FLy-Away Kits
Complete Solutions for Cyber Operations,
Transportable Private Cloud, Edge Computing
A Fly-Away Kit (FAK) or Expeditionary Kit is a self-contained suite of equipment (hardware and software) for DoD and federal civilian Cyber Protection Teams (CPTs) and forward operations to operate both in tactical (field-deployed) and back-office environments. The FAK suite of cyber tools or cloud/server applications include tools to conduct vulnerability analysis, incident response, and other cyber-analytic functions, and are suitable for operation on both classified and unclassified networks.
In order to determine the state of the critical networks or to run a deployable network, cyber teams, IT infrastructure teams, and data analytics teams require:
- Network data from sensors which are deployable servers
- Analytic capability from the hardware and software
- A user interface typically via their laptops
NextComputing Fly-Away Kits can support a wide variety of user-supplied software modules, including Government Off-the-Shelf (GOTS), Commercial Off-the-Shelf (COTS), and free and open-source software (FOSS).
Fly-Away Kit (FAK) for cyber operations
Standard Fly-Away Kit Configurations
In addition to FAKs customized to meet your specific needs, NextComputing also provides a set of standard FAK configurations, including appropriate hardware accessories and commercial / FOSS software tools:
- Packet Capture Network Sensor Kit
- Lossless packet capture with real-time DPI packet analytics, Suricata IDS alerting and very fast “federated” PCAP search. Used for network threat-hunting and Incident Response forensic investigations.
- (1) TSA-compliant transit case for the appliance
- Pen Test Fly-Away Kit
- For network/host monitoring for cyber defense, including threat-hunting (both network and end-point), vulnerability assessment, packet capture with PCAP network forensics
- (1) TSA-compliant appliance case + (1) accessories case
- Malware & Digital Forensics Fly-Away Kit
- For analysis of file-based malware, including data/file extraction from external devices, drives and cell-phones
- (1) TSA-compliant appliance case + (1) accessories case
