CyberPro Plus X
High-Speed Portable Capture Appliance -
TSA Carry-on Compliant Form Factor
CONTACT US TODAY TO START BUILDING YOUR ORDER

The intelligent, compact design of the CyberPro Plus X allows for both easy transport and expandability. Whether you need cyber analytics in the field, or the flexibility to grow your toolset with your changing needs, the CyberPro Plus X has you covered.
CyberPro appliances are based on a powerful software architecture that offers lossless packet capture, fast query retrieval, IDS alerting and a real-time Threat Hunting / Log Investigator. It is integrated into a unique, impossibly small portable form factor, addressing critical elements inherent to a comprehensive incident response plan (IRP). This makes CyberPro ideal for multiple cybersecurity use cases that require onsite response, analysis and mitigation.
CyberPro Plus X includes a unique threat-hunting feature: Use a SNORT/SURICATA rule set for “Retrospective Detection” of PCAP history. Find out if a newly discovered IoC was active in your network – even before the threat was known!
For higher throughput the CyberPro Plus X 100G offers twice the capture interfaces for 100Gbps aggregate continuous PCAP capture.
Our core technology enables capture rates unheard of in such a small form factor. Just as easily as we can scale down this much performance into a compact system, CyberPro cost-efficient systems can be federated at a massive scale. Federated, CyberPro systems can be used at multiple sites from a central hub for monitoring offsite, as well as providing the ability for SOC teams to update security policies remotely.
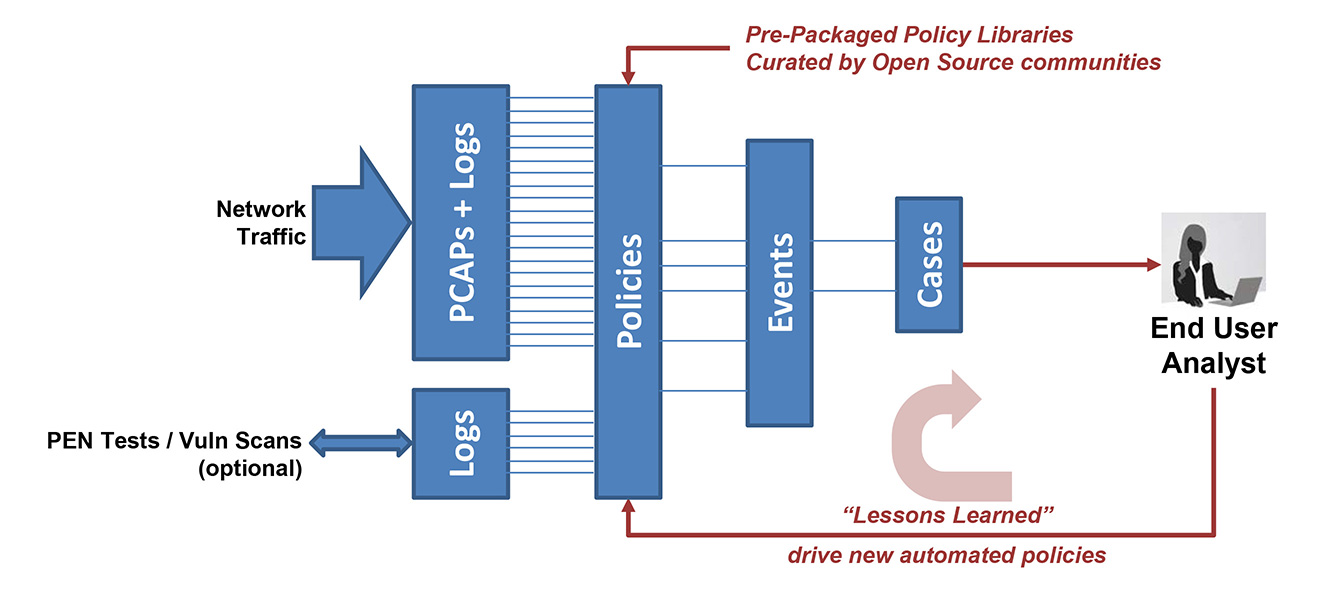
CyberPro systems are designed for standards-based policies with open data access. We leverage trusted open source communities for databases of threats and rule sets to keep you alerted of critical incidents for full-session analytics and reconstruction. Logs and data are then available in standard file formats so you can integrate them with your own preferred tools.
