Enterprise Scale Packet Capture and Recording
Need efficient forensics investigations of potential breaches, indicators of compromise (IOC) , malware, data exfiltration, and network vulnerabilities?
Learn how we can help with enterprise scale packet capture and recording of network IOC events, application events, and enriched network metadata with fast correlation and search
Identification of threats
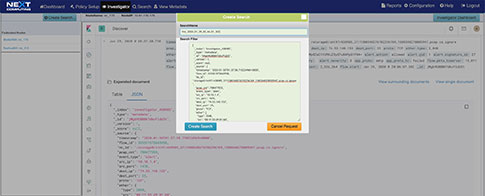
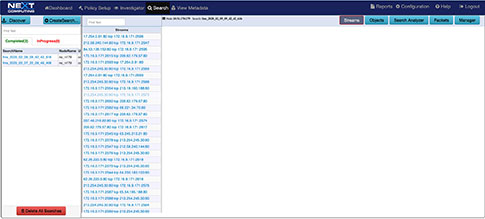
Forensic analysis workflows - fast search – follow the stream
Malware identification
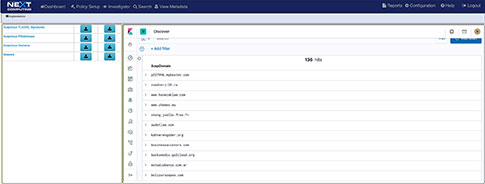
Suricata IOC signature and application ID rules - suspicious domains - threat IPs
Easy integration
Combine with or pivot from your existing SIEM, alerting, and threat intelligence tools
Lossless Capture
Configuration options from 1Gbps to 500Gbps+
Consolidated views
Single and geographically dispersed locations aggregated views
Multiple Use Cases
Cyber Security Operation Center, forward deployment, and much more
Workflow Examples
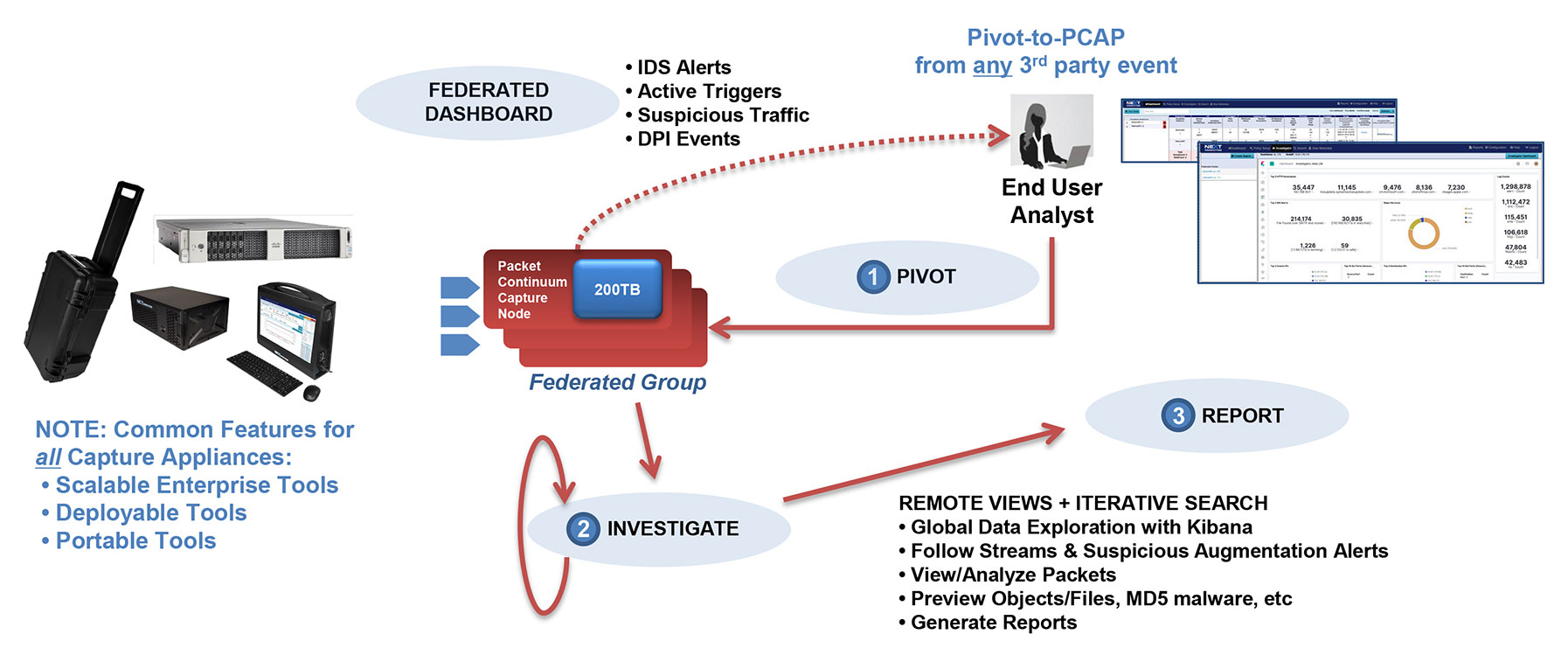
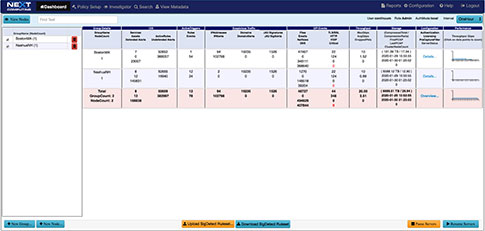
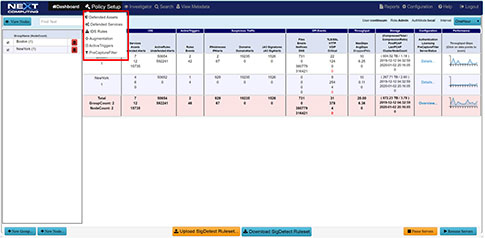
Total Overview Dashboard Pivot Point Workflow