- Optional: workflow with separate Packet Capture Sensor Kit, for real-time file-carving into Sandbox application
- SCADA/OT Fly-Away Kit
- For analysis of Supervisory Control and Data Acquisition (SCADA) and Field Operational Technology (OT) systems for protection of critical infrastructure.
- (1) TSA-compliant appliance case + (1) accessories case
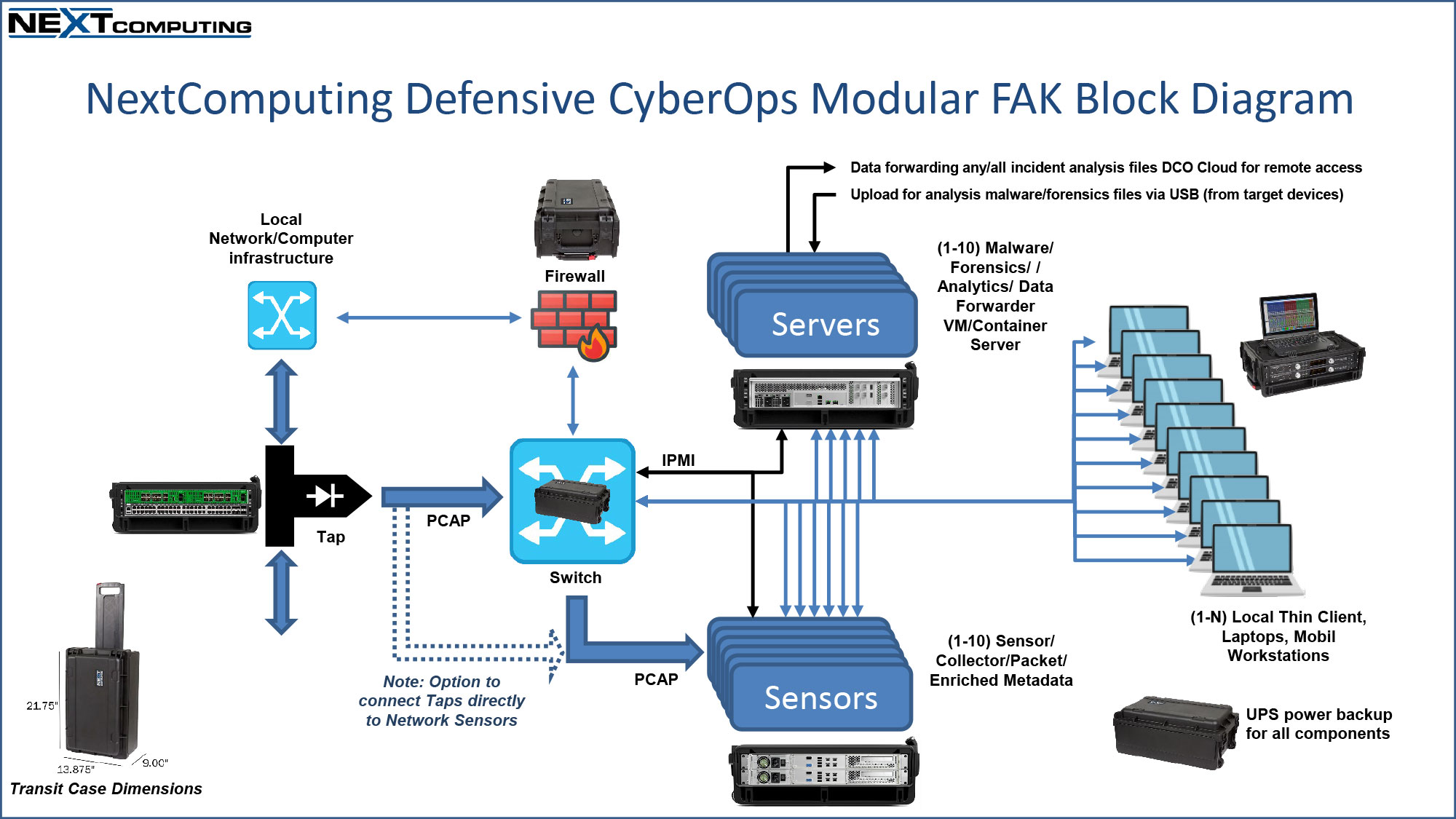
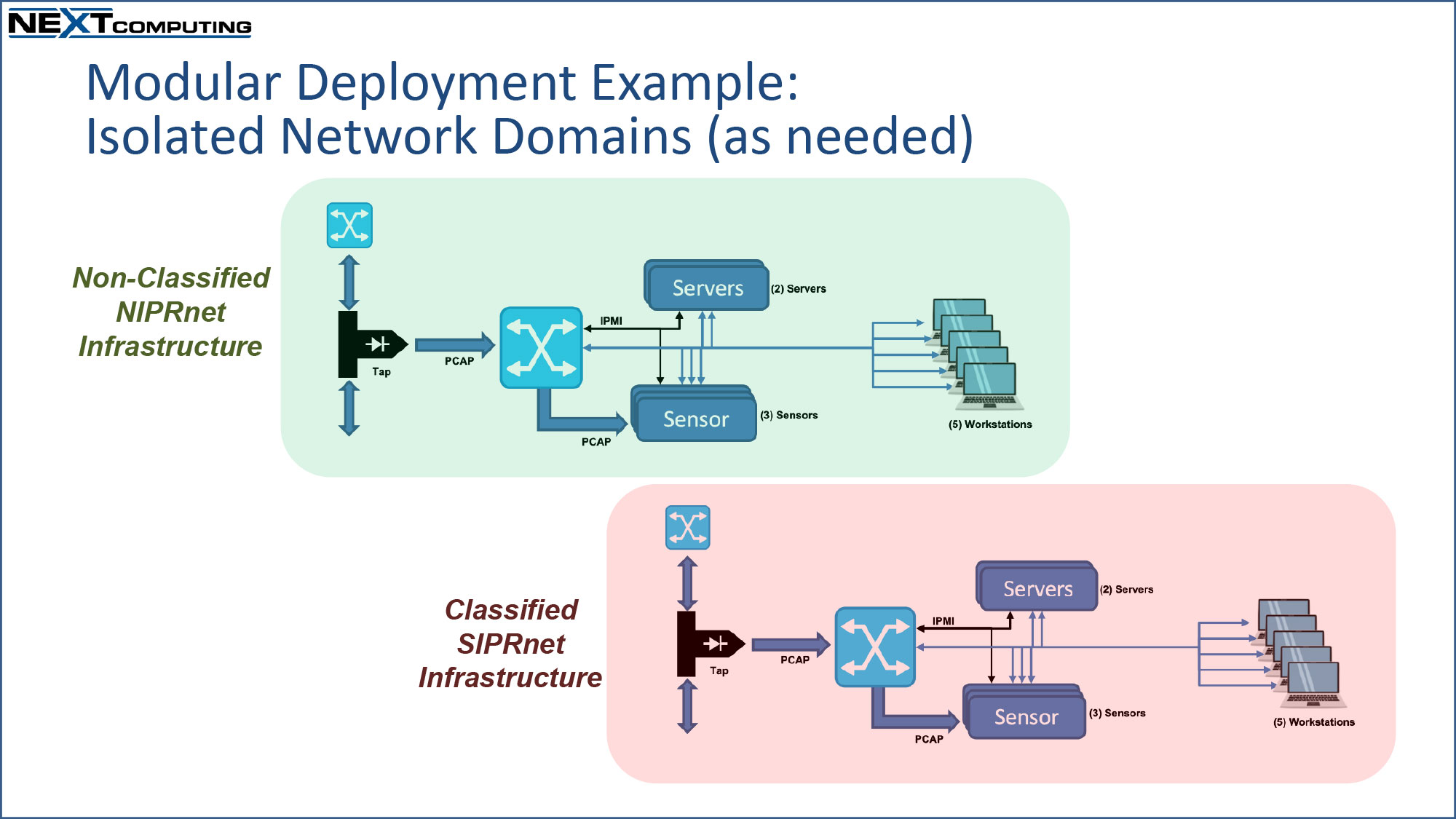
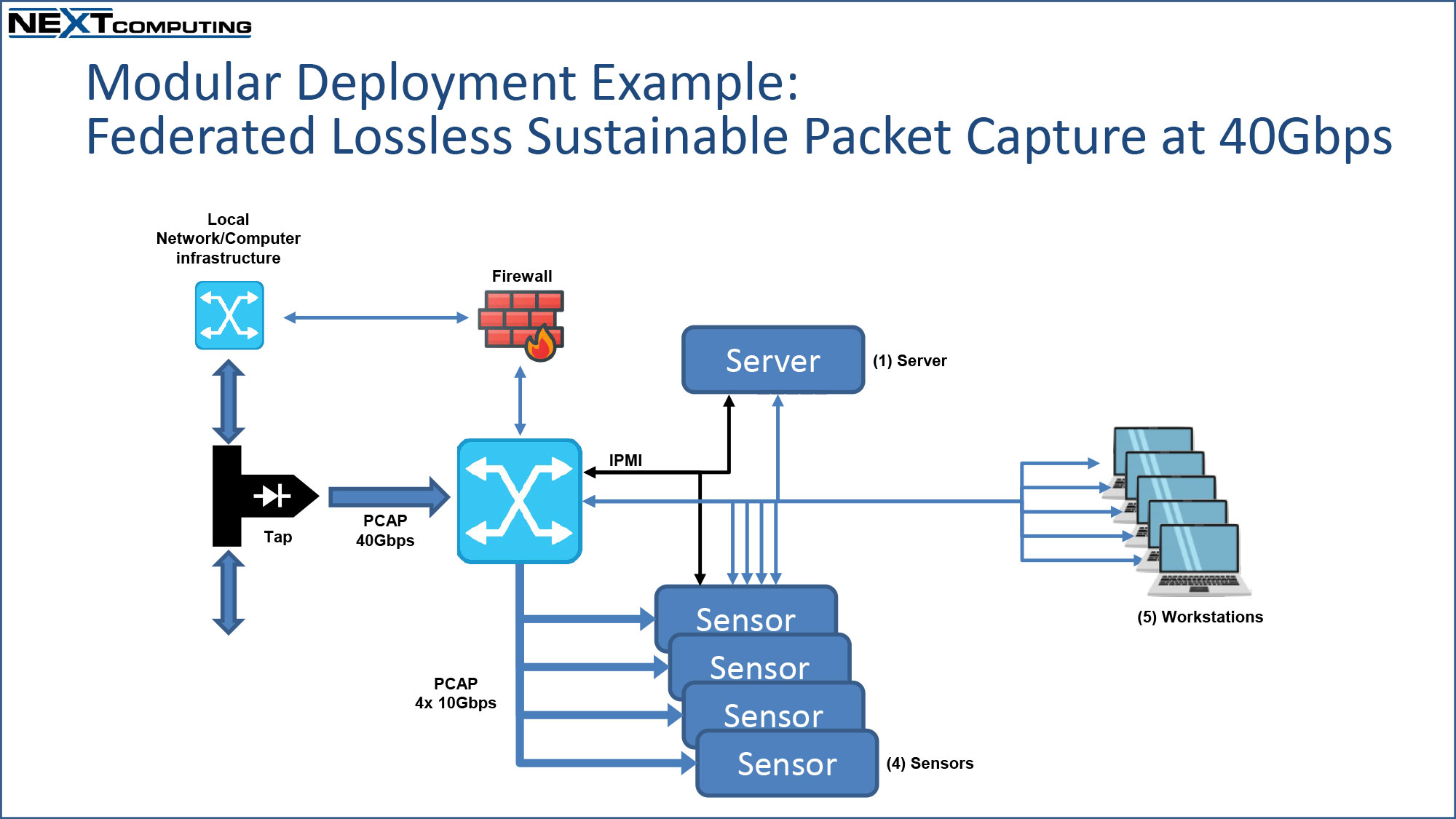
- Modular Defensive Cyber Operations Fly-Away Kit
- For deployment of full-scale CPT operations, including multiple Sensors, Operator Workstations, Servers, Tap/Aggregator, Switch, Firewall, deployable UPS
- Multiple TSA-compliant transit cases, for modular deployment & re-configuration – see diagram examples below
Powerful AI-Based Data Solutions at the Network Edge
When it comes to leveraging AI and machine learning for FAK solutions, NextComputing offers industry-leading hardware and capabilities. The NVIDIA RTX 4000 SFF Ada Generation GPU is a natural fit for these kits as it's designed for professionals who demand performance but without the footprint of full sized workstations.