With a full-featured, mature REST/API, custom workflow scripting, and 3rd party event / data / PCAP correlation, CyberPro systems offer open workflow automation & orchestration. End users, resellers and integrators can incorporate data from any third party threat detection system for a complete cybersecurity solution package.

Key Features
High-Speed Capture
Up to 20Gbps continuous lossless packet capture with simultaneous search and analytics support. Configuration options for 2x25G (50Gbps) continuous PCAP capture only and post analysis / search.
Large Capture Timeline Storage
10-200 TB storage options via fixed or no-tools removable drives, additional storage up to 200TB
Real-Time Packet Analytics
- Lossless packet capture at line rate
- Policy management
- Real-time alerting/detection (standards based)
- Defended assets, defended services, IDS alerts, IoC alerts, malware and event logging – at line rate
- Event-based and simultaneous PCAP session search/retrieval
- Data compression in-line
Simultaneous search
Stream initial search results of PCAP, NetFlow, and log files to any visualization tool, even while a critical search in on-going. No more waiting for endless query response times! CyberPro Plus X includes a unique threat-hunting feature: Use a SNORT/SURICATA rule set for “Retrospective Detection” of PCAP history. Find out if a newly discovered IoC was active in your network – even before the threat was known!
Active Triggers
Use real-time, dynamic, user-defined Active Triggers and real-time analytics to rapidly direct critical PCAP data for post-processing, using any of multiple third-party open source DPI software packages, conveniently pre-installed and ready-to-use within the system.
Extensive Logging Features
