cyberpro 1G/10G
Low-Cost, High-Performance, Portable Packet Forensics Appliance for Network Analysts and Cyber Security Investigators
CONTACT US TODAY TO START BUILDING YOUR ORDER

CyberPro 1G/10G is the perfect tool for today’s Cyber-Hunters, IT/InfoSec specialists, and field network engineers, whose mission is to keep modern digital IP networks up and running – and fully protected. Grab this portable tool, arrive on-site, plug into the network without disrupting IT operations, and get productive fast!
Within a mobile, lightweight test appliance, CyberPro 1G/10G offers high-speed capture, indicators-of-compromise (IoC) alerting, and fully integrated analytics workflow. View long PCAP forensic timelines based on inline data compression. Find critical incidents for full-session analytics and reconstruction. CyberPro 1G/10G is ideal for network performance monitoring, cyber forensics, compliance enforcement, lawful intercept, and packet data analytics.
Download CyberPro 1G/10G Datasheet
Key Features
Lossless Capture
2 options for lossless packet capture: 1-3Gbps, 5-10Gbps
Simultaneous Search
Stream initial search results of PCAP, NetFlow, and log files to any visualization tool, even while a critical search in on-going. No more waiting for endless query response times!
Active Triggers
Use real-time, dynamic, user-defined Active Triggers and real-time analytics to rapidly direct critical PCAP data for post-processing, using any of multiple third-party open source DPI software packages, conveniently pre-installed and ready-to-use within CyberPro 1G/10G.
Extensive Logging Features
RFC anomaly logging, file download event logging, multi-protocol event / metadata logging. The Log Investigator also allows for search, cross-correlation and extraction: HTTP, files, DNS, email, user agents, NetFlow, TLS/SSL, and VOIP.
Efficient Data Management
CyberPro 1G/10G’s built-in PCAP streaming means that no third-party software will “choke” on too much data throughput during PCAP post-processing.
Unified GUI
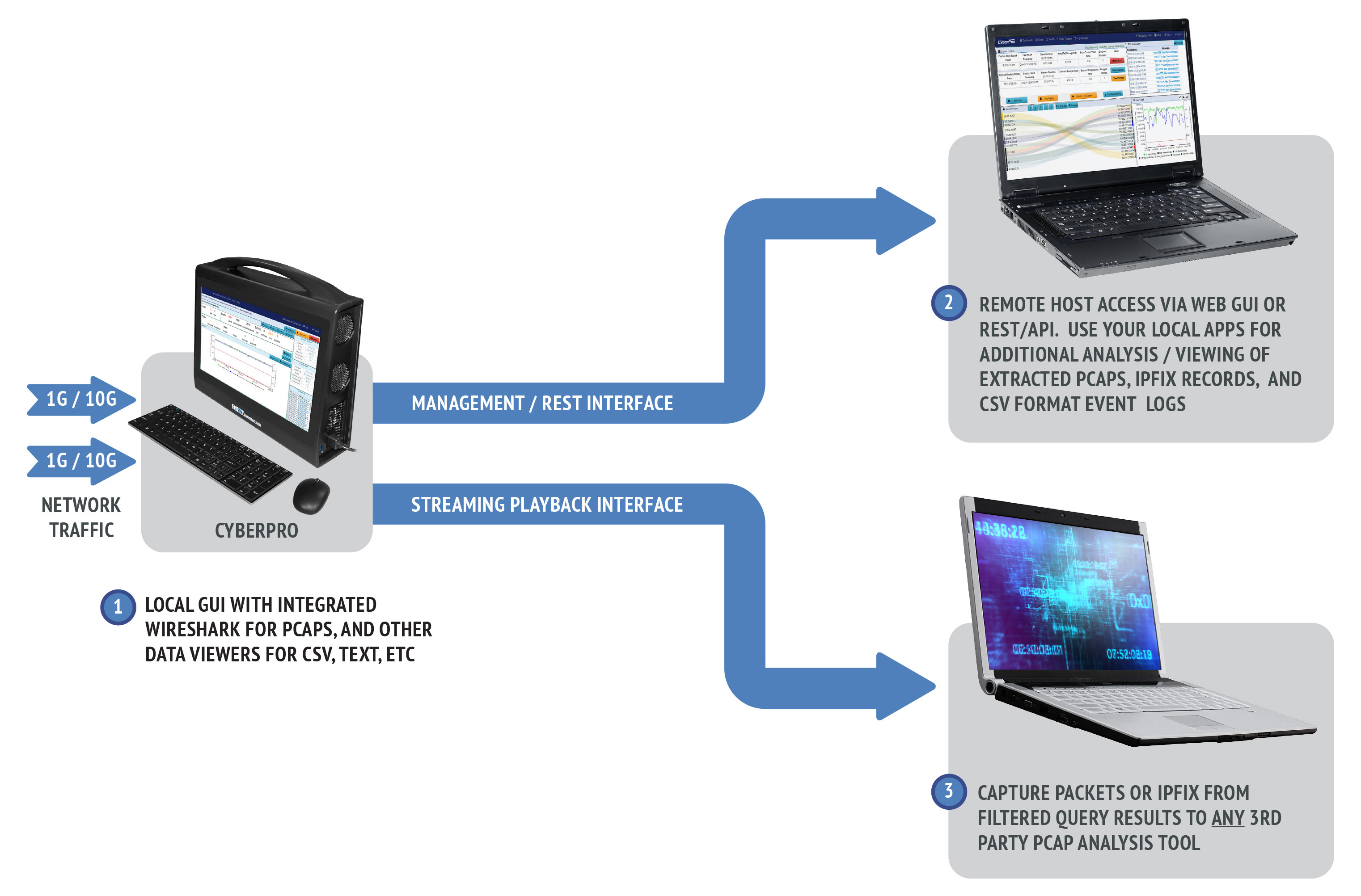
