Continuum Advantage
Leverage the power of our packet capture solution whenever and wherever you need it
find the right subscription plan with
our FAQs, quick start guide, or CONTACT US TODAY
Continuum Advantage is a subscription plan that gives you access to NextComputing’s powerful packet capture software on the qualifying system of your choice. Whether you need the tools on a temporary or ongoing basis, on-site or off, Continuum Advantage lets you build the right cyber analytics tool to match your workflow.
| Subscription |
Price |
Description |
|---|---|---|
| Monthly |
$750/month |
Start using Continuum Advantage at $250 for the first month ($500/month thereafter, auto-renewed) |
| 3-Month |
$1500/3 months |
3 month pre-paid subscription, auto-renewed every three months |
| Yearly |
$3750/12 months |
12 month pre-paid subscription, auto-renewed every year |
Key Software Subscription Features
Extensive Functionality
Continuum Advantage support various workflows for NOC or SOC use on a subscription use basis on the qualifying hardware platform of your choice.
LOSSLESS CAPTURE and ACTIVE RSYNC TO EXISTING PCAP REPOSITORIES
The subscription supports use for continuous lossless packet capture on (1) or (2) capture interfaces via tap or span port up to 10Gbps aggregate depending on the qualifying hardware platform of your choice
Click here to view hardware requirements
Additionally the Continuum Advantage has an active connection Rsync that can connect to your host server directories where existing PCAP and PCAP-NG file repository exists to copy and ingest and process same as capture packets for analysis, search and review. (1) active Rsync interface and (1) passive packet capture interface can be supported at one time.
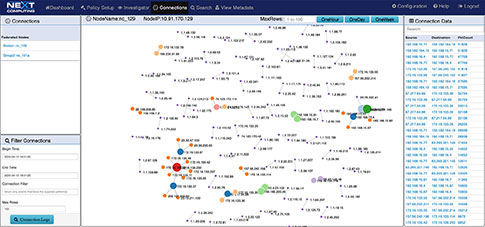
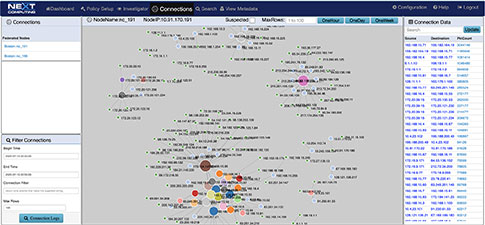
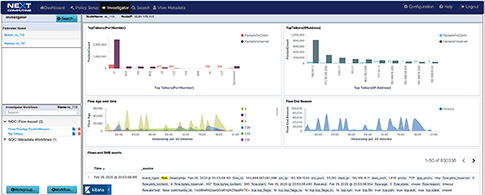
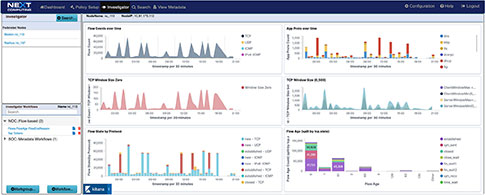
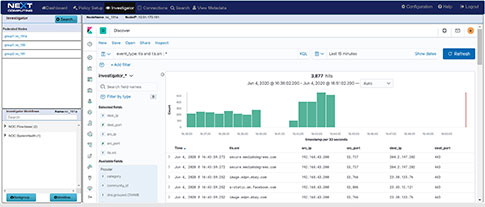
VISUALIZATION AND SIMULTANEOUS SEARCH