RFC anomaly logging, file download event logging, multi-protocol event / metadata logging. The Log Investigator also allows for search, cross-correlation and extraction: HTTP, files, DNS, email, user agents, NetFlow, TLS/SSL, and VOIP.
Efficient Data Management
CyberPro Plus X’s built-in PCAP streaming means that no third-party software will “choke” on too much data throughput during PCAP post-processing.
Visualization
Visualization is pre-installed and hard-wired into the CyberPro Plus X fully integrated analytics workflow, using open industry-standard data file formats: PCAP & NetFlow records open in WireShark; log searches open as CSV files; reports as TXT/RTF files.
Optional Features
- Penetration testing / security scanning tools package for more active analysis
CyberPro Plus X Workflow
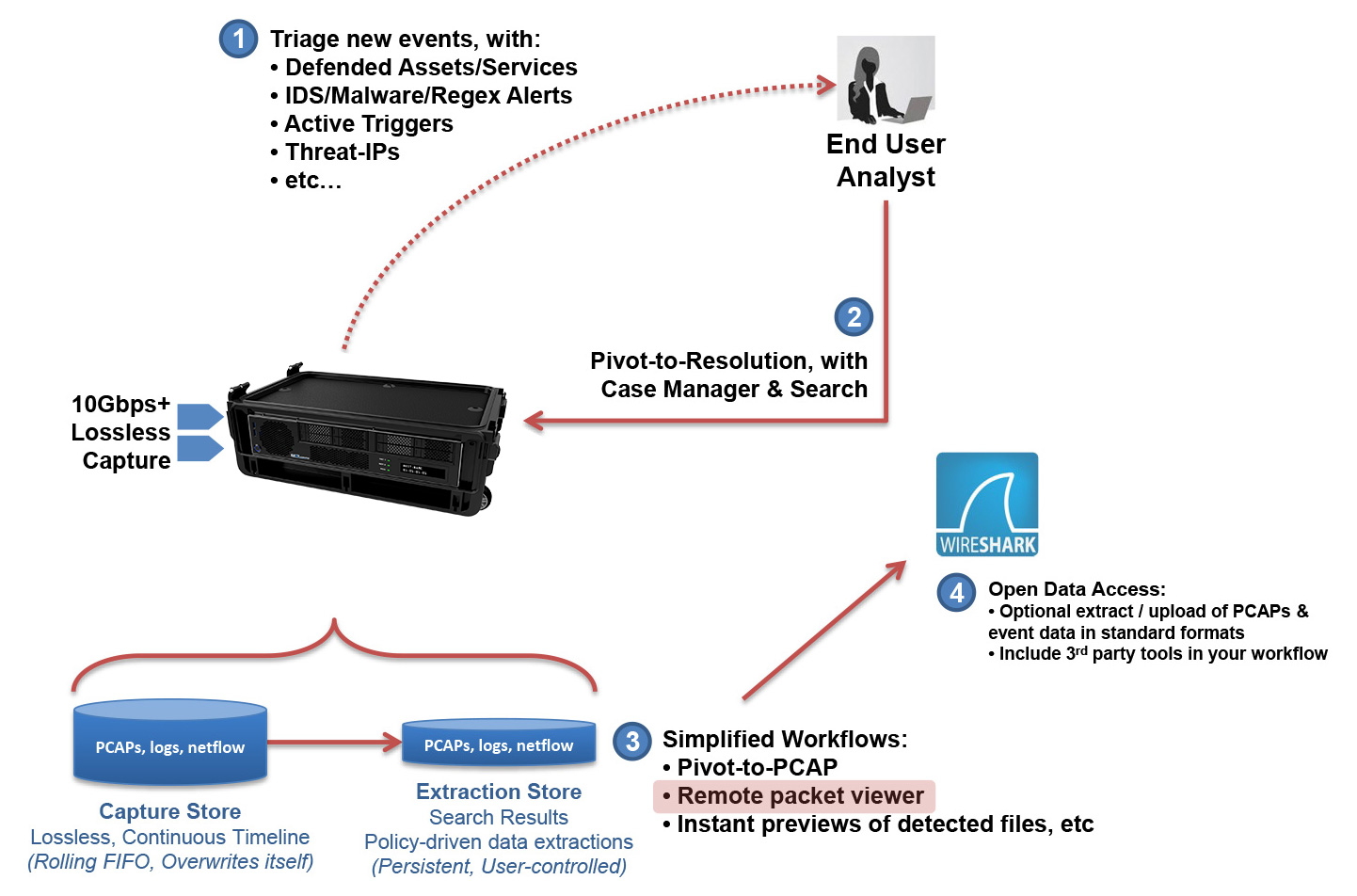
CyberPro Plus X utilizes NextComputing's Packet Continuum architecture to let you jump quickly between PCAP actions and your tools-of-choice. Gain new insight from DPI analytics tools, and generate graphical incident reports. Then iterate new Active Trigger alerts and PCAP searches, to conclude your investigation quickly.
Real-Time Analytics Features
Open simultaneous BPF-based “Active Triggers”. Adjust them dynamically.
Log Investigator events, all with search, cross-correlation and extraction:
- HTTP
- File event logging, with file size and URL or SMTP reference
- DNS
- User agents
- TLS/SSL
- VOIP
- NetFlow
- Active Triggers (BPF signature)
- 50,000 Snort rules (emerging-DNS, emerging-ftp
- 1 Million ThreatIP alerts
- System events
Log Investigator search actions:
- All logs are time-correlated with PCAPs and NetFlow data
- Text string search of logs
- NetFlow record logging and search
- Choose your results for any search: PCAP, NetFlow, logs, etc.