Our 2U server-based fly-away kit supports up to 3 RTX 4000 SFF GPUs, each individual GPU offers 20GB GDDR6 memory, 6,144 CUDA Cores, and 192 Tensor Cores for outstanding performance in using AI to manage datasets.

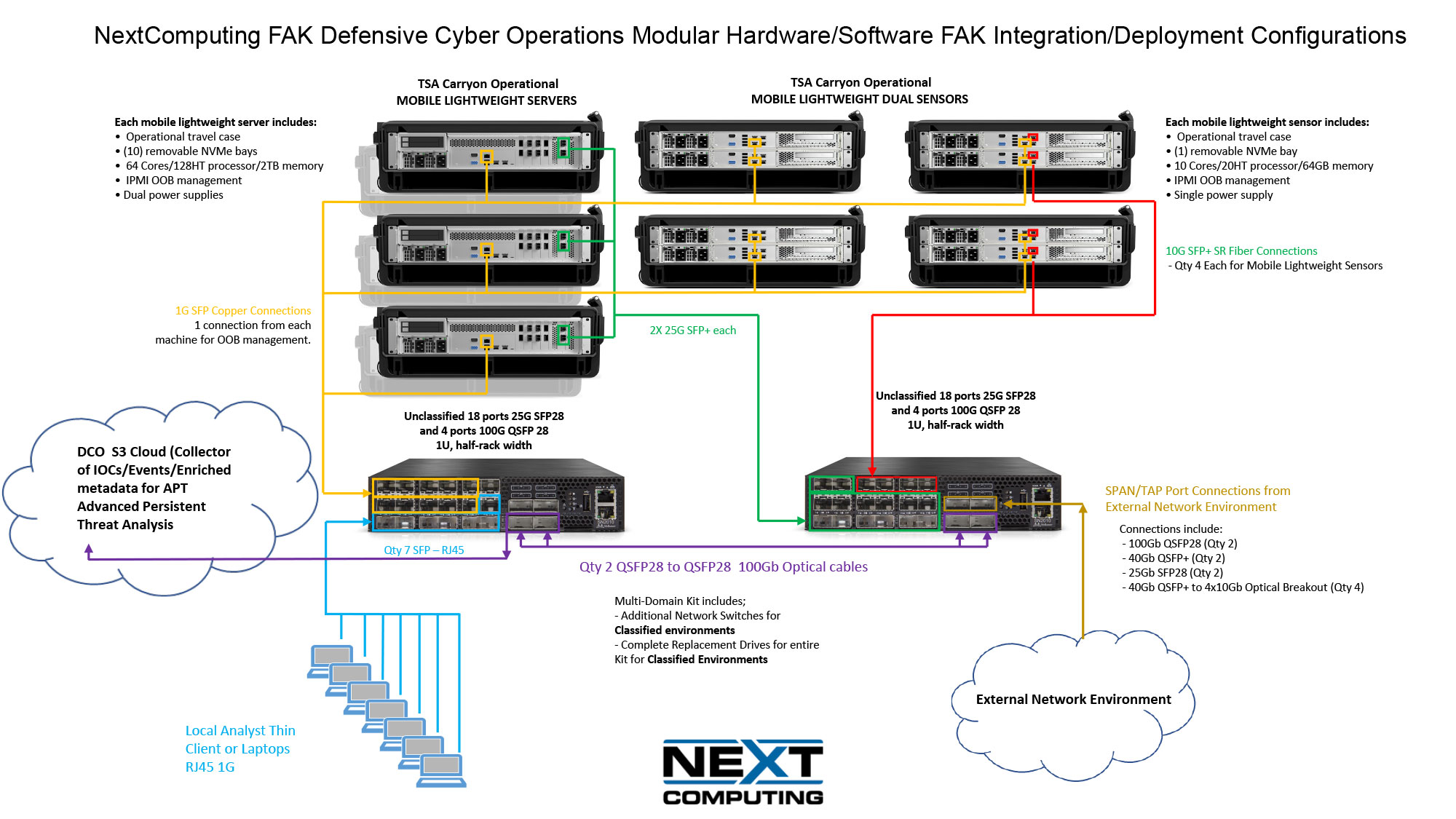
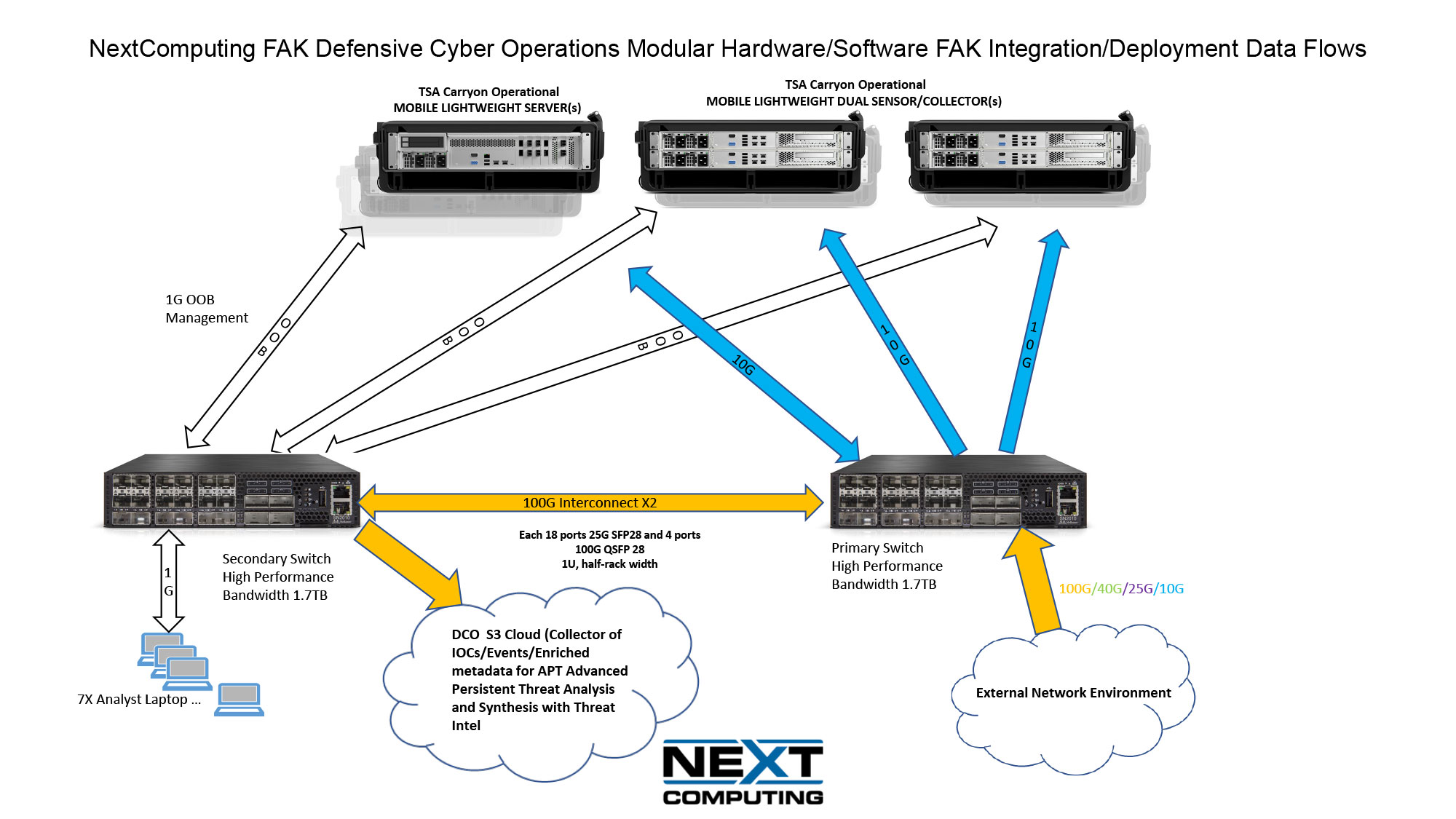
Defensive Cyber Operations Modular Hardware/Software FAK Integration/Deployment Configurations
Fly-Away Kit Objectives
What it does
- Enable a Rapid Response by more agile CPT teams. More easily scale up and scale down travelling teams to meet the mission. Be able to respond at a moment’s notice, and not have to carefully schedule C130 or other travel assets
- Single person lift
- Carry-on commercial aircraft, staying close to the analyst
- Easily transport on rental car or sedan, SUV cross over vehicles (rental)
- Make travel less conspicuous by carrying smaller items
- Reduce operation costs. Simplify procurement with pre-configured Fly-Away Kits as a single part#s.