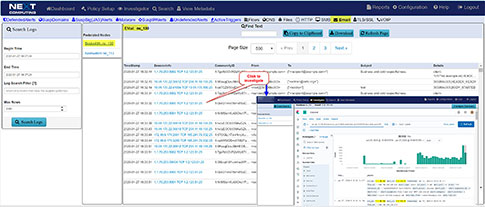
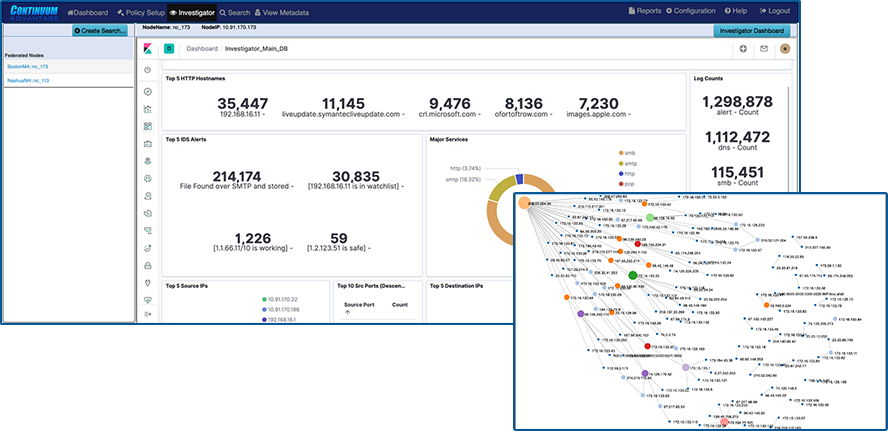
The investigator allows you to view NetFlow, and enriched meta data logs, and threat signatures in our visualization tool, and pivot to a follow the stream and packet view from an event within the dashboard
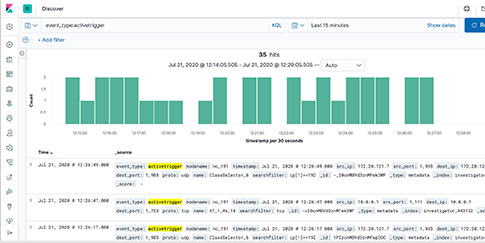
SOC and THREAT MONITORING WITH ACTIVE TRIGGERS, SURICATA FORMAT SIGNATURES, SUSPICOUS JA3, SUSPICIOUS DOMAINS and OTHER EVENT MATCHING
Use real-time, dynamic, user-defined SOC workflow related analytics to rapidly review of behavior and anomalies and pivot to concurrent search workflows to follow the stream, event and view packets
NOC and NETWORK PERFORMANCE RELATED ACTIVITY MONITORING
RFC anomaly logging, file download event logging, multi-protocol event / metadata logging including HTTP, files, DNS, email, user agents, NetFlow, TLS/SSL, and VOIP concurrent search workflows to follow the stream, event and view packets
WEB GUI for VISUALIZATION AND REST API FOR AUTOMATION
Continuum Advantage’s interactive dashboard drives your investigation workflow as well as over the REST interface
SUPPORT and SOFTWARE UPDATES
During the term of your subscription, software updates are provided when available and support is available via phone, email, or our online ticket system including assistance with workflows. Specific REST API automation scripts can be implemented as an additional for fee service.
Continuum Advantage Workflows
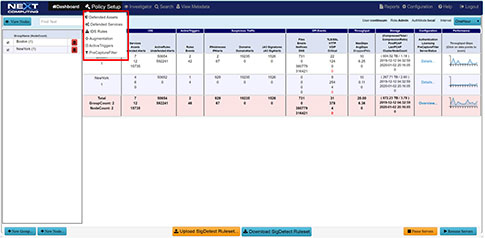
Network Topology View Augmented by Suspected IP Address View

DSCP Network Performance Metrics Investigation/Search Workflow

TLS-SNI Pivot Workflow

Suspicious Traffic Workflow
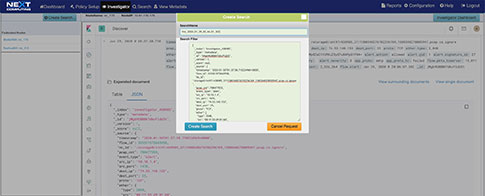
Packet Continuum's DPI Engine and Augmentation pipeline ensures that metadata associated with suspicious traffic are identified and tagged.
This sequence explains the workflow from defining policies to identify suspicious traffic to the display of the metadata events tagged as suspicious traffic.
