Packet Continuum Use Cases
Incident Response
As the fastest growing crime in the world, cyber theft is a top concern for companies across multiple industries. Budgets for mitigating cyber threats are expanding. The cybersecurity community and major media have largely concurred on the prediction that cybercrime damages will cost the world $6 trillion annually by 2021.
The roster of potential attackers is expanding too. Organized criminal groups have found the Internet to be a profitable avenue from which to mount high‐tech fraud, identity theft, and extortion schemes. Rogue nations are also increasingly involved in cyberespionage, cyberterrorism, and cyberattacks against defense, government, and private industry targets.

The right tools, the right plan
A successful incident response plan defines in advance the key performance indicators (KPI) to measure during the event. Companies use this phase to consider the various breach scenarios that could play out and identify their weak points, and risk factors, figure out what activities need to be closely monitored, and decide how best to spend their security budgets based on analysis.
Good measurements include time to threat detection, time to report an incident, time to triage, time to investigate, and time to response. On the qualitative side, some figures to track include the number of false positives and the nature of the attack.
Packet Continuum addresses critical elements inherent to a comprehensive incident response plan (IRP) for the detection, response and limitation of negative effects from a security event in a way that limits damage and reduces recovery time and costs.
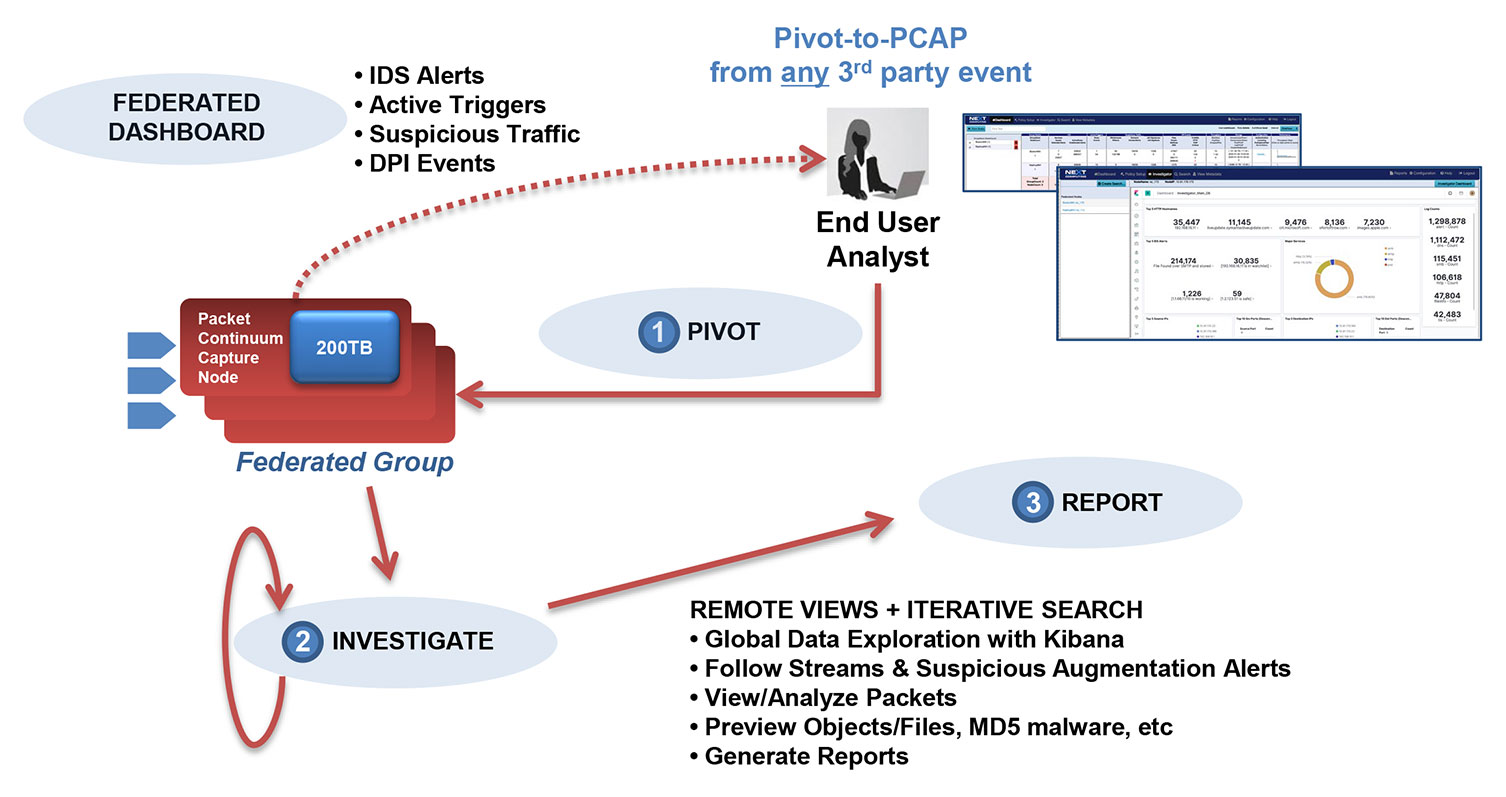
Every important detected threat requires follow up action. This kind of “Incident Response” action often involves investigating the full details of a critical network event by retrieving the lossless recorded network traffic in the form of a standard PCAP file, including the full payloads, attachments, etc.
From Packet Continuum’s convenient GUI dashboard, a cyber-investigator can query any PCAP history using data from IoC (Indicator of Compromise) events. Over time the investigator builds up a history of PCAP query results in the form of critical incidents from which they can gain insight about the problem to solve, whether it is a network performance problem or a cyber-threat.