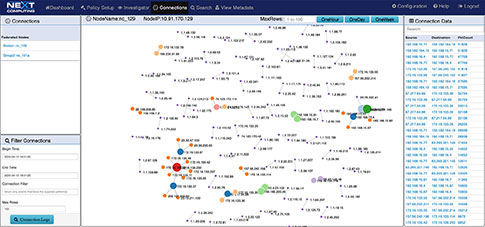
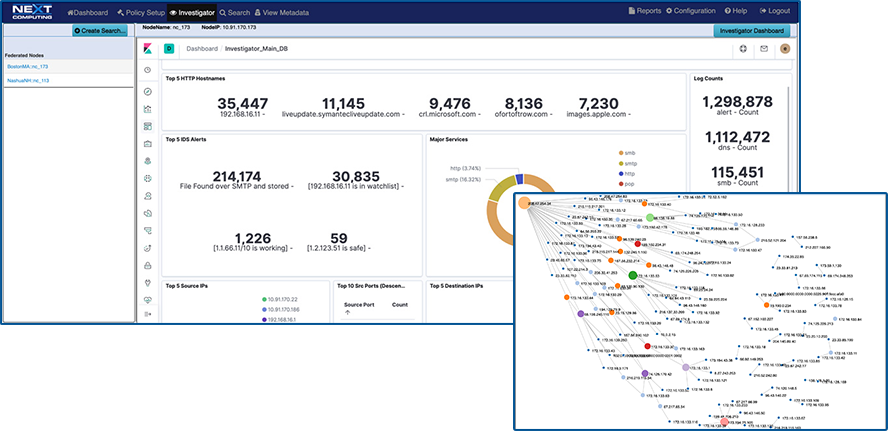
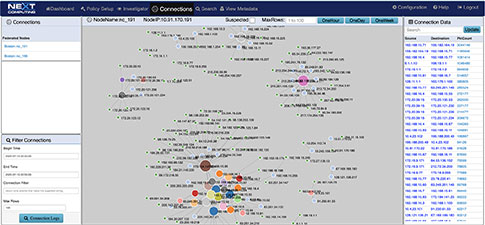
Network Topology View Augmented by Suspected IP Address View