- One-click searches auto-populate time period and search filter (BPF), based on context
CyberPro Plus X Open Data Access
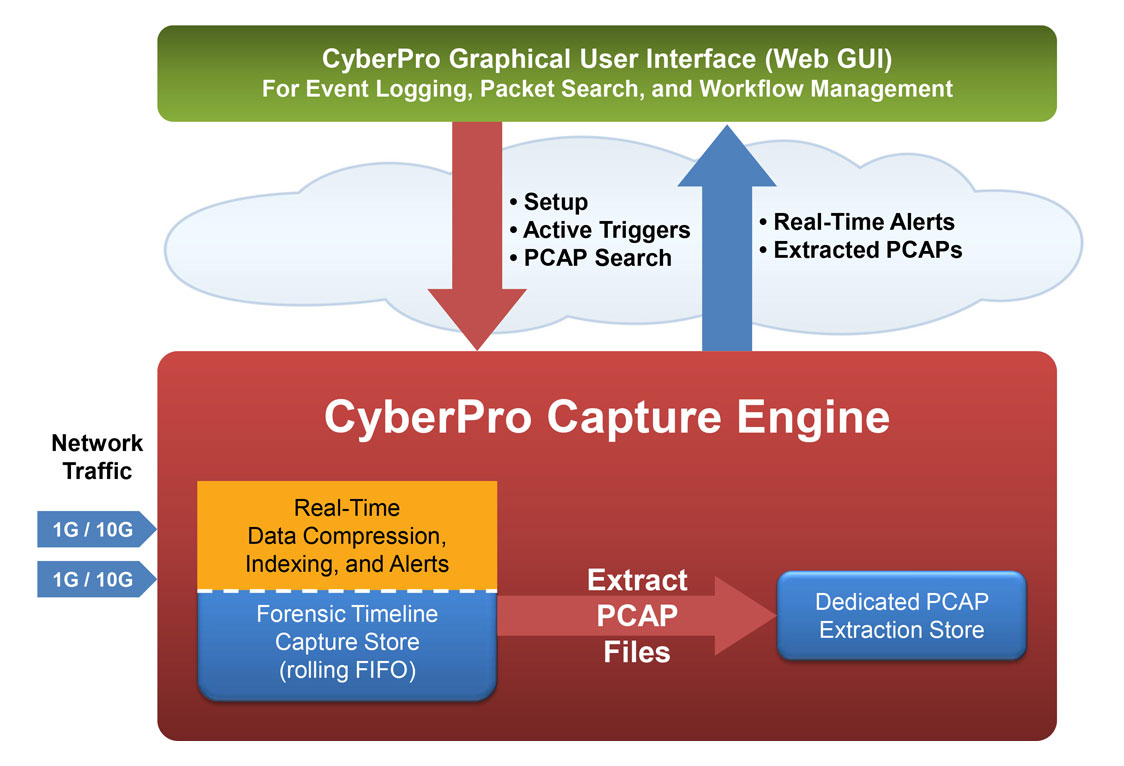
Continuous lossless packet capture into a rolling FIFO Capture Store
Searchable data recorder for NetFlow records and log files
Real time indexing and alerting — with time stamping as low as 150 nanoseconds
Data compression in real time — Overall storage amplification up to 3x
Dedicated onboard Extraction Store retains all search query results, retrievable by user-defined name
Options for PCAP (or NetFlow) search results:
- View in Wireshark on a local display UI
- Remotely access from an external host via Web GUI or REST/API scripting
- Run the critical sessions over the Streaming Playback Interface to any 3rd party forensic analysis tool. Simply connect streaming playback output to the capture interface of your tool, just like a span/mirror port.