- Reduce travel costs by leveraging commercial travel options
- Reduce setup time & tear down time
- Reduce size, so less space used on the site/location. Expand the potential sites where space is a constraint
Pain Points
Legacy FAK tools have been too large, consist of too many components and peripherals, and are vulnerable to shock damage. In addition, the lack of modularity of legacy tools do not allow the flexibility to support various missions and subordinate commands simultaneously. Legacy tools have been costly and complex to use.
In particular, large rack servers, in large transport cases are:
- Not agile. Transport has to be carefully planned and scheduled, subject to delays.
- Expensive to transport
- Subject to damage
- Subject to separation of critical data & equipment from the CPT teams
- 3-4+ person lift
- Large, bulky, takes up a lot of space. Cannot go to certain locations based on size/weight.
- Cannot easily transport on commercial airline, or via car or standard vehicles
- Complex to setup & complex to tear down
- Not easily configurable
Solutions
There is a critical need for less expensive tools where personnel can engage quickly with minimal training. The ideal cyber Fly-Away Kit provides a lighter, smaller, shock-tolerant, faster and more capable suite than the current legacy tools in use today.
This is why NextComputing solutions are built with compact, cutting-edge hardware and configured to meet your needs. From systems to cases to accessories, our Fly-Away Kits offer you an all-inclusive mobile toolset that allows you to get started quickly, anywhere you need to be.
Systems
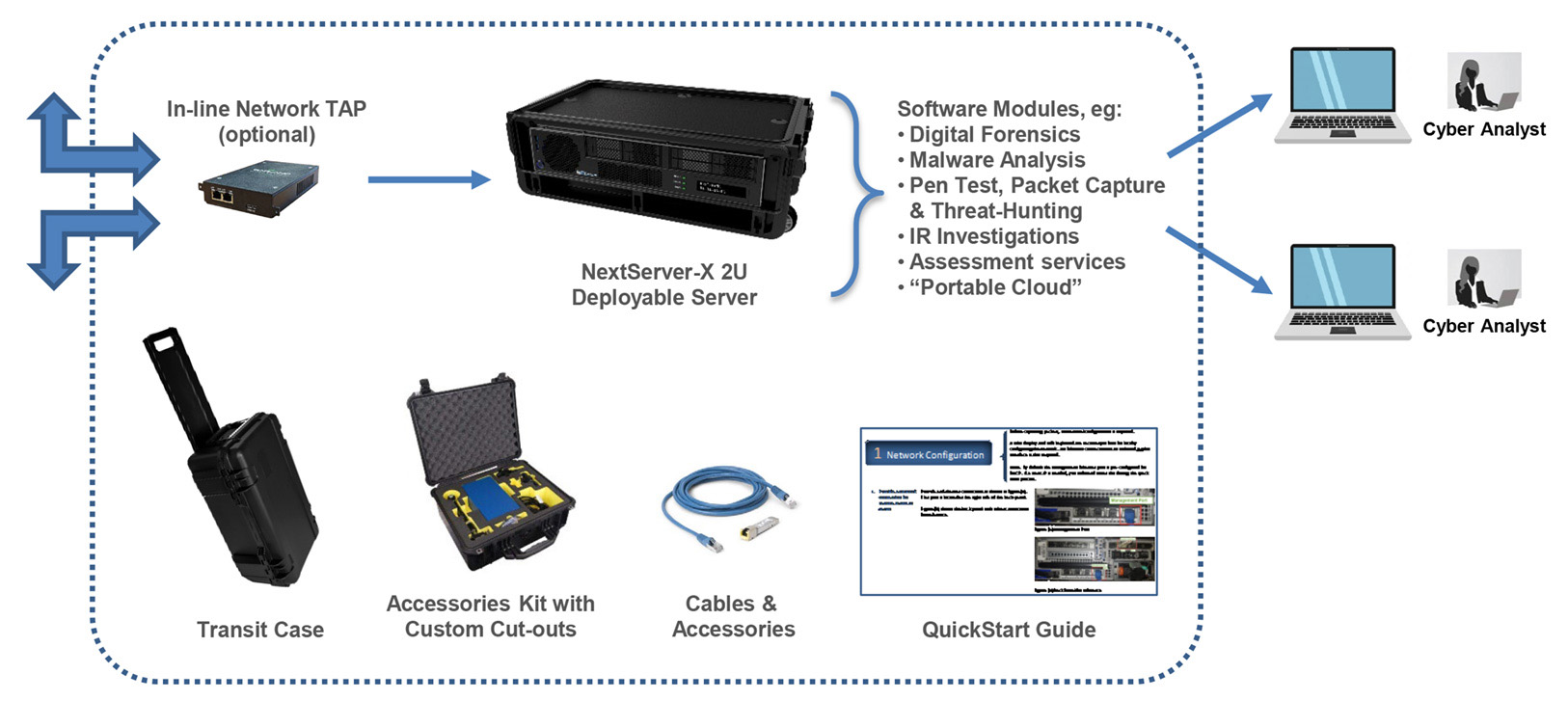
NextServer-X 2U
- Compact form factor: Maximum performance in minimum space
- Easy, rugged transport: Operate the system from within the rugged travel case for quick setup anywhere.
- High-performance server: Ideal for cyber analytics, data analytics, network forensics and data recording at the network edge
- Flexibility to meet your requirements: Single or dual 2U system configurations in a TSA-compliant carry-on case.

NextServer-X 1U
- Compact form factor: High-density 1U server / sensor.
- Easy, rugged transport: Operate (1) or (2) systems from within the rugged travel case for quick setup anywhere.
