CyberPro Plus 100G
High-Speed Portable Capture Appliance
CONTACT US TODAY TO START BUILDING YOUR ORDER

The CyberPro Plus 100G combines Packet Continuum with a briefcase-sized portable workstation for 10Gbps and higher continuous lossless capture with configuration options for 4x25G or 2x100G capture interfaces (100Gbps aggregate) continuous PCAP capture only and post analysis / search.
It also features massive storage and an integrated display for real-time visualization and analysis. It is an all-in-one capture / triage tool for ad-hoc threat hunting, incident response, or network troubleshooting, wherever you need to work.
Grab this portable tool, arrive on-site, plug into the network without disrupting IT operations, and get productive fast! It is the perfect tool for today’s cyber-hunters, IT/InfoSec specialists, and field network engineers whose mission is to keep modern IP networks up and running – and fully protected.
Download CyberPro Plus 100G Datasheet
Our core technology enables capture rates unheard of in such a small form factor. Just as easily as we can scale down this much performance into a compact system, CyberPro portable, cost-efficient systems can be federated at a massive scale. Federated, CyberPro systems can be used at multiple sites from a central hub for monitoring offsite, as well as providing the ability for SOC teams to update security policies remotely.
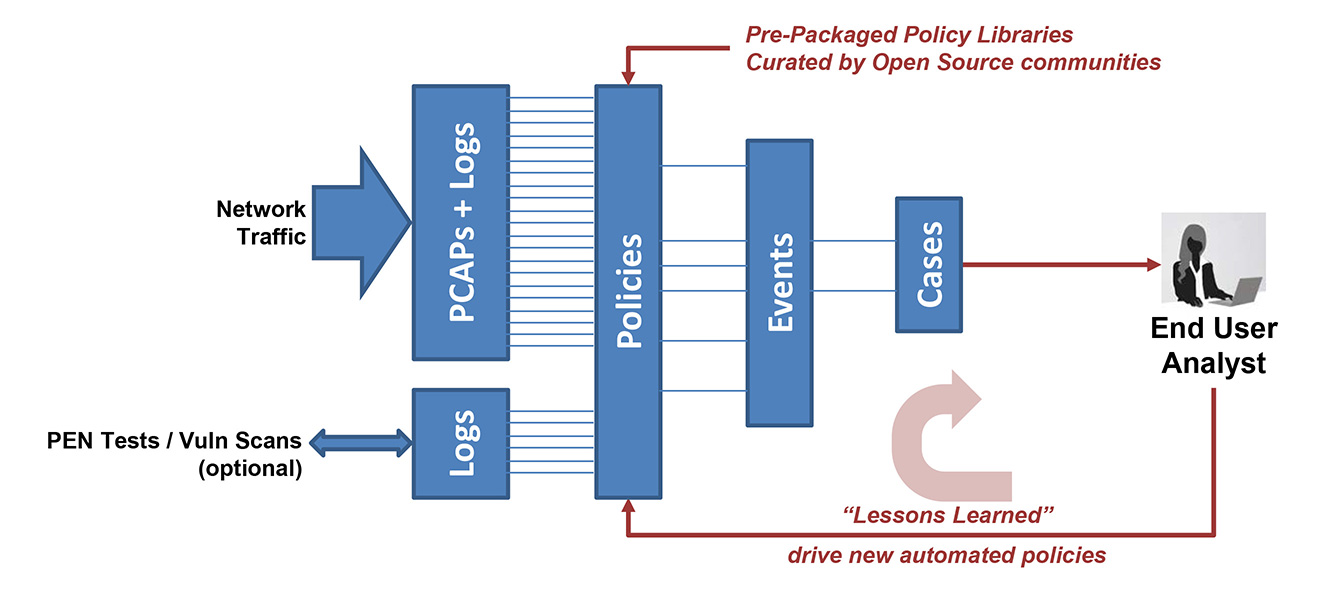
CyberPro systems are designed for standards-based policies with open data access. We leverage trusted open source communities for databases of threats and rule sets to keep you alerted of critical incidents for full-session analytics and reconstruction. Logs and data are then available in standard file formats so you can integrate them with your own preferred tools.
With a full-featured, mature REST/API, custom workflow scripting, and 3rd party event / data / PCAP correlation, CyberPro systems offer open workflow automation & orchestration.