A unique feature of Packet Continuum is ability to pre-wire an Open PCAP Forensic Workflow. PCAP queries execute very fast, extract a standard PCAP file format, and begin almost immediately to stream the PCAP results in small chunks to third party or open source DPI (Deep Packet Inspection) analysis tools. Using the REST/API, a technical team can “pre-wire” their system to automatically process the streamed results of every PCAP query. In fact, it is good practice to pre-wire PCAP results to multiple tools, because different analysis tools have different benefits – and not all tools will interpret the same PCAP data in the same way.
The ultimate benefit to a cyber investigator, when Packet Continuum query results are automatically pre-wired for DPI processing, is that they can easily visualize the results they need using all those tools immediately – almost as soon as they press the “submit PCAP query” button on the GUI dashboard.
Packet Continuum Key Features
Reduced Costs
Massive queries over large timelines, as well as federated search across multiple Packet Continuum-based security appliances in different locations. These features, among others, reduce labor/cost needed for analysis. Cutting costs in this phase opens the security budget for additional tools to implement a complete cybersecurity plan.
Active Triggers
Often, the plan that is developed, relies on information only gathered during the initial detection phase. But if the threat is persistent, it will reload when the computer reboots, perhaps with a different process name, and communicate with a different server. The security team should then enter an endless loop of detection, containment and eradication for the same threat. Packet Continuum enables analysts to set Active Triggers (BPF signature).
Behavior Analysis
The team should additionally investigate the malware’s techniques and behavior for a better eradication plan and a well-developed prevention plan. Packet Continuum’s behavior analysis features illuminate suspicious activity. The Log Investigator's enhanced search capabilities, allowing integrated pivot to PCAP and enriched metadata, enable behavior and signature visibility. The IDS Alert configurator and DPI Analyzer enable multi-level signature and behavior event session search and logging. This gives you the ability to configure groupings of signature and unusual behavior alerts dynamically.
