Suspicious Traffic Workflow
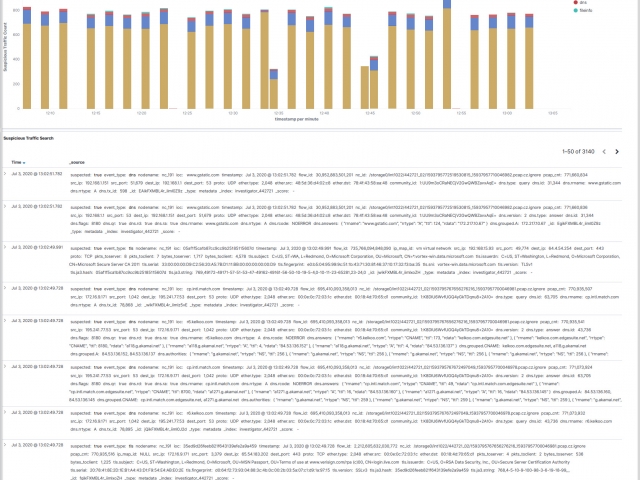
Packet Continuum's DPI Engine and Augmentation pipeline ensures that metadata associated with suspicious traffic are identified and tagged.
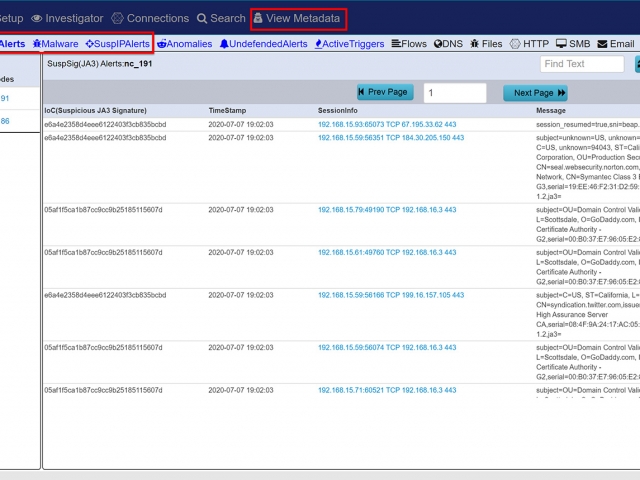
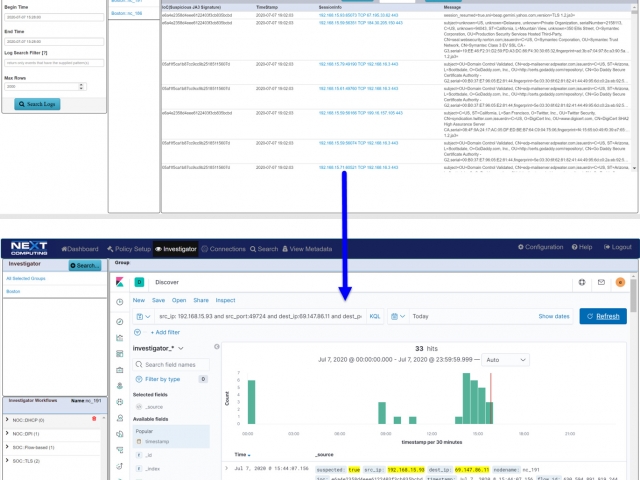
This sequence explains the workflow from defining policies to identify suspicious traffic to the display of the metadata events tagged as suspicious traffic.