Key Features
High-Speed Capture
10Gbps+ continuous lossless packet capture. Configuration options for 4x25G or 2x100G capture interfaces (100Gbps aggregate) continuous PCAP capture only and post analysis / search
Large Capture Timeline Storage
20-200 TB storage options via fixed or no-tools removable drives, additional storage up to 200TB
TSA-Compliant
Less than 30lbs. airline carry-on with the system and soft bag. Less than 50lbs. as a checked bag with the rugged transit case
Real-Time Packet Analytics
- Lossless packet capture at line rate
- Policy management
- Real-time alerting/detection (standards based)
- Defended assets, defended services, IDS alerts, IoC alerts, malware and event logging – at line rate
- Event-based and simultaneous PCAP session search/retrieval
- Data compression in-line
Simultaneous search
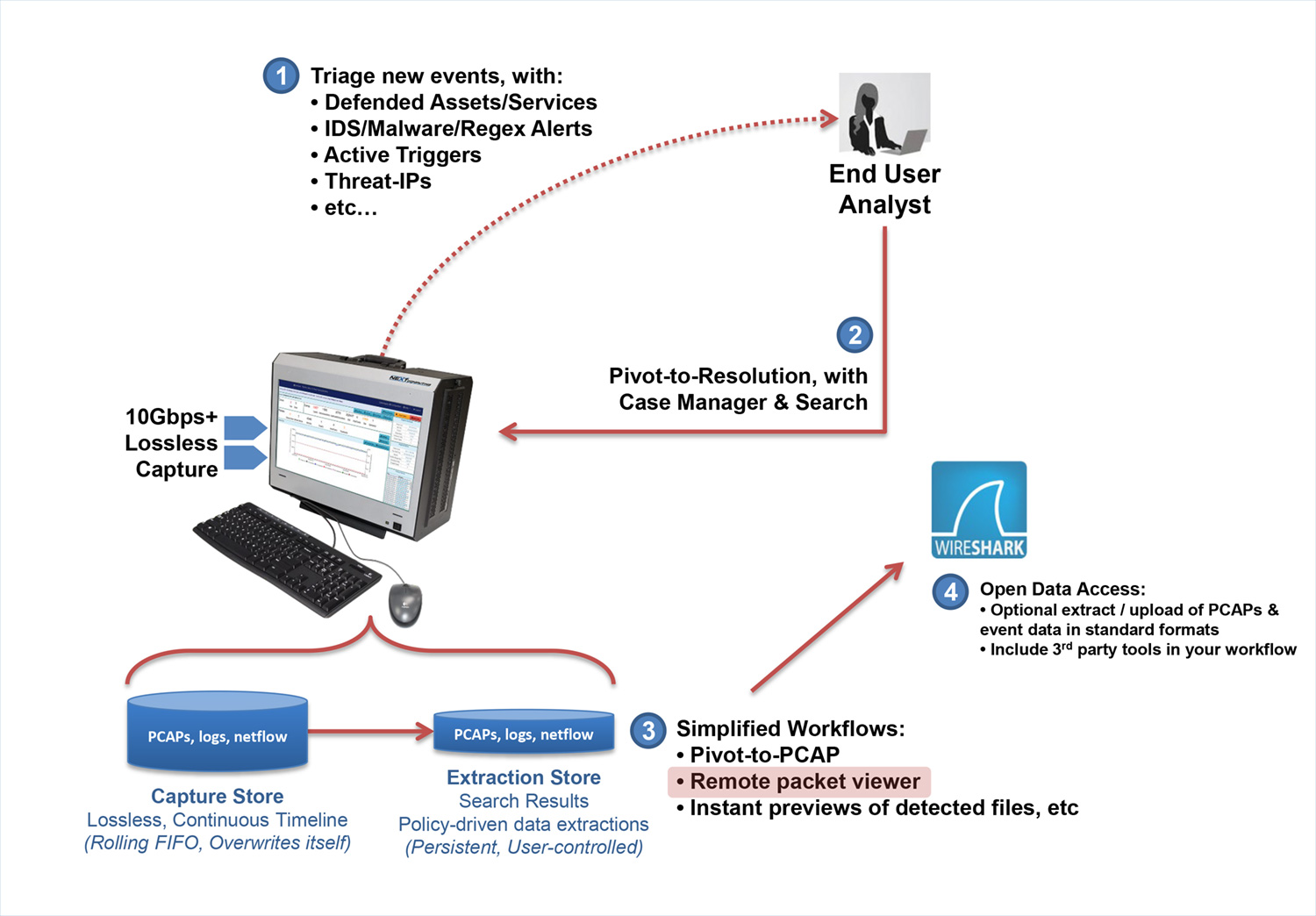
Stream initial search results of PCAP, NetFlow, and log files to any visualization tool, even while a critical search in on-going. No more waiting for endless query response times! CyberPro Plus 100G includes a unique threat-hunting feature: Use a SNORT/SURICATA rule set for “Retrospective Detection” of PCAP history. Find out if a newly discovered IoC was active in your network – even before the threat was known!