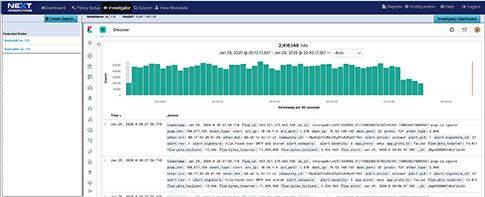
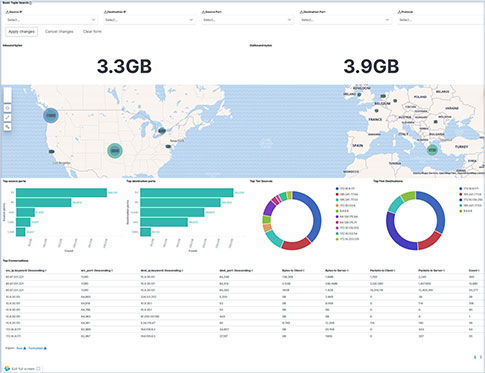
DSCP Network Performance Metrics Investigation/Search Workflow

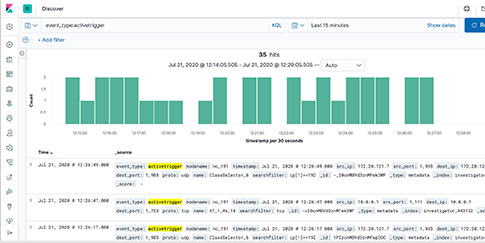
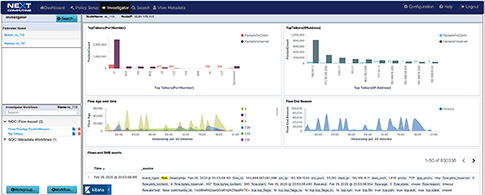
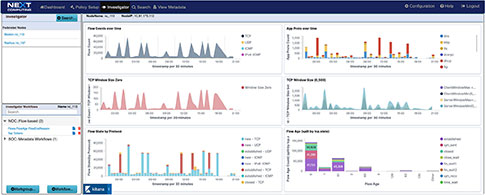
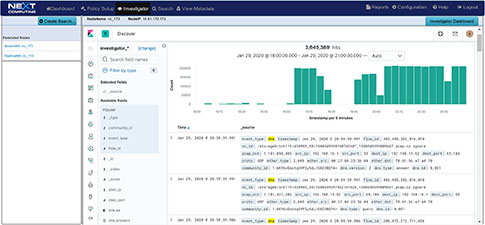
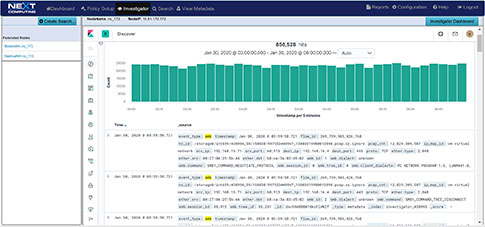
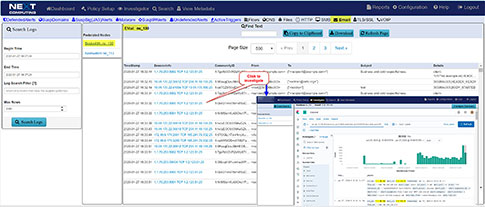
TLS-SNI Pivot Workflow

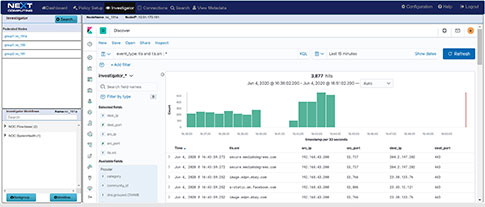
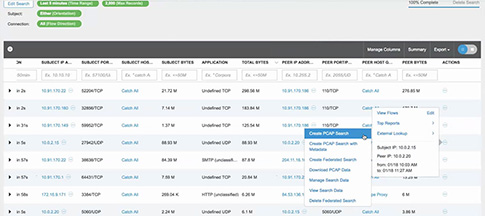
Suspicious Traffic Workflow
Packet Continuum's DPI Engine and Augmentation pipeline ensures that metadata associated with suspicious traffic are identified and tagged.
This sequence explains the workflow from defining policies to identify suspicious traffic to the display of the metadata events tagged as suspicious traffic.
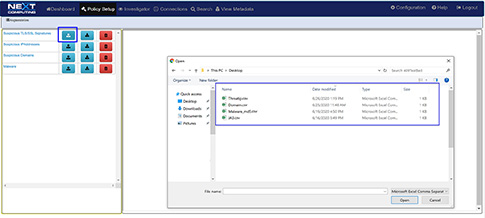
There are 4 types of augmentation policy data that can be provided to the Augmentation server:
- Suspicious TLS/SSL Signatures
- Suspicious IP Addresses
- Suspicious Domains
- Malware
The Augmentation tab allows users to upload additional data that can be used to enhance the value of stored data and allow data correlation. This workflow explains adding a watchlist and investigating the suspicious traffic for further analysis.