Log Investigator
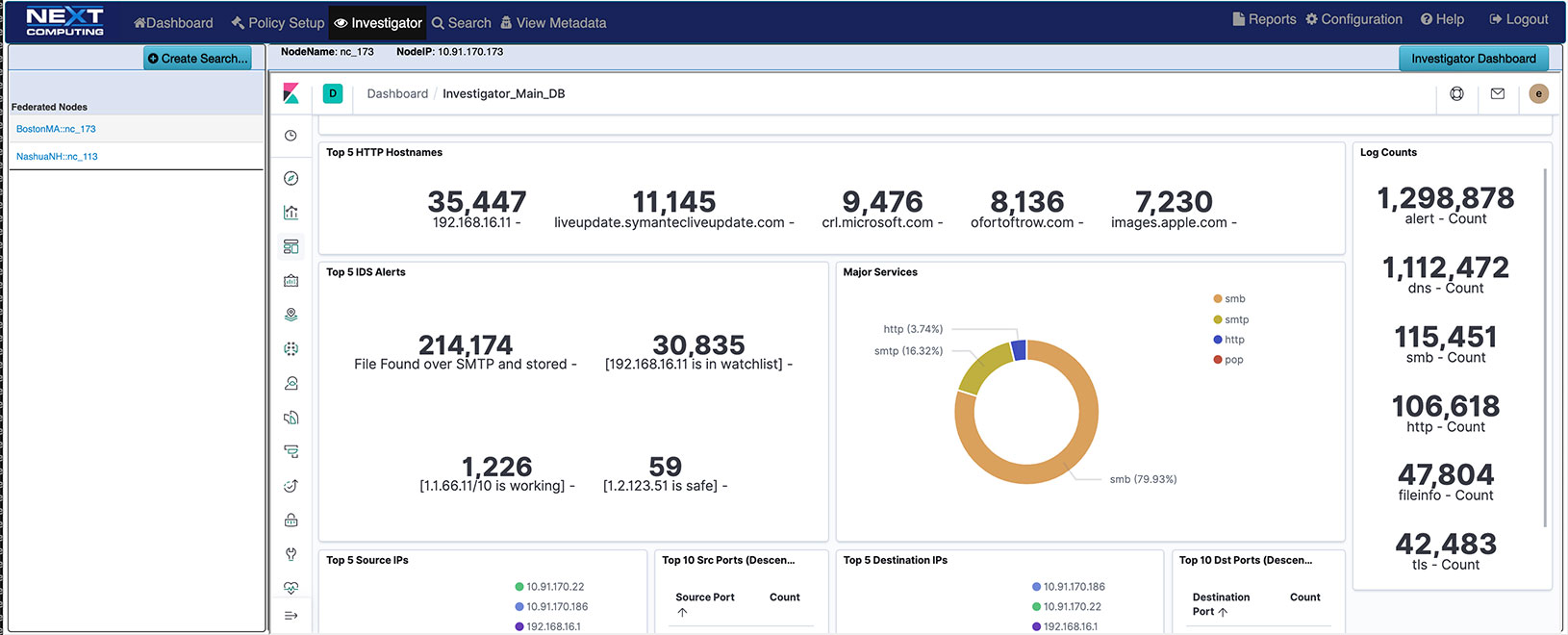
Incident response teams need to build and maintain a data repository that has continuous and broad visibility across the full environment. This is crucial for accelerating investigation and response. Packet Continuum’s real-time Log Investigator provides features to this end such as:
- Real-time indexing, for efficient query and retrieval of retrospective PCAP data or IPFIX records
- Real-time IDS alert configurator generates event logs for HTTP, Files, DNS, email, user agents, TLS/SSL, VOIP – all cross-correlated with PCAP & NetFlow V9 records
An End User can additionally use data from any third-party threat detection system for a PCAP search and investigation. Such incidents might be triggered by cyber security threat detection, suspicious activity, or performance anomalies, or simply based on an audit trail requirement (eg. for cross-border packet activity within a multi-tenant data center.) Log and maintain all identified threats from investigation for later search and analysis.