There are 4 types of augmentation policy data that can be provided to the Augmentation server:
- Suspicious TLS/SSL Signatures
- Suspicious IP Addresses
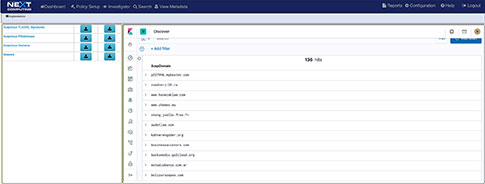
- Suspicious Domains
- Malware
The Augmentation tab allows users to upload additional data that can be used to enhance the value of stored data and allow data correlation. This workflow explains adding a watchlist and investigating the suspicious traffic for further analysis.

Continuum Advantage Open Data Access
Packet Capture and Rsync Features
Continuous lossless packet capture up to 10Gbps aggregate depending on your system configuration into a rolling FIFO Capture Store from (1) or (2) span port or taps
Optionally ingest existing PCAP and PCAP-NG files on your host server via our active connection Rsync feature
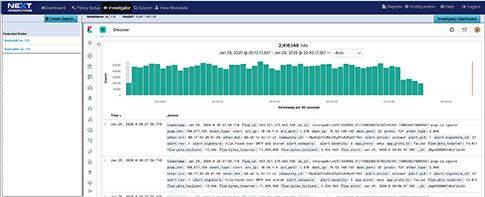
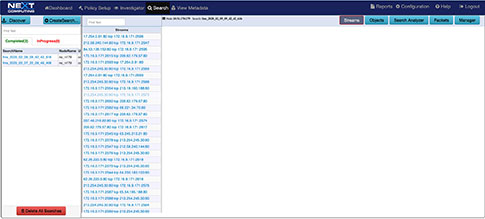
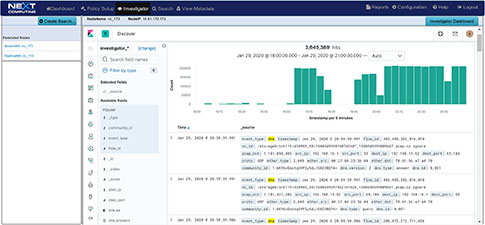
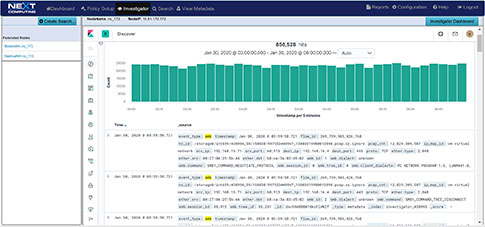
Simultaneously Searchable netflow, enriched application meta data, threat alerts, and packets thru our Web GUI Investigator and packet viewer (See workflow examples
Real time indexing and suspicious threat and suricata rule based signature alerting — with time stamping as low as 150 nanoseconds -
Dedicated onboard Extraction Store retains all search query results viewable in our UI or downloadable for further analysis in your analytics tool of choice
Options for PCAP (or NetFlow) search results:
- View in Wireshark on the local display UI
- Remotely access from an external host via Web GUI or REST/API scripting
- Run the critical sessions over the Streaming Playback Interface to any 3rd party forensic analysis tool. Simply connect streaming playback output to the capture interface of your tool, just like a span/mirror port.
STANDARDS-BASED POLICIES, WITH OPEN DATA ACCESS
Open Source Rulesets & Data Interfaces for NOC and SOC use case workflows:
- Integrated Suricata IDS — alert rulesets for signature based threat alerting- Up to 50,000 simultaneous rules-changeable via UI or RESTAPI
- Web UI investigator with Kibana flexible workflow screens – open data visualization of enriched meta data and intelligence data
- JA3 – TLS/SSL encrypted traffic signatures and matching to uploaded known suspicious JA3 signatures
- MD5 – File signatures and File Malware signatures matching to uploaded known malware MD5 hashes with search feature (and with active traffic when running 1Gbps or Rsync in a 5Gbps hardware configurion and 5Gbps in a 10Gbps hardware configuration
Above 5Gbs only supported with session search not on all incoming traffic. BPF Active Triggers— Define a single BPF pre-capture filter and up to 10 BPF passive filted for BPF signature events to alert on Suspicious Domains and DNS Alerts & Augmentation to uploaded known suspicious Domains and DNS Defended Assets/Services — Define your list of known or internal IP addresses and ports (Services) that you want to defend or do network analysis on Topology of IP conection discovery — Auto discover muli level IP conection and indirect connection of network traffic to investigate for NOC and SOC use case purposes
PCAP-NG for packet data off load from search for further analysis NetFlow Version 9 flow records for off load from search for further analysis JSON and Text/CSV/syslog network enrichment data for off lead from search for further analysis
Web UI (Chrome and FireFox) Simplified URL-based actions, via a full-featured, mature REST/API to pivot from Splunk, Cisco watch, Corelight, Zeek, IBM Security QRadar and range of other tools Unix Command Line Interface (CLI) Custom Workflow Scripting 3rd Party Event/Data/PCAP Correlation including Zeek/Corelight Community ID Role-Based Access Control
Continuum Advantage Capture Process
- Continuous lossless packet capture up to 10Gbps into a rolling FIFO capture store. A separate extraction store retains PCAP file query results.