Active Triggers
Use real-time, dynamic, user-defined Active Triggers and real-time analytics to rapidly direct critical PCAP data for post-processing, using any of multiple third-party open source DPI software packages, conveniently pre-installed and ready-to-use within the system.
Extensive Logging Features
RFC anomaly logging, file download event logging, multi-protocol event / metadata logging. The Log Investigator also allows for search, cross-correlation and extraction: HTTP, files, DNS, email, user agents, NetFlow, TLS/SSL, and VOIP.
Efficient Data Management
CyberPro Plus 100G’s built-in PCAP streaming means that no third-party software will “choke” on too much data throughput during PCAP post-processing.
Unified GUI
CyberPro Plus 100G's interactive dashboard drives your investigation workflow. You control capture operations, check the scrolling alert log, and quickly extract PCAP or NetFlow data into Wireshark, or log/metadata findings results into CSV or text. Streaming results are also remotely accessible, both from a host-based WebGUI over the REST interface, and even from a streaming output port into any 3rd party forensics tool.
Visualization
Visualization is pre-installed and hard-wired into the CyberPro Plus 100G fully integrated analytics workflow, using open industry-standard data file formats: PCAP & NetFlow records open in WireShark; log searches open as CSV files; reports as TXT/RTF files.
Optional Features
- Penetration testing / security scanning tools package for more active analysis
- Carrying bag or rugged case for easier transportation
- Rugged case for securely storing removable hard drives
CyberPro Plus 100G Workflow
CyberPro Plus 100G utilizes NextComputing's Packet Continuum architecture to let you jump quickly between PCAP actions and your tools-of-choice. Gain new insight from DPI analytics tools, and generate graphical incident reports. Then iterate new Active Trigger alerts and PCAP searches, to conclude your investigation quickly.
Real-Time Analytics Features
Open simultaneous BPF-based “Active Triggers”. Adjust them dynamically.
Log Investigator events, all with search, cross-correlation and extraction:
- HTTP
- File event logging, with file size and URL or SMTP reference
- DNS
- User agents
- TLS/SSL
- VOIP
- NetFlow
- Active Triggers (BPF signature)
- 50,000 Snort rules (emerging-DNS, emerging-ftp
- 1 Million ThreatIP alerts