THREAT-HUNTING AND IOC AUDIT/ASSESSMENT
Packet Continuum is an ideal tool for field organizations to manage the critical tasks of cyber security assessment, and of ongoing threat-hunting operations. Teams on assignment can collect a wide variety of Indicators of Compromise (IoC) data (in the form of system logs or optionally as NetFlow V9 broadcasts), build evidence and generate reports about what they found. Many standards-based policy management methods allow for a rich set of IoC events, which will help the analyst to prioritize investigative action by what adversary behavior appears to be the most dangerous.

Network Troubleshooting
Drill down into specific network events to find out exactly what happened. Direct suspect network traffic through DPI software for analysis and data visualization. Captured data can be analyzed for suspicious traffic, such as non-DNS traffic over port 53, encrypted traffic over 80, etc. Analysts can use third party forensic tools with complementary analysis capabilities for multiple uses.
Endpoint Behavior Analysis
Packet Continuum allows you to see what’s happening on your endpoints and detect intrusions fast. Spear phishing attacks can quickly lead to compromised endpoints. External intrusions can result from unpatched systems or zero day attacks. The Packet Continuum architecture provides deep, real-time visibility into endpoint and server activities. It detects intrusions and suspicious activity through behavioral analytics.
Correlate metadata about users, files and sessions with real-time threat information, and use the correlations to provide situational awareness reports and alerts. Identify employees using unapproved applications or using applications in ways that violate policies.
Advanced threats are more accurately detected for a comprehensive endpoint behavioral analytics solution.

VOIP CYBER ATTACK INVESTIGATION / MITIGATION
The increase of enterprise RTC (real time communication) such as VoIP (voice over IP) and UC (unified communication), along with the mainstream availability of covert methods of intercepting IP packets, have made RTC a prime target for hackers. Cyber-attacks using the VoIP protocol SIP (Session Initiation Protocol) have been growing and has accounted for over half of the security event activity analyzed in previous years, according to a recent report from IBM’s Security Intelligence group. The annual cost of SIP attacks alone in 2017 was estimated at $11.7 billion, according to CFCA, the SIP Forum, and Telecom Reseller.
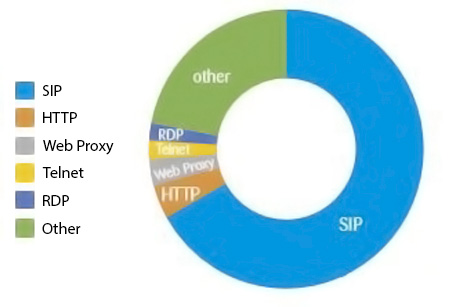
image courtesy of HTTPS://WWW.PROFWOODWARD.ORG/2016/02/ARE-YOU-ONLY-ONE-USING-YOUR-VOIP-PHONE.HTML
SIP‐sniffing software is readily available on the Internet, which makes securing RTC particularly challenging. For example, attackers can freely download network protocol analyzers to capture and interpret VoIP calls, record media streams, and intercept instant messaging communications. Other tools, such as UCSniff, can be used to identify, record, and replay VoIP conversations or IP videoconferencing sessions.
The most common threats for RTC attacks are:
- DoS (Denial of service) attacks
- Toll fraud, including number harvesting, spam over Internet telephony (SPIT), and spam over instant messaging (SPIM)
- Identity theft, including caller ID spoofing, eavesdropping, and call hijacking

image courtesy of SNOM.com
Hacking into RTC sessions requires that the malicious party intercept signaling and/or media flowing between two endpoints at any of several points along the communications path. Several potential points of attack exist in RTC sessions, including …
- UC application servers
- Call control elements, such as PBXs and automatic call distributors (ACDs)
- Session‐layer servers and proxies, such as SBCs
- Transport and network layer elements, such as routers
- Link‐layer elements, such as Ethernet switches and wireless LANs ✓ Endpoints, such as desktop and laptop PCs, mobile devices, IP phones and videoconferencing terminals
Telco and Network engineers need to bring up and test IP related equipment and do quality of measurement performance from a “packet level” and packet count perspective and assess performance of SIP based RTC / VOIP based sessions including jitter measurements.