- 4-tuple indexing in real time — IP address source/destination, port source/destination — with time stamping as low as 150 nanoseconds
- PCAP compression in real time — Overall storage amplification up to 20x (depending on % of captured traffic that is SSL or video)
- Search PCAP data from a convenient web GUI, using easy BPF+ descriptors, immediately streaming the results from capture store to persistent extraction store.
RSYNC to existing PCAPs
In addition to lossless capture via tap or span port, the Continuum Advantage also has the ability to have an active connection to any systems that have existing PCAP or PCAP-NG files
-
Ingesting PCAP and PCAP-NG files from remote systems via Rsync command retaining the original timestamps.
-
This is in addition to capturing data off a separate live network interface.
-
Our Rsync feature recursively copies from your source system directory(s) into the Continuum Advantage system
-
Rsync User – username used for access to the source system. Must be a valid Linux user and organizes, indexes, generated enriched metadata, as well processing against signature or other threat alerts for analysis and search same as the lossless packet capture
-
Configurations support (1) Rsync interface on the source system and/or (1) lossless packet capture interface from a span port or (2) lossless packet capture interface from span or tap ports.
-
An Rsync as an active network interface connection to your source computer or server where the existing PCAPs reside.
Hardware Configurations and Performance
All Configurations
- Bare Metal installation of CentOS 7.9 or RedHat 7.9
- AMD processors are most optimal if you have a choice (AMD EPYC 16 , 32 or 64 cores)
lossless capture rates from span or tap ports
based on system configurations
|
Up to 1Gbps |
Up to 5Gbps |
Up to 10Gbps |
|
| CPU |
16-core processor+ (with BIOS set to hyperthreading) Processors can be AMD EPYC, Ryzen, Threadripper or Intel Core i7, Core i9, or single Socket Xeon or Xeon Scalable Processor |
22-cores+ processor(s) (with BIOS set to hyperthreading) Processors can be AMD EPYC 24, 32 or 64 Core, Threadripper or single or dual socket Xeon or Xeon Scalable Processor(s) |
44-cores total processor(s) (with BIOS set to hyperthreading) Processors can be AMD EPYC 64 Core, Threadripper or single or dual socket Xeon or Xeon Scalable Processor(s) |
| RAM |
128 GB+ |
196 GB+ |
256 GB+ |
| OS Drive |
Minimum 500GB+ (JBOD or RAID 1) |
||
| Network Interface |
|
||
| Capture store for PCAP, enriched metadata and search extraction store |
|
|
|
Need More?
NextComputing also offers complete hardware and software solutions that provide maximum capture rates, storage, and expandability to match your high-demand workflow. If you need enterprise-class performance or custom workflows, consider what our Packet Continuum solutions have to offer:
- More connections: Up to 4 capture interfaces
- Beyond 10G: Packet Continuum supports 1G, 10G, 25G, 40G, 100G capture NIC interfaces
- Expand your enterprise: Packet Continuum supports up to 100 federations with up to 100 capture nodes in a federation group
- Expand performance: Packet Continuum supports up to 8 cluster processing/storage nodes per capture node
- Maximum storage: Packet Continuum is to 10 PB or more with federation and clustering