- High-performance server: Ideal for cyber analytics, data analytics, network forensics and data recording at the network edge
- Flexibility to meet your requirements: Configurations available with 2 or 4 1U system configurations in a TSA-compliant carry-on case.

NextServer-X
- Smallest form factor, highest performance: as a desktop system or short-depth rack mount
- Easily transportable: System and hard case combined are less than 35lbs for single-person lift and TSA compliant carry-on
- Modular and purpose-built: For your high performance computing use case
- As a high-performance server: Ideal for cyber analytics, data analytics, network forensics and data recording
- As a high-performance workstation: Ideal for rendering and scientific simulation

Network Tap
- Portable form factor: TSA Compliant case featuring equipment supporting 10M/100M/1Gigabit/10Gigabit/25Gigabit & 40Gigabit
- High-density configuration: Each 1U system holds up to 24 LC TAP Modules, 16 MPO/MTP TAP Modules, 16 BiDi LC TAP Modules
- SelectTAP: Fiber Single Passive Tap Module for FMC-1U: Single-Mode Fiber 9 micron OS1/OS2, 1310/1550nm dual wavelengths, 50/50
- SelectTAP FMC: Single Tap Module : Multi-Mode Fiber 50 micron OM3/OM4 Optimized, 850nm Wavelength, 50/50
- MM Passive Fiber TAP-Single Tap: 40GSR4/100GSR4 MM Fiber 50 micron Laser-Optimized OM3/OM4 Design, 850nm, 50/50, MTP12 B Style Male Connectors (MPO12)
- Contact NextComputing to Learn More

Network Aggregator
- Portable form factor: TSA Compliant case featuring Copper Portable 10/100/1000M TAP: (2) Copper 10/100/1000M RJ-45 Tap Ports with (2) Copper 1000M RJ-45 Monitoring Ports, 1 Power Supply
- PacketMAX: Advanced Aggregator, (20) SFP+ 1/10G Ports, Managed, AC power supply
- SFP+ Dual Speed 1Gigabit-LX / 10Gigabit-LR Single Mode Fiber LC Connector, TAA Compliant
- SFP+ Dual Speed 1Gigabit-SX / 10Gigabit-SR Multi-Mode Fiber LC Connector, TAA Compliant
- SFP 10/100/1000 Copper RJ-45 Connector, TAA Compliant
- PacketMAX: Advanced Feature (4) SFP+ 1G/10G Ports: De-duplication, managed, AC Power
- Contact NextComputing to Learn More

Radius EDS
- Portable form factor: Briefcase-like form factor and integrated 17.3″ Full HD display, with optional resistive touchscreen
- High-Performance: Workstation-class Intel and AMD processors, high-speed memory, and full-size PCIe expansion
- Massive storage: Up to 16 easy-access removable SSDs with RAID options; utilizing the latest high-performance NVMe and traditional SSD storage
- PCI Express expansion: Up to (7) PCI Express expansion slots for full-size cards

NextComputing Kit Features
Available configurations include:
- Packet capture software: (packetcontinuum.nextcomputing.com/) Packet Continuum Suricata, PCAP, Elastic software suite) or open suite tools (ELK, Zeek, Suricata, PCAP) at 10+ Gbps
- Malware Suite software and hardware: NextComputing Malware software stack/ VM suite of tools and collection hardware kit (in separate TSA carryon case)
- Forensics Suite software and hardware: NextComputing Forensics software stack/ VM suite of tools and collection hardware kit (in separate TSA carryon case)
- Pentest Suite software and hardware: NextComputing Pentest software stack/ VM suite of tools and collection hardware kit (in separate TSA carryon case)
- Deployable Network tap/aggregator: Separate system options for Network tap/aggregators in our operational TSA carryon hardcase
- Deployable Network Switch: Separate system options for 100Gbps Network Switch in our operational TSA carryon hardcase
- Mobile Workstations: Separate system options for thin client laptops or full client mobile workstations
Optional Network TAP:
- Passive regenerative network TAPs
- Supports copper media type, fiber media type, with a minimum of (4) SFP interfaces
- Supports network speeds from 1Gbps for copper and 1/10/40/100Gbps for fiber
- Dual internal AC power
- Duplicate all network traffic (not replication), eg. passes physical errors
- Supports up to (4) physical TAP modules that are fully configurable and interchangeable
- 100% secure and invisible (no IP or MAC addresses)
Deployable Server – Physical:
- Many configurations fit into overhead storage bin of commercial airlines (TSA-compliant)
- Deployable server hardware is physically modular, with other components capable of being added to increase storage and/or performance capabilities
- Deployable server hardware is also rack-mountable front or back (or both), with removable “ears”
- Systems are capable of meeting all operational requirements in temperatures ranging from 40 °F to 95°F
- Deployable server hardware, in its transport configuration, withstands typical-use vibration tests and drop-tests
Deployable Server – Performance and Modularity:
- Powerful Intel or AMD processors (single or dual)
- Multiple RAID and HBA configuration options
- No-tools removable storage
- High performance sustained reads and writes per NVMe SSD up to 3500MB/Sec
- Up to 1TB of RAM up to 3200MHz
- Multiple USB 3.1 or better Type-A ports
- PCI Express 3.0 and 4.0 expansion slots
- Both 110-220v AC 50/60Hz power
- Secure Boot UEFI compliant BIOS, Boot Guard, TPM2.0
- Remote management: IPMI, HTML5 and API based out of band management with MAC addresses identification, one time boot on next reboot option, PXE boot option, Redfish compatible Out of Band (OBB) management connection
- Certified for CentOS, Red Hat Enterprise Linux, VMware vSphere, various other type 2 hypervisors, Windows 2019 server, Windows 11, and deployable cloud infrastructure https://solutions.nextcomputing.com/operating-systems/
- Supports various virtualization options including Red Hat, CentOS, and vSphere hypervisor https://solutions.nextcomputing.com/operating-systems/
- Modular design allows upgrades for additional PCI Express cards
- Modular design allows for expansion via additional Plugin RAID controller and carrier/module kit (sold separately) for up to an additional (8) 12G SAS/6G SATA SSDs in JBOD/RAID 0/5/6. Each server is provisioned already standard with the drive cage and (8) slot 12G SAS/6G SATA mid-plane/receiver
- Modular design allows for addition of 25G,40G, 100G network cards or additional 1G/10G Network cards
- Modular design allows for ease of service, and upgrade and change in configuration options
Transit cases.