Packet Continuum is a powerful packet analytics framework for lossless continuous network packet and flow data capture with concurrent analysis and search. It is designed for use cases including:
- As a network data forensics analysis platform to complement existing tools within an Enterprise SOC (Security Operations Center)
- For Packet Network engineers to use in troubleshooting and packet-based QoS analysis in the field for 5G wireless networks and other network infrastructure
- As a forward deployment or portable packet data recording and forensics analysis tool for cyber and network auditing and analysis for cyber services practitioner companies
- As a complementary cyber forensics benefit as a service for Managed Security Service Providers (MSSP)
- As an application identification and application forensics analysis platform to complement existing tools within a NOC (Network/IT Operations Center)
NextComputing offers a flexible business model for financial, technical and logistic support services including appliances based on Cisco, DELL, HP, SuperMicro and our purpose-built small form factor deployable and portable servers with perpetual and annual software licensing models. We use open standards CentOS and RedHat, standard AMD EPYC and Intel Xeon server SKUs with standard Intel network cards from 1G, 10G, 25G and 100G for ease of IT management, maintenance and updates.
Core benefits include:
- Advanced policy-driven threat-hunting
- Real-time alerting/detection of Indicators of Compromise (standards-based)
- Fast search of lossless packet capture history, and correlation with events
- Options for numerous distributed sensor/recorders within a highly-scalable “Federated” network architecture, for close coordination with a central Security / Network Operations Center
- Configuration options for long capture timelines for days, weeks, or months of lossless packet capture data history, when quick-response search is required
- Added timeline features include in-line data compression
- High capture rate capture points (eg. 40Gbps, 100Gbps, and beyond) where a full feature set of real-time analytics functions must run at line rate with deterministic performance: Continuous lossless full packet capture (PCAP), real-time IDS alerting and other user-defined Policy Management, with simultaneous search/recall for Incident Response
Packet Continuum is disrupting the market with open data access, smooth scale, and long timelines – at very low cost!
Cybersecurity Awareness
Cyber theft is the fastest growing crime in the United States. The cybersecurity community and major media have largely concurred on the prediction that cyber crime damages will cost the world $6 trillion annually by 2021. Cybersecurity spending is expected to exceed $1 trillion by 2021.
Global ransomware damage costs are predicted to exceed $5 billion by the end of 2017, a 15X increase in the past two years. Healthcare organizations are the No. 1 cyber-attacked industry with ransomware attacks expected to quadruple by 2020. This translates to human attacks reaching 4 billion people by 2020. As the world goes digital, humans have moved ahead of machines as the top target for cyber criminals. Microsoft estimates that by 2020, 4 billion people will be online—twice the number that are online now. Today's hackers smell blood, not silicon.
Cyber crime will more than triple the number of unfilled cybersecurity jobs, estimated to reach 3.5 million by 2021. Every IT worker, every technology worker, must be involved with protecting and defending applications, data, devices, infrastructure and people. There is a massive cybersecurity workforce shortage, resulting in an unemployment rate of zero within the industry.

Cybersecurity Mistakes

"...most major industry player tools are expensive and offered as proprietary, single or incomplete solution security tools."
More than a quarter of data breach incidents in 2016 took at least one month for companies to discover, and 1 in 10 went unnoticed for at least a year. These results are compiled from the latest report on data breaches from Verizon’s security research division, which analyzed 1,935 breach incidents reported by 65 organizations. According to the report, nearly two-thirds of the breaches that were discovered in days or less were associated with incidents that are easy to catch, like physical theft or administrative accidents. Breaches that took months or longer to detect largely fell into categories like “cyber-espionage,” “point-of-sale intrusions,” and “privilege misuse.”
Why the big increases in the share of incidents discovered at both the long and the short end of the timescale? The facts are most major industry player tools are expensive and offered as proprietary, single or incomplete solution security tools. They do not mix with other cybersecurity tools effectively enough for a complete security solution. Many of these tools are also very complex and labor intensive to use. They often lack true lossless forensics recovery analysis capabilities in the event of a breach.