Standards-based Policies, with Open Data Access
Leveraging trusted open source communities – at enterprise scale
- Snort/Suricata — IDS alert rulessets
- BPF — User-defined Active Trigger alerts
- Defended Assets/Services — Flexible user-defined lists
- TAXII/STIX — pre-packaged ThreatIPs and rulesets, supported via structured cyber threat information
Open Data Access, with standard file formats
- PCAP-NG packet data
- NetFlow v9 records
- Text/CSV/syslog for enrichment log data
Open Workflow Automation & Orchestration
- Full-featured, mature REST/API
- Custom Workflow Scripting
- 3rd Party Event/Data/PCAP Correlation
A PORTABLE CASE-MANAGEMENT FRAMEWORK
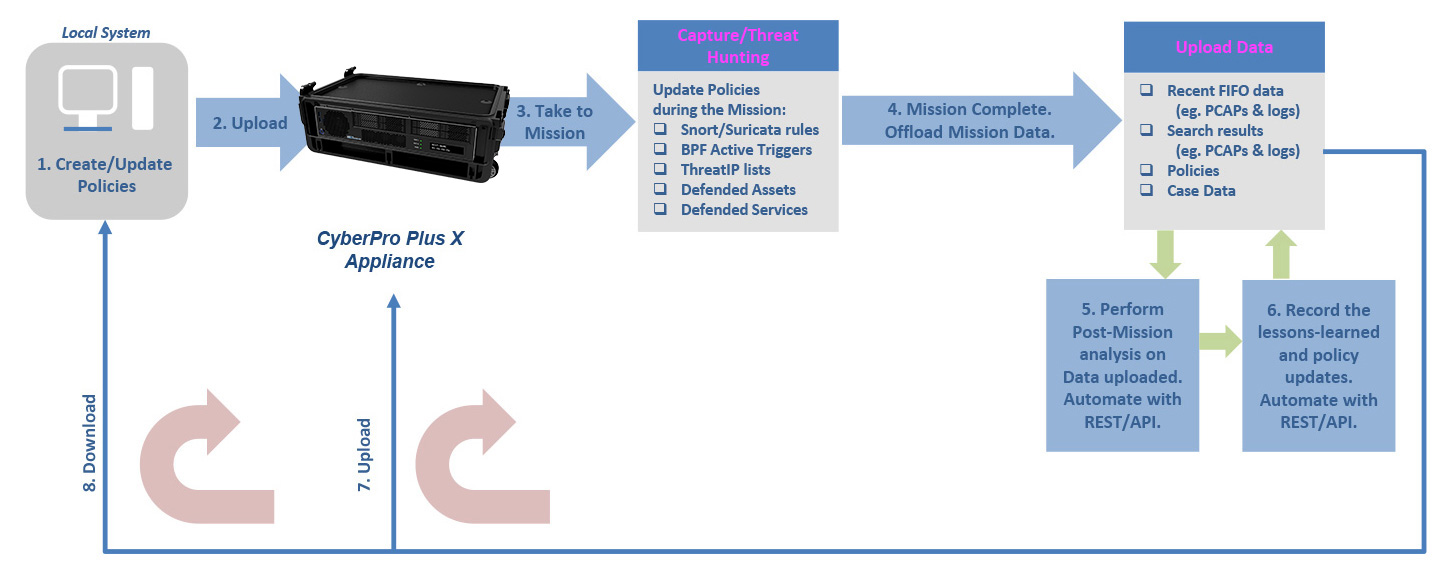
- Cyber team will create/update initial policies on a local system.
- Before each mission, upload these policies to a CyberPro Plus X for use during the mission.
- During the mission, Capture / Threat Hunting. Update real-time alerting policies, as required.
- After the mission, offload data that includes marked case data, current policies, and last Capture Store / Extraction Store data.
- Perform Post-Mission analysis on the data uploaded in step 4. Automate the post-mission analysis operations by utilizing the NextComputing REST/API.
- Record the set of lessons learned and policy updates.
- To iterate for the next mission, go to Step 2: upload and share new Policies with the CyberPro Plus appliance(s).
- Download any updated policies to the local system, as needed to update and upload again.
CyberPro Plus X Capture Process
Continuous lossless packet capture into a rolling FIFO capture store. A separate extraction store retains PCAP file query results.
4-tuple indexing in real time — IP address source/destination, port source/destination — with time stamping as low as 150 nanoseconds
PCAP compression in real time — Overall storage amplification up to 20x (depending on % of captured traffic that is SSL or video)
Search PCAP data from a convenient web GUI, using easy BPF+ descriptors, immediately streaming the results from capture store to persistent extraction store.
A PORTABLE BUILT FOR SCALE
The CyberPro Plus X works as a stand-alone appliance, and several can also joint together for even greater functionality.