- System events
Log Investigator search actions:
- All logs are time-correlated with PCAPs and NetFlow data
- Text string search of logs
- NetFlow record logging and search
- Choose your results for any search: PCAP, NetFlow, logs, etc.
- One-click searches auto-populate time period and search filter (BPF), based on context
CyberPro Plus 100G Open Data Access
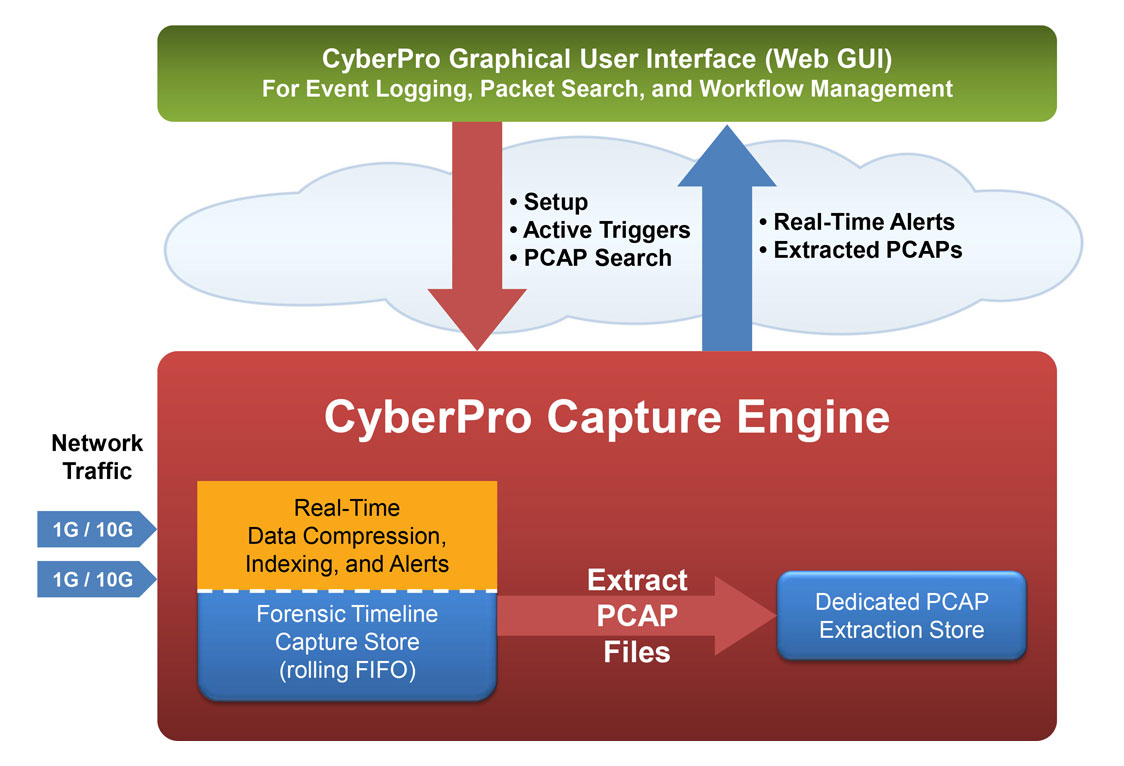
Continuous lossless packet capture, with configurations 10Gbps and higher, into a rolling FIFO Capture Store
Searchable data recorder for NetFlow records and log files
Real time indexing and alerting — with time stamping as low as 150 nanoseconds
Data compression in real time — Overall storage amplification up to 10x
Dedicated onboard Extraction Store retains all search query results, retrievable by user-defined name
Options for PCAP (or NetFlow) search results:
- View in Wireshark on the local display UI
- Remotely access from an external host via Web GUI or REST/API scripting
- Run the critical sessions over the Streaming Playback Interface to any 3rd party forensic analysis tool. Simply connect streaming playback output to the capture interface of your tool, just like a span/mirror port.
standards-based policies, with open data access
Open Source Rulesets & Data Interfaces:
- Snort/Suricata — IDS alert rulesets
- Kibana – open data visualization, compatible with the Elastic ELK stack
- JSON – used for open data-interchange and PCAP search parameters
- JA3 – TLS/SSL encrypted traffic signatures
- MD5 – File Malware signatures
- BPF — used for Active Trigger alerts, PCAP search parameters, and pre-capture filtering
- Suspicious Alerts & Augmentation – Flexible user-defined lists
- Defended Assets/Services — Flexible user-defined lists
- TAXII/STIX — pre-packaged rulesets andSuspicious Alerts, supported via structured cyber threat information
Open Data Access, with standard file formats:
- PCAP-NG forpacket data
- NetFlow Version 9 flow records
- Text/CSV/syslog for log enrichment data
Open Workflow Automation & Orchestration:
- Simplified URL-based actions, via a full-featured, mature REST/API
- Unix Command Line Interface (CLI)
- Custom Workflow Scripting
- 3rd Party Event/Data/PCAP Correlation
- Role-Based Access Control
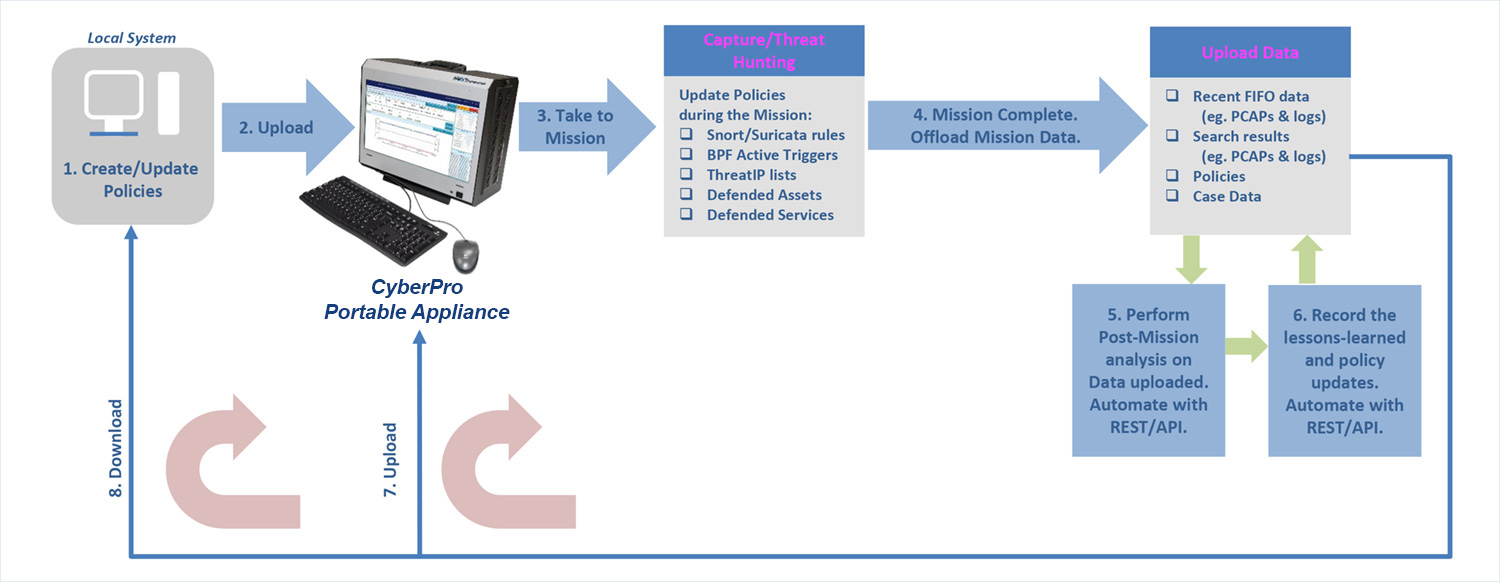
A PORTABLE CASE-MANAGEMENT FRAMEWORK
- Cyber team will create/update initial policies on a local system.