- Deployable server hardware and transit cases may be customized with markings:
- private-label logos
- labels that identify the weight and number of persons required to lift the object.
- marked in accordance with MIL-STD-130N (Identification Markings of US Military Property).
- Transit cases include custom cutouts for optional components, as needed.
- Laptops - multiple laptops will be required per Deployable server
- Cables, power strips, tools, etc
- Battery backup module
- Quick-start documentation

Other FAK Services.
NOTE: These option services can potentially reduce engineering and support costs for customer operations teams:
- Package custom FAK configurations as single-SKU unique part#s, for convenient procurement and future support under revision control by part#
- Engineering services to design/review a complete suite of hardware and software components to meet specific mission requirements
- Deliver fully assembled FAKs, including a “QuickStart Guide” document for users
- Transit cases: Customized cutout inserts. Private labeling and/or special marks & stenciling
- Software: Install & configure software, eg ESXi virtualization
- Hardware: Setup required for devices (servers, switches and laptop clients)
- Configuration control management, so ordering the same part# again means the exact same thing is delivered each time, eg with rev# changes as components require upgrade
- Support services, like policies to assure all software components are updated to the latest release
- Engineering future versions, upgrades or variations, eg as additional SKUs and part#s
- We also provide unique “Mission Management” logistics and refresh services, where we manage/maintain an inventory pool of FAKs or mobile appliances, with quick-turn refresh, repair & drop-ship to the next client engagement.
- Click here to learn more about NextComputing OEM solutions
Software
- Deployable servers and laptops all support virtualized software modules
- These software capabilities are often utilized for cyber protection operations:
- Network Mapping Software
- Incident Response Software to include
- full disk image capture
- memory capture
- forensic analysis.
- Network traffic ingestion and analysis capabilities that takes advantage of
- full packet capture
- offloading and analysis
- metadata creation for use by other tools.
- Host agent and log collection for collection of data from remotely installed agents.
- Vulnerability scanners
- Malware analysis sandbox capability
- Cyber software development experience/capabilities.
- NextComputing has extensive experience working with customer-developed or 3rd-party software. Typically the challenge is how to optimize performance, when a 3rd party application which is developed for standard data centers servers, is now deployed on NextComputing small form-factor hardware platform like NextServer-X, within difficult use cases like mobile field deployment with frequent operational challenges like power insecurity, frequent restarts, and high-speed/constant-use disk storage. Sharing only run-time object code, NextComputing has unique expertise to tune bottlenecks by adjusting BIOS settings, RAID configurations, NIC card utilization. We can make adjustments to open source code and track any changes. When appropriate, we offer suggestions for making adjustments to code developed by customers and 3rd parties.
- NextComputing has unique experience developing software for lossless packet capture and real-time DPI packet analytics. This began when our hardware OEM customers requested that we optimize a modular packet capture software framework with a critical requirement: no packet loss, within deterministic performance specifications for maximum sustainable capture rate, even with simultaneous operations for up to 50,000 active Suricata IDS rulesets, and fast PCAP search by multiple user-analysts. For this important use case, NextComputing developed the Packet Continuum / CyberPro packet capture software framework, which runs native on any common hardware platform, scales to enterprise or carrier-grade networks with a unique Federation Manager software feature, and provides a mature and well-documented REST/API interface for automation, scripting, and easy integration with 3rd party cyber solutions.
- NextComputing is committed to supporting open data access, standard data interchange formats, open API integrations with 3rd parties. We particularly wish to support the aspirations of open source communities, with use of common syntax and interfaces used by open source packages in common use. For example, Wireshark, Suricata and Zeek are examples of open source packages that have difficulty performing at enterprise scale, with problems like packet loss or unpredictable behavior. Packet Continuum provides a clear deterministic performance while using open/common file formats & syntax.
- Open source applications integration/optimization, including the ability to integrate/optimize existing DCO applications (e.g DoD customers with open source code bundles they may want to reuse)
- Many customers have long experience working with various open source packages for cyber operations. NextComputing is eager to assist customers by integrating customer-specific combinations of open source packages, and optimizing performance while minimizing the cost of the underlying hardware platform needed to sustain that performance. For example, we many government DCO customers have long history with open source packages with valuable packet capture, real-time DPI analytics, IDS alerting and scripting capabilities. NextComputing can take these user-defined solutions and optimize a deployable hardware platform for exactly that set of open source solutions — and provide ongoing revision control and configuration management for that specific bundle.
- Configuration management capability
- NextComputing engineering services for Software and Fly-Away Kit integration include initial specification of software tools and hardware accessories, creation of useful Quickstart Guides for inclusion within each FAK, precise revision tracking of the specified FAK components, consistent QA & regression testing, and regular software patch updates for all included software. Logistics services provide quick turnaround for any legacy FAK appliance taken from a field mission, to refresh the hardware and bring all software to the most recent version, then QA/regression test, and ready for stock or drop-ship to the next field mission. NextComputing has partners with cleared personnel and restricted facilities and who can provide these logistics services to DoD cyber operations and other government customers.