CyberPro 1G/10G’s interactive dashboard drives your investigation workflow. You control capture operations, check the scrolling alert log, and quickly extract PCAP or NetFlow data into Wireshark, or log/metadata findings results into CSV or text. Streaming results are also remotely accessible, both from a host-based WebGUI over the REST interface, and even from a streaming output port into any 3rd party forensics tool.
Visualization
Visualization is pre-installed and hard-wired into the CyberPro 1G/10G workflow, using open industry-standard data file formats: PCAP & NetFlow records open in WireShark; log searches open as CSV files; reports as TXT/RTF files.
CyberPro 1G/10G Workflow
Real-Time Analytics Features
Open up to 10 simultaneous BPF-based “Active Triggers”. Adjust them dynamically.
Log Investigator events, all with search, cross-correlation and extraction:
- HTTP
- File event logging, with file size and URL or SMTP reference
- DNS
- User agents
- TLS/SSL
- VOIP
- NetFlow
- Active Triggers (BPF signature)
- 1000 Snort rules (emerging-DNS, emerging-ftp
- System events
Log Investigator search actions:
- All logs are time-correlated with PCAPs and NetFlow data
- Text string search of logs
- NetFlow v9 record logging and search
- Choose your results for any search: PCAP, NetFlow, logs, etc.
- One-click searches auto-populate time period and search filter (BPF), based on context
CyberPro 1G/10G Open Data Access
Continuous lossless packet capture, with configurations up to 10 Gbps, into a rolling FIFO Capture Store
Searchable data recorder for NetFlow v9 records and log files
Real time indexing and alerting — with time stamping as low as 150 nanoseconds
Data compression in real time — Overall storage amplification up to 10x
Dedicated onboard Extraction Store retains all search query results, retrievable by user-defined name
Options for PCAP (or NetFlow) search results:
- View in Wireshark on the local display UI
- Remotely access from an external host via Web GUI or REST/API scripting
- Run the critical sessions over the Streaming Playback Interface to any 3rd party forensic analysis tool. Simply connect streaming playback output to the capture interface of your tool, just like a span/mirror port.