VOIP for Incident Response with Packet Continuum
The addition of VOIP for IR (incident response) to the Packet Continuum Log Investigator enables:
- Log and search of SIP based RTC/VOIP sessions
- Ability to pivot to extract SIP, RTP (Real-time Protocol) and RTCP (Real-Time Transport Control Protocol) packets for each session
- Loading of extracted session into WireShark for further VOIP decoding including voice playback
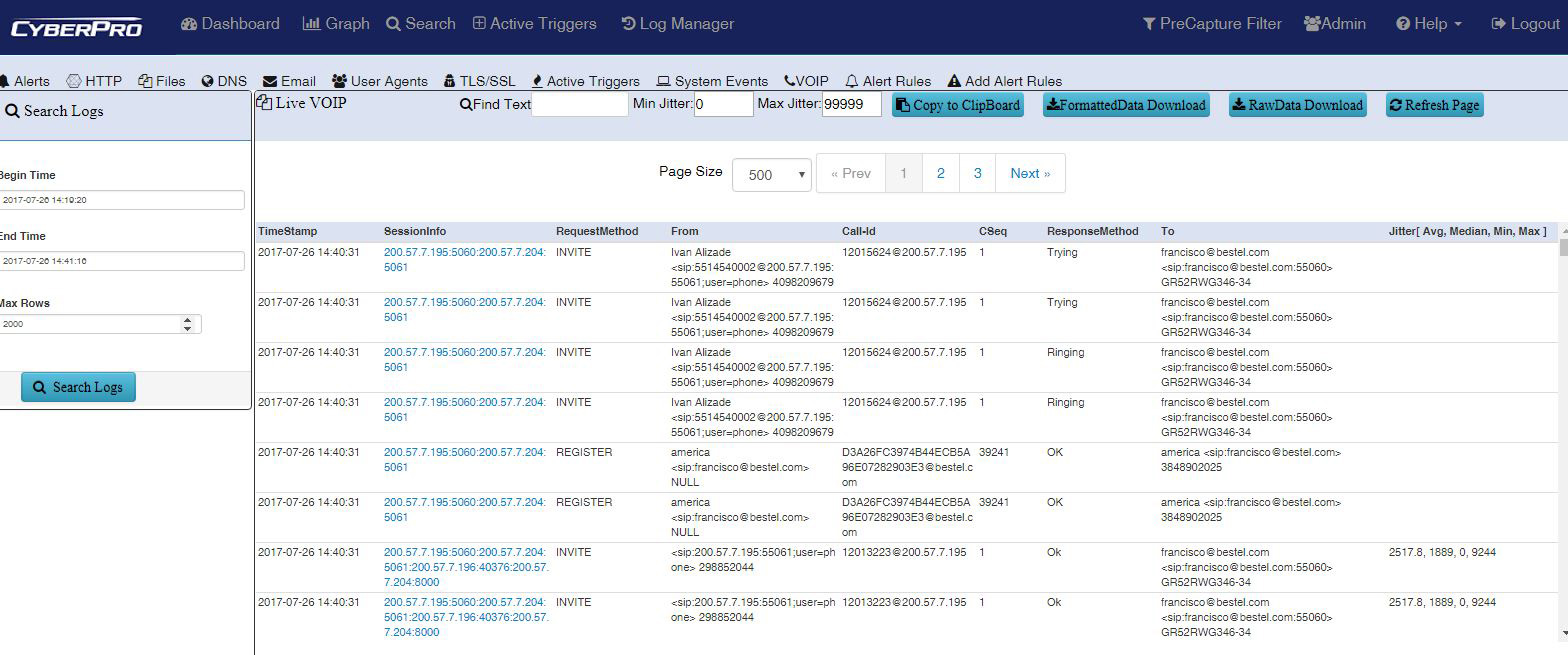
Packet Continuum VOIP jitter summary (Avg., Median, Min., Max. value)
ON SITE NETWORK TEST & MEASUREMENT
A recent Frost & Sullivan report predicts the Network testing market will reach $25 billion by 2025. Packet Continuum can be deployed in a small, portable form factor appliance which enables onsite analysis when the network is slow, or bottlenecks develop.