- Before each mission, upload these policies to a CyberPro Plus 100G for use during the mission.
- During the mission, Capture / Threat Hunting. Update real-time alerting policies, as required.
- After the mission, offload data that includes marked case data, current policies, and last Capture Store / Extraction Store data.
- Perform Post-Mission analysis on the data uploaded in step 4. Automate the post-mission analysis operations by utilizing the NextComputing REST/API.
- Record the set of lessons learned and policy updates.
- To iterate for the next mission, go to Step 2: upload and share new Policies with the CyberPro appliance(s).
- Download any updated policies to the local system, as needed to update and upload again.
CyberPro Plus 100G Capture Process
Continuous lossless packet capture into a rolling FIFO capture store. A separate extraction store retains PCAP file query results.
4-tuple indexing in real time — IP address source/destination, port source/destination — with time stamping as low as 150 nanoseconds
PCAP compression in real time — Overall storage amplification up to 20x (depending on % of captured traffic that is SSL or video)
Search PCAP data from a convenient web GUI, using easy BPF+ descriptors, immediately streaming the results from capture store to persistent extraction store.
A PORTABLE BUILT FOR SCALE
The portable CyberPro Plus 100G works as a stand-alone appliance, and several can also joint together for even greater functionality.
When you require additional capture timeline in the field, configure and connect several other CyberPro Plus 100G appliances as "Cluster Nodes". NextComputing's unique MapReduce software framework spreads the processing load, so long timelines are as quick to search as with a single appliance.
When you set up multiple CyberPro Plus 100G appliances to capture at different locations, a single analyst use the Federation Manager capability for integrated remote access via unified web-based UI.
When you have ad-hoc requirements for lossless capture of very high capture rates, the Federation Manager will also do the job. When high-rate traffic is split (using a Network Packet Broker or Load Balancer) into multiple 10G lines, each CyberPro Plus 100G can capture up to 10Gbps of the load or higher, and an end-user analyst will see all traffic integrated within the Federated UI. With Federation Manager features, it does not matter where the packets are located: You can make a single query for the whole traffic contents, and the results will be combined from all appliances into a single set of PCAP file results.
Transportation

Soft Case
A high-quality, padded carrying bag is included with the CyberPro.
- Has room and extra pockets for your keyboard, mouse, cables, and other items
- The case can be branded with your logo stitched on the front
- Fits in the overhead bin on an airplane

Full Size Rugged Case
Full size rugged case with wheels and telescoping handle.
- Internal foam cutout snugly holds the CyberPro, as well as spaces for additional accessories
- Can be checked as baggage, while giving you peace of mind that your system is safe
- Exterior dimensions (L X W X D) – 24.60″ x 19.70″ x 11.70″ (62.5 x 50 x 29.7 cm)

Rugged, Secure HDD Case
Compact, lockable case for removable hard drives and SFP/SFP+ modules
- Holds up to (16) quick-time removable 2.5” drives AND
- Up to (8) SFP/SFP+ modules
- Internal security tray
- 16.44" L x 13.00" W x 6.82" D (41.8 x 33 x 17.3 cm)

TSA Compliant
- System with accessories and soft case is < 30lbs and small enough to be an airline carry-on
- Rugged case and system are < 50lbs, which can be checked as luggage without worry about damage.