standards-based policies, with open data access
Open Source Rulesets & Data Interfaces:
- Snort/Suricata — IDS alert rulesets
- Kibana – open data visualization, compatible with the Elastic ELK stack
- JSON – used for open data-interchange and PCAP search parameters
- JA3 – TLS/SSL encrypted traffic signatures
- MD5 – File Malware signatures
- BPF — used for Active Trigger alerts, PCAP search parameters, and pre-capture filtering
- Suspicious Alerts & Augmentation – Flexible user-defined lists
- Defended Assets/Services — Flexible user-defined lists
- TAXII/STIX — pre-packaged rulesets andSuspicious Alerts, supported via structured cyber threat information
Open Data Access, with standard file formats:
- PCAP-NG forpacket data
- NetFlow Version 9 flow records
- Text/CSV/syslog for log enrichment data
Open Workflow Automation & Orchestration:
- Simplified URL-based actions, via a full-featured, mature REST/API
- Unix Command Line Interface (CLI)
- Custom Workflow Scripting
- 3rd Party Event/Data/PCAP Correlation
- Role-Based Access Control
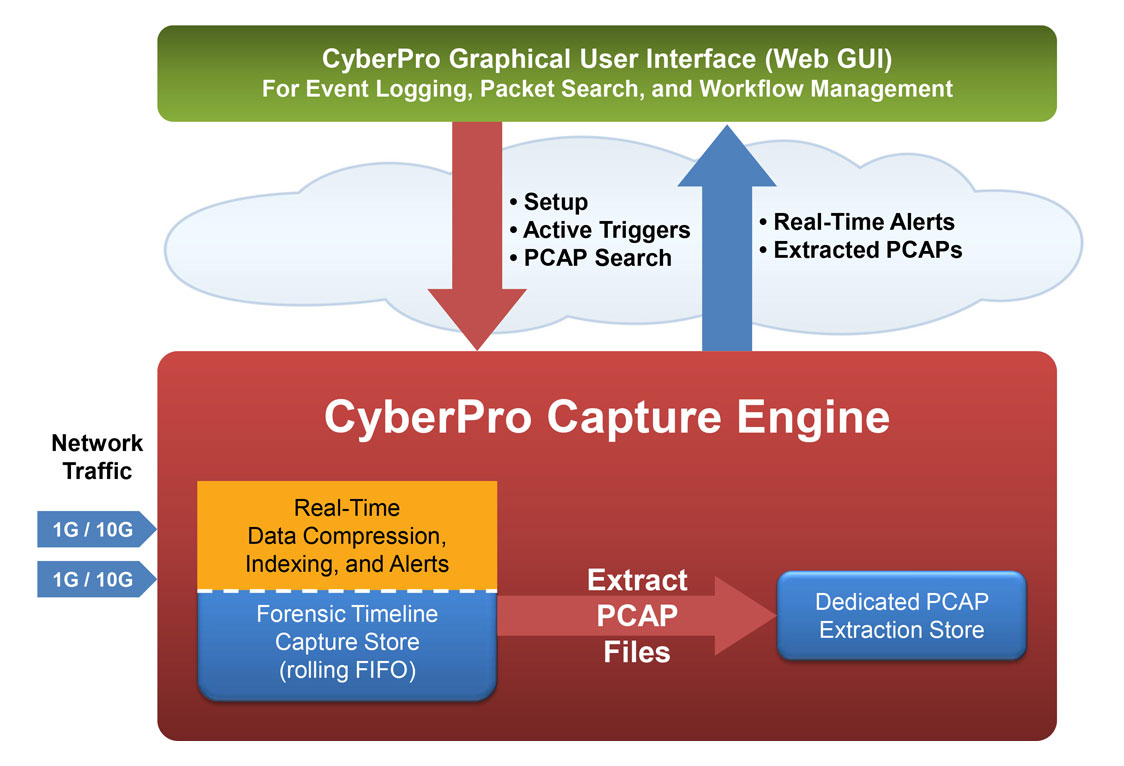
CyberPro 1G/10G Capture Process
Continuous lossless packet capture, with configurations up to 10 Gbps, into a rolling FIFO capture store. A separate extraction store retains PCAP file query results.
4-tuple indexing in real time — IP address source/destination, port source/destination — with time stamping as low as 150 nanoseconds
PCAP compression in real time — Overall storage amplification up to 20x (depending on % of captured traffic that is SSL or video)
Search PCAP data from a convenient web GUI, using easy BPF+ descriptors, immediately streaming the results from capture store to persistent extraction store.