Cyber threats often appear to be benign anomalies at first detection, but upon further analysis unveil malware that was masked as a performance issue. Packet Continuum allows immediate investigation into these performance issues to determine in real time if a threat does, in fact, exist.
There are a variety of transport options for the CyberPro for ease of travel for incidence response and other use cases.
- Soft case with additional pockets for cords and accessories. Fits in the overhead bin of a plane.
- Compact rugged case with foam cutouts for accessories. Also fits in the overbid of some planes.
- Full size rugged case with wheels and telescoping handle. Can be checked as baggage, while giving you peace of mind that your system is safe.
Additional Use Cases
COMPLETE CYBERSECURITY TOOL INTEGRATION
An end user can use data from any third party threat detection system for a PCAP search and investigation.
Cybersecurity resellers and integrators who represent other vendors and tools that are complimentary, with a need for a portable tool for onsite monitoring and response, can add to their existing infrastructure for a complete cybersecurity solution package for their clients.
Packet Continuum’s quick, simplified workflow features also cut costs to open up the security budget for additional tools necessary for a complete cybersecurity plan.
compliance enforcement
Packet Continuum makes it easy to investigate compliance violations on an enterprise network. In addition, integration with a portable appliance such as the CyberPro allows for non-intrusive testing and audits at branch office locations.
Identify employees using unapproved applications or using applications in ways that violate policies. Correlate metadata about users, files and sessions with real-time threat information, and use the correlations to provide situational awareness reports and alerts.
Use encrypted traffic analysis features to understand what employees are sending over encrypted email, ftp or other channels.
Security Breach Evidence
All packet captures and log events can be used as legal evidence or compliance verification, which can be a requirement for use as evidence after a breach, attack, or any incident. The CyberPro portable appliance with Packet Continuum enables immediate, onsite retrieval of needed data evidence.
lawful intercept
Packet Continuum’s pre-capture feature is ideal for enforcing the selective capture of targeted users on a network, with the self-contained portable form factor of the CyberPro, for non-intrusive network connectivity, and evidence chain-of-custody enforcement.
All packet captures and PCAP files extractions can automatically be tagged with a file hash, to assure the “chain of custody” of legal evidence, which is a requirement for use as evidence in a future criminal prosecution after a breach or attack.
Threat Intelligence
Information from third party threat intelligence can be used to detect, classify and extract objects (files, URLs, IP addresses, etc.), and to inspect and take appropriate actions to enrich cyber investigations and generate alerts.
Packet Continuum then provides twofold security against malicious IP addresses.
- Asset IP monitoring enables identification, monitoring, viewing and automatic approval of Critical IPs (essential infrastructure) as well as Trusted Asset IPs (host IP addresses defined as safe).
- Threat IP monitoring enables identification, monitoring, viewing, and mitigation of pre-defined Threat IPs as well as user-defined IPs. Packet Continuum comes pre-loaded with a known list of Threat IPs; a number of malicious IPs previously identified by trusted sources such as US-CERT, for your protection.
Botnet Command-and-control activity
Using extracted metadata such as a malware encryption key, forensic analysts can go back in time and reconstruct all C2 activity performed by such malware (e.g. via a tool such as ChopShop). This will provide insight into critical attacker activities such as details on lateral movement through the environment.
Forensic Traffic Analysis
Captured data can be analyzed for suspicious traffic, such as non-DNS traffic, over port 53, encrypted traffic over 80, etc. This is especially useful if the End User uses third party forensic tools with complementary analysis capabilities. There many possible creative use cases.