Packet Continuum, the open, massively scalable packet capture software from NextComputing, now features new and enhanced functionality, making it an even more powerful solution for lossless packet capture.
Updated UI
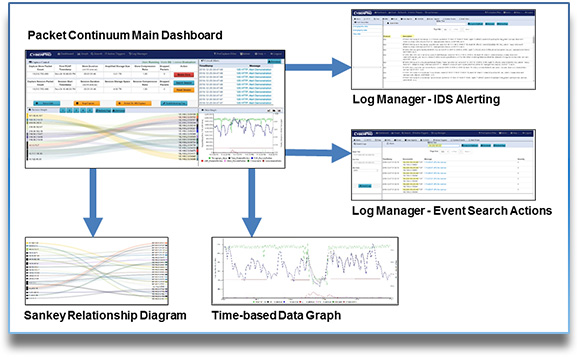
The newly optimized UI offers easier management and correlation between data sets such as PCAPs, netflow, and numerous real-time logs. New features include:
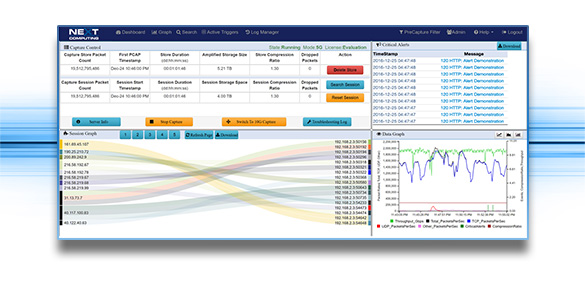
- Innovative dynamic Sankey Session Relationship Diagram shows top-talkers and SRC/DST IP/port pairs
- “One-Click” searches directly from Sankey, Time Graph or Critical Alerts log. Auto-populates the query request, making it easy to drill down quickly to find the PCAP files you need
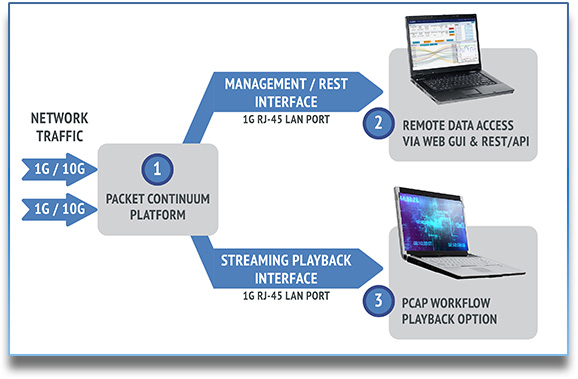
- Streaming PCAP Playback – For any PCAP query result, you can re-generate it from a 1G copper RJ45 interface, for input to any 3rd party analysis tool – just like a span/mirror port
- Now you can build scalable Cluster Capture Systems with NextComputing’s alternate form-factor platforms: Portable, Short Rackmount, and even our unique Ruggedized Portable
Powerful Log Investigator
The updated Log Investigator is a versatile tool for actionable search of log data, allowing you to quickly pivot to exactly the PCAPs or IPFIX flow records needed to identify the threat.
- The Log Investigator time stamps and provides session IDs and metadata for network events such as HTTP, files, DNS, email, user agents, TLS/SSL, Active Triggers (BPF signature), system events, and 100 Snort rules (emerging-DNS, emerging-ftp, and files).
- Logs are instantly searchable by text string, time period and/or BPF. With a single click, pivot from a critical event to PCAP session data, IPFIX record flows, or any other recorded log files.
- Export any search results (PCAP/IPFIX/Log) in open-standard file formats such as PCAP-NG and CSV for analysis in any tool you want.
Open Data Access
Open PCAP Infrastructure is key to the flexibility of the Packet Continuum software. It allows for deployment on many platforms, and the ability to integrate with any 3rd party forensics tool.
- IPFIX flow record extractions are viewable in Wireshark, in addition to extracted PCAP files
- All log files and alerts are viewable as CSV or text files in any compatible application such as MSFT Office.
- Remote access to file extractions via the Web GUI
- Open REST/API for creating customized workflows for automated Incident Response, Policy-Driven data retention, or interface to legacy analytic tools.
And more
- Now you can change pre-capture filters on-the-fly while capture is running
- Greater capacity and performance via new storage configurations
Using Packet Continuum for lossless packet capture, you have the “ground truth” about what happened during a critical event – not merely an interpretation. Combined with the open data access, smooth scale, and long timelines, Packet Continuum can support even the largest enterprise scale users – and all at a very low cost.