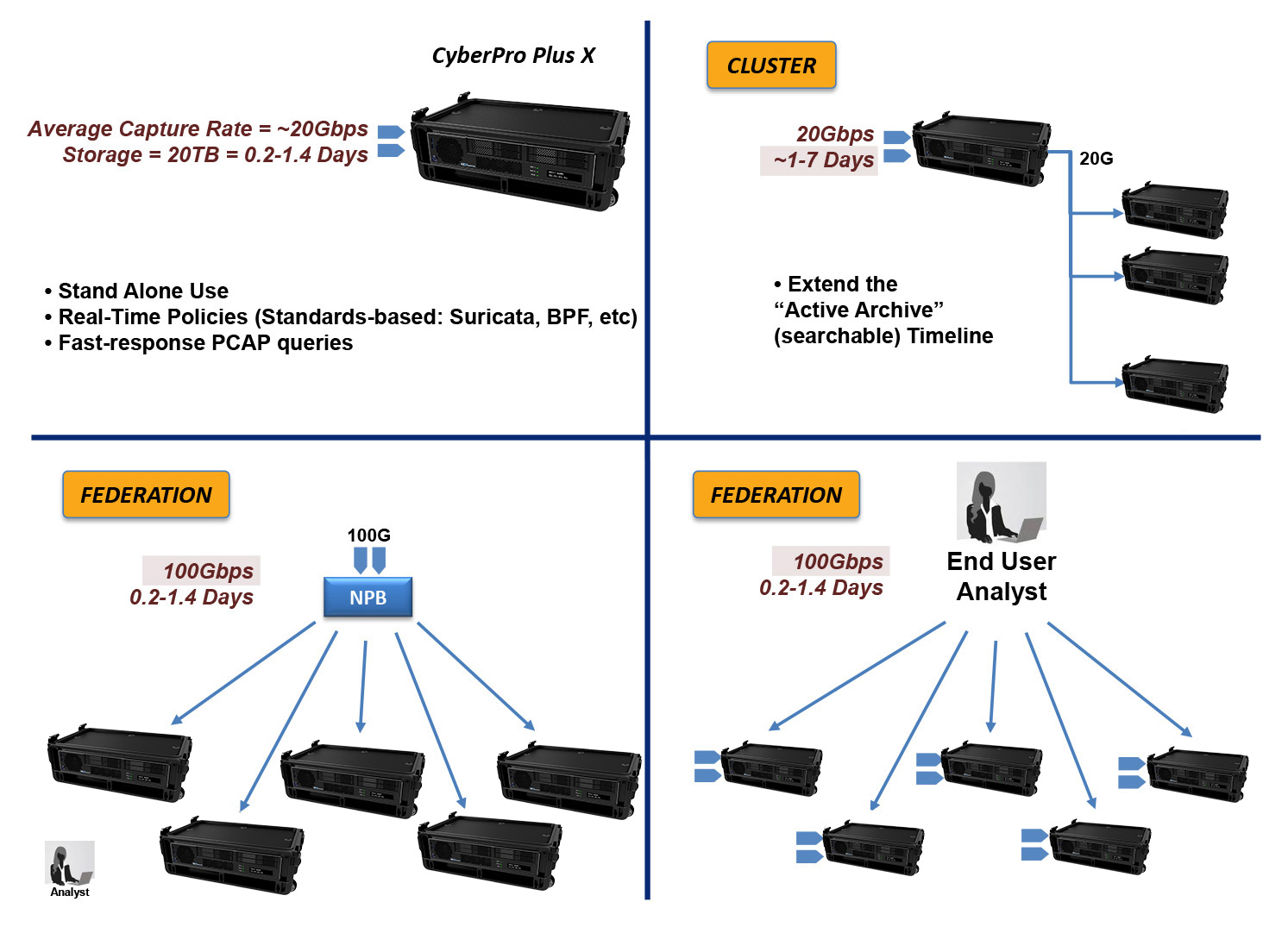
When you require additional capture timeline in the field, configure and connect several other CyberPro Plus X appliances as "Cluster Nodes". NextComputing's unique MapReduce software framework spreads the processing load, so long timelines are as quick to search as with a single appliance.