- Air-gap updates/support enhancement services
- Software installation and regular software version updates / patches are always a challenge for cyber operations within a restricted air-gap environment. This is especially true for mobile FAK systems that contain many diverse software tools — both commercial and free or open source FOSS software, each with their own update schedule. NextComputing has developed unique capabilities to support FAKs deployed across air-gaps. NextComputing engineering support services will bundle multiple software updates together so that all integrated software packages can be brought to current version with a single operating procedure. Software updates with clear documented instructions will be provided via a secure ShareFile, such that cleared support personnel (either the customer team, or a cleared/certified technical support partner of NextComputing) have instant access to download updates and instructions to removable media to carry across the air-gap. Within the air-gapped zone, support personnel will be able to update all FAK units from a central point, using to “Federation Manager” feature of the Packet Continuum software framework.
- Certain FAK software tools, including threat intelligence resources with streaming data services or internet-based threat query access, will not operate as-is in an air-gap environment. NextComputing has experience working with customers to minimize operational complexities and optimizing the value for cyber operations of software tools within a restricted air-gap zone. Sometimes the solution is to bring the threat data base into the air-gap zone. HWhen this is not possible, NextComputing can assist with custom software and/or special operating procedures. NextComputing has extensive experience with FAK hardware, software tool suites in air-gap operation for multiple customers.
Operating Systems and Hypervisors Available for Integration on NextComputing Platforms
- Nextcomputing offers a range of operating systems and hypervisor based configuration options custom configured and optimized for your needs including integrating open source and commercial licensed cyber related applications. Our expertise includes the ELK stack (Elastic/Kibana), SPLUNK, graylog, packet capture, packet capture with file carving, malware detection and sandboxing, Suricata alerting with ET Pro rules and custom rules, Zeek, among a range of open source and commercial forensics investigation, malware analysis and pentesting applications
- Click here to learn more about NextComputing operating system offerings
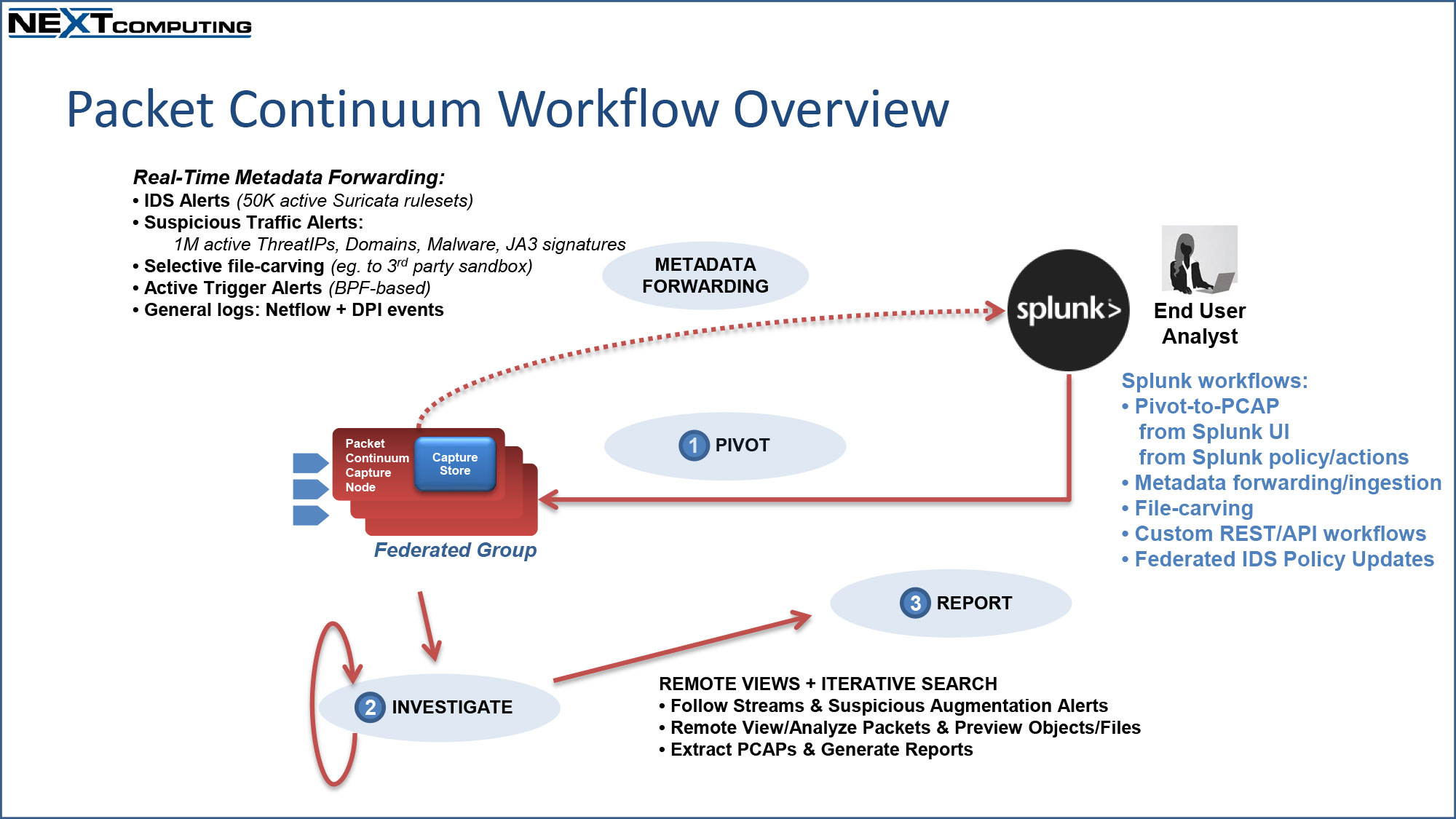
Packet Continuum Workflow Overview
(click to enlarge)