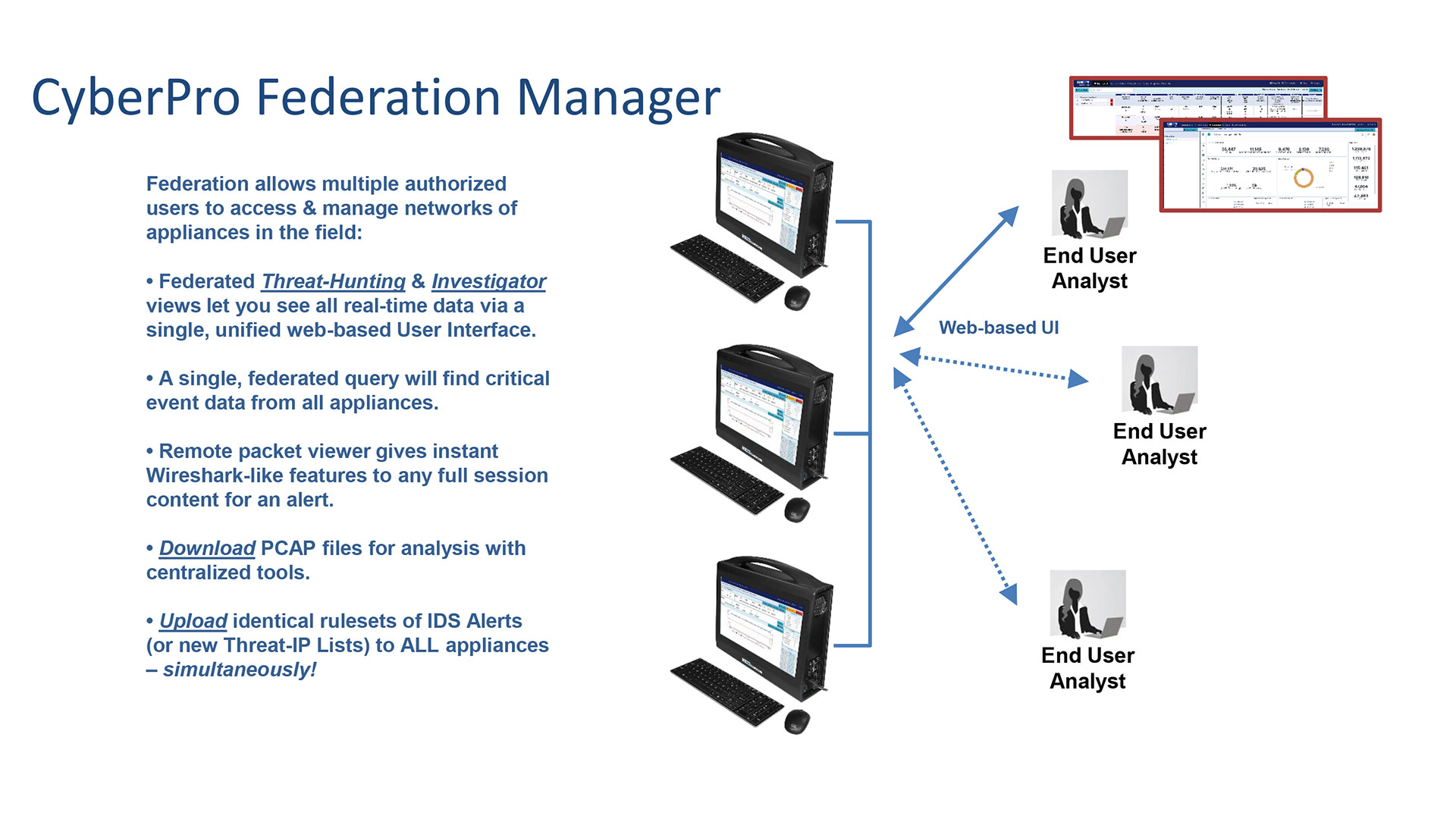
A PORTABLE BUILT FOR SCALE
The CyberPro 1G/10G works as a stand-alone appliance, and several can also joint together for even greater functionality. When you set up multiple CyberPro 1G/10G appliances to capture at different locations, a single analyst use the Federation Manager capability for integrated remote access via unified web-based UI.
Transportation Cases

Soft Case
A high-quality, padded carrying bag is included with the CyberPro 1G/10G.
- Has room and extra pockets for your keyboard, mouse, cables, and other items
- The case can be branded with your logo stitched on the front
- Fits in the overhead bin on an airplane
Compact Rugged Case
A compact rugged transport case is also available for the CyberPro 1G/10G.
- Internal foam cutout snugly holds the CyberPro 1G/10G, as well as spaces for additional accessories
- Fits in the overhead bin of some planes
- Exterior dimensions (L X W X D) 24.39″ x 19.36″ x 8.79″ (62 x 49.2 x 22.3 cm)

Full Size Rugged Case
Full size rugged case with wheels and telescoping handle.
- Internal foam cutout snugly holds the CyberPro 1G/10G, as well as spaces for additional accessories
- Can be checked as baggage, while giving you peace of mind that your system is safe
- Exterior dimensions (L X W X D) – 24.60″ x 19.70″ x 11.70″ (62.5 x 50 x 29.7 cm)

TSA Compliant
- System with accessories and soft case is small and light enough to be carry-on
- Rugged case and system can be checked as luggage without worry about damage.