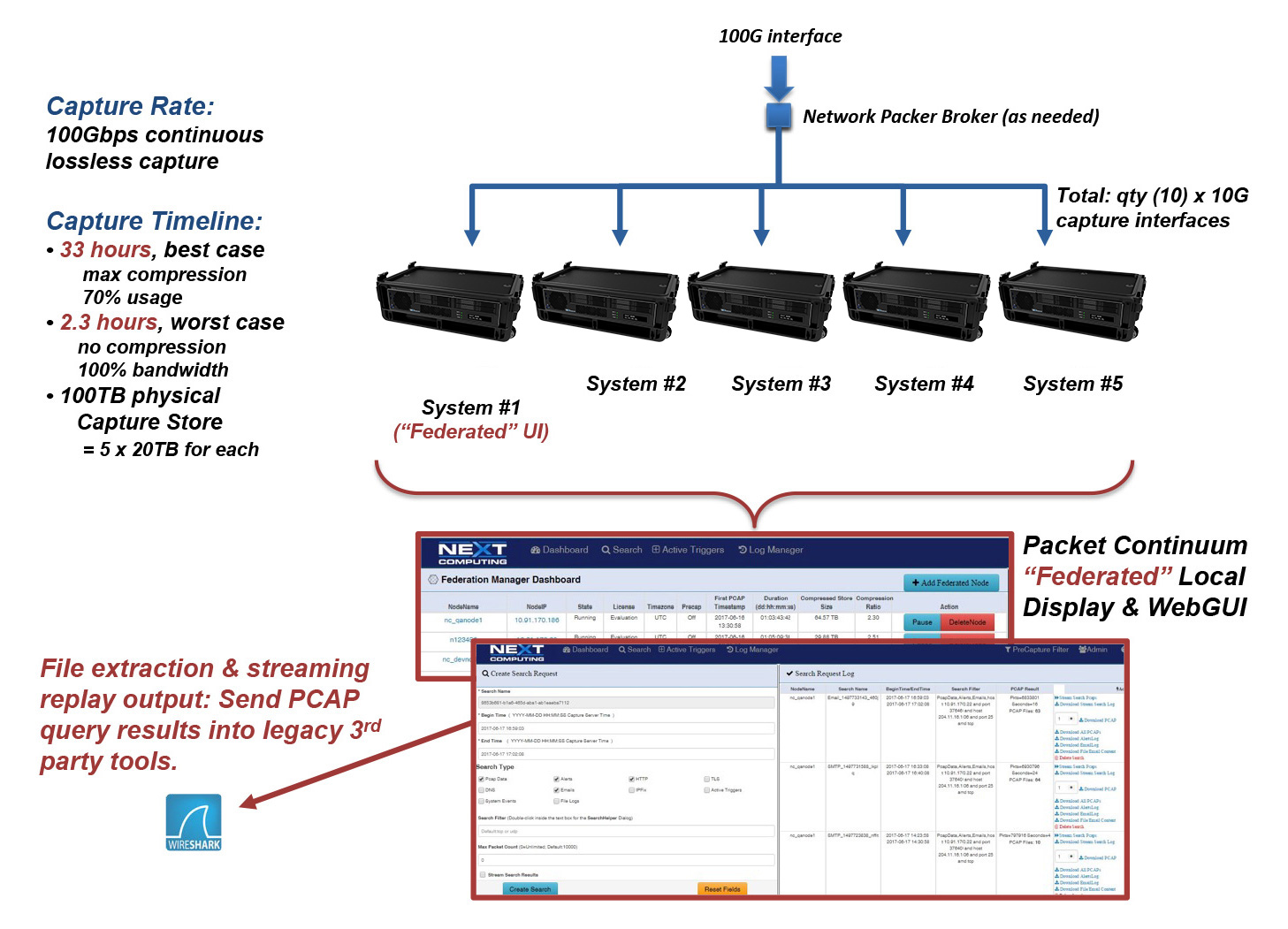
When you set up multiple CyberPro Plus X appliances to capture at different locations, a single analyst use the Federation Manager capability for integrated remote access via unified web-based UI.
When you have ad-hoc requirements for lossless capture of very high capture rates the Federation Manager will also do the job. When high-rate traffic is split (using a Network Packet Broker or Load Balancer) into multiple lines, each CyberPro Plus X can capture up to 20Gbps of the load or higher, and an end-user analyst will see all traffic integrated within the Federated UI. With Federation Manager features, it does not matter where the packets are located: You can make a single query for the whole traffic contents, and the results will be combined from all appliances into a single set of PCAP file results.