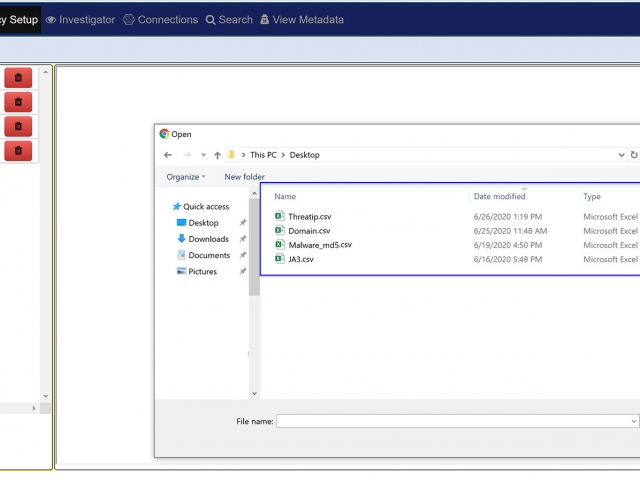
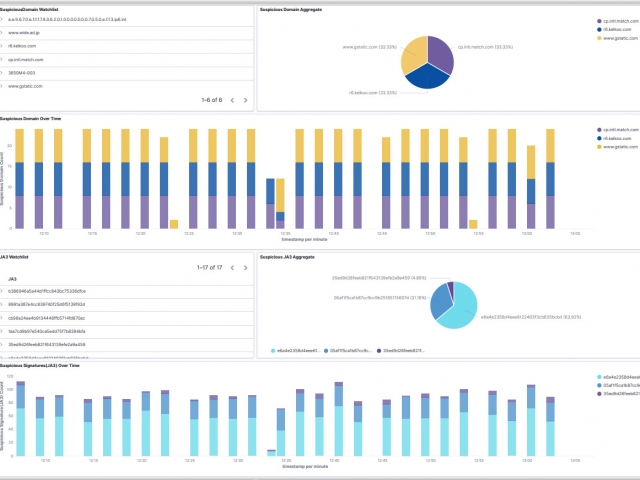
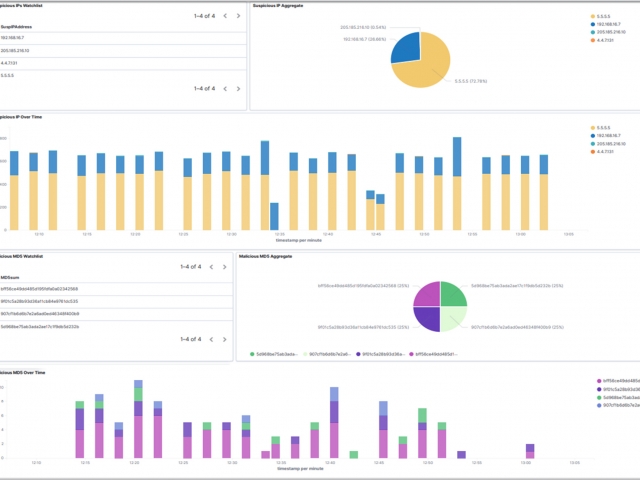
There are 4 types of augmentation policy data that can be provided to the Augmentation server:
- Suspicious TLS/SSL Signatures
- Suspicious IP Addresses
- Suspicious Domains
- Malware
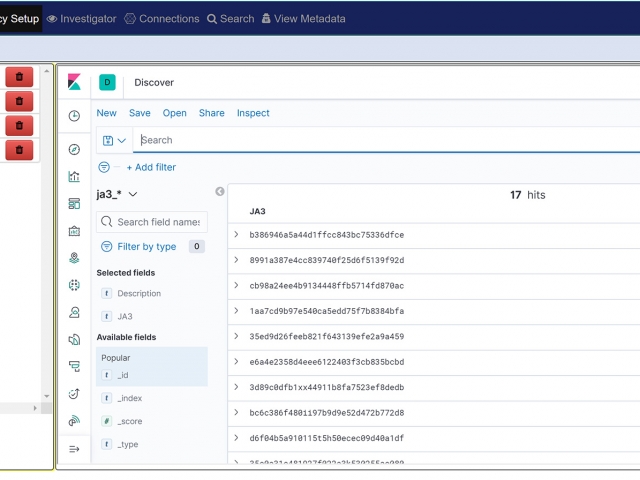
The Augmentation tab allows users to upload additional data that can be used to enhance the value of stored data and allow data correlation. This workflow explains adding a watchlist and investigating the suspicious traffic for further analysis.