CISCO SECURITY WORKFLOW
- Use Steathwatch to initiate detailed Forensic IR Investigations
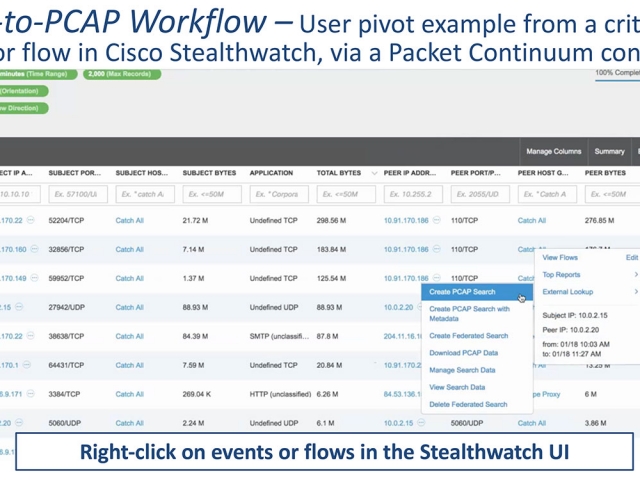
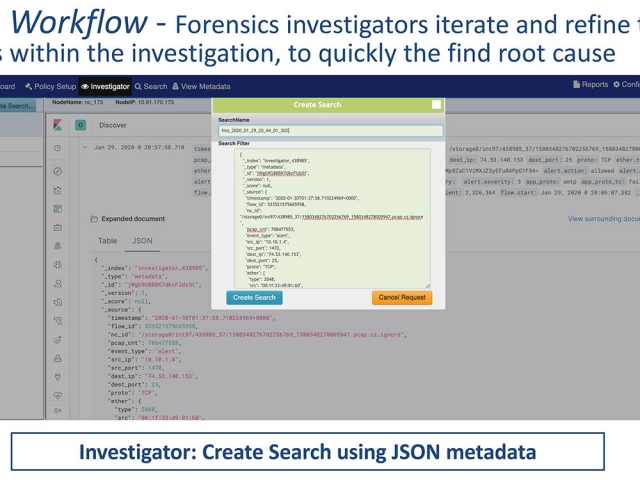
- Examine full lossless packet capture data of suspicious activity around any critical alert – over extended timeline periods
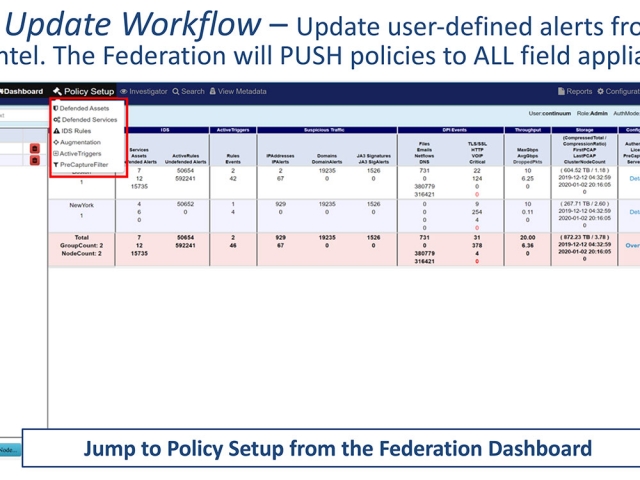
- Supplement Stealthwatch with rich data augmentation around events
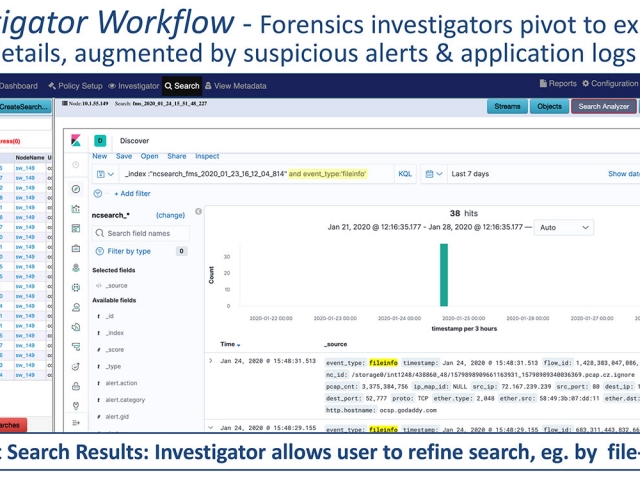
- Pivot from Stealthwatch into a full-featured Data Visualization Investigator
- “What else is going around this critical event?”
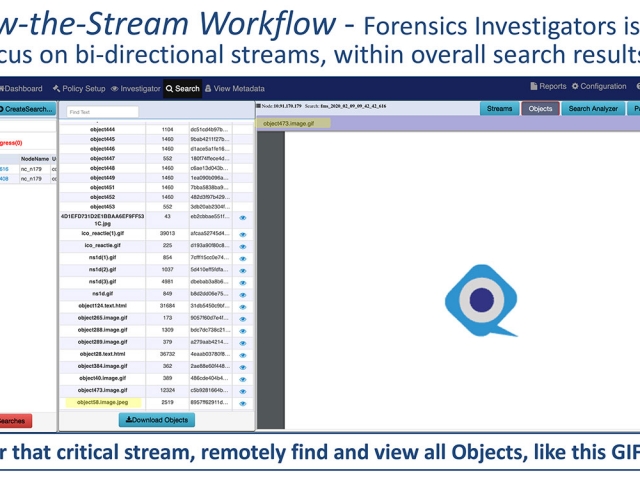
- Isolate & follow individual “Streams”, augmented with known suspicious files & activity like domains or JA3 signatures, in addition to user-defined IDS snort alerts, etc
- Leverage valuable Stealthwatch alerting policies:
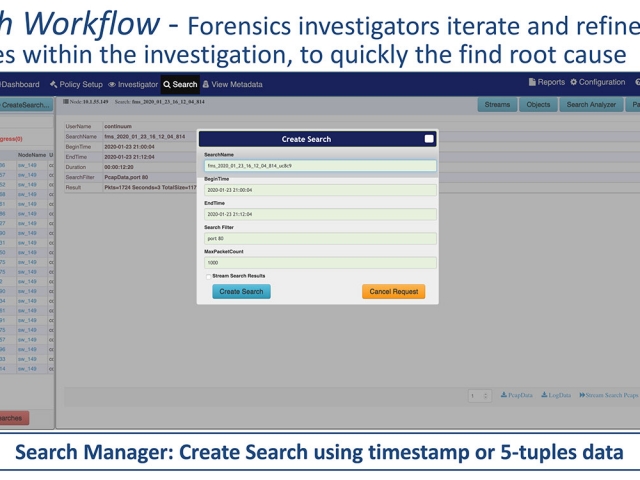
- Extend the timeline for critical data retention, beyond the lossless Capture Timeline
- Retrospective Detection: Did similar behavior occur in the past, while undetected?
- Trigger automated capture & extraction workflows