Packet Continuum 100G+
CONTACT US TODAY TO START BUILDING YOUR ORDER

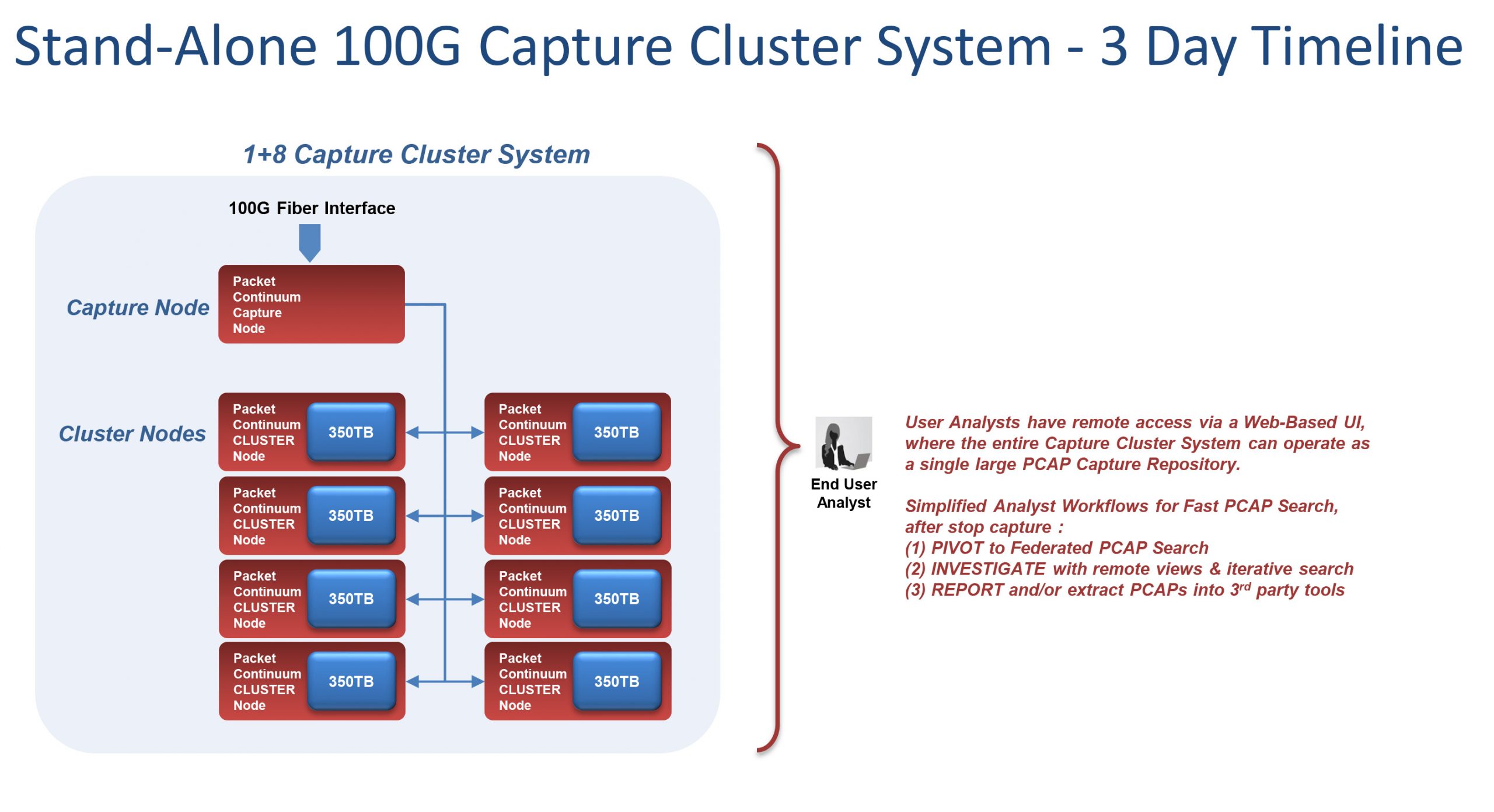
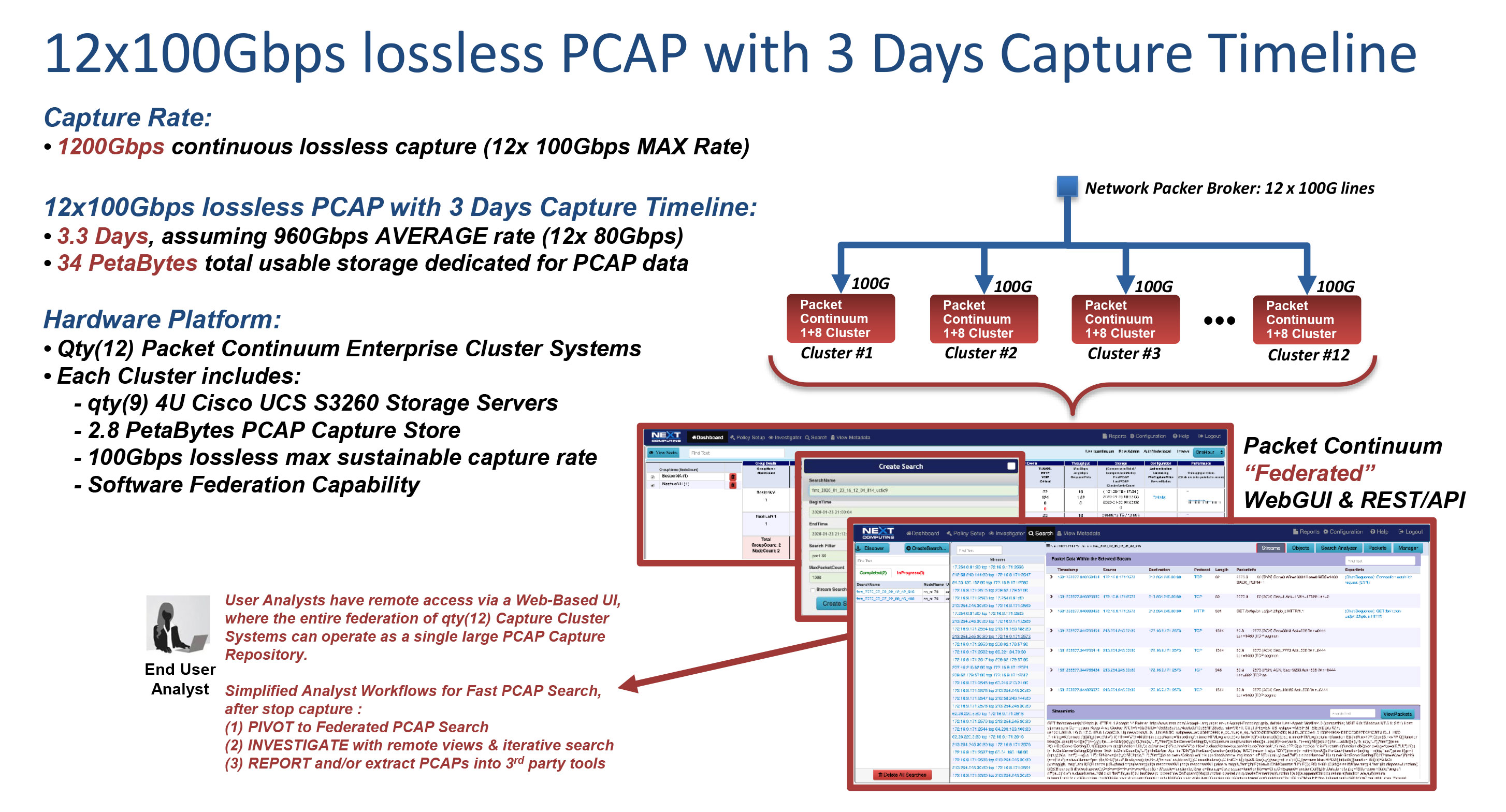
The Packet Continuum 100G+ offers 100G packet capture and higher for recording and search of PCAP data on large scale networks driven by 5G.
Through our partnership with Cisco, the Packet Continuum 100G+ utilizes our unique packet capture technology and the innovative design of the Cisco UCS S3260 server.
- Utilizes common platform enterprise-class servers
- No proprietary hardware – Direct support from the server vendor (Cisco)
- Standard Linux (CentOS or Red Hat)
- Standard Cisco IMC / IPMI remote interface, for lights-out data center operation
- Scalable/Adjustable for more/less timeline storage
- Scalable/Adjustable for multiple use cases
- Aggregate at a single location
- Or, Federate across multiple data centers or mobile PoP sites
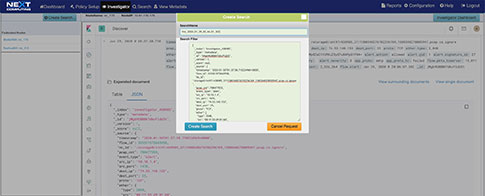
- Fast-response PCAP queries (with 100G limitations, eg stop capture), with analyst workflows for:
- Web-based UI with remote packet viewers and PCAP analyzer/investigator
- Pivot-to-PCAP from BFP and/or timeline search
Key Features
Utilizes common platform enterprise-class servers
- No proprietary hardware – Direct support from the server vendor (Cisco)
- Standard Linux (CentOS or Red Hat)
- Standard Cisco IMC / IPMI remote interface, for lights-out data center operation
100Gbps+ continuous lossless packet capture
- Aggregate at a single location
- Or, Federate across multiple data centers or mobile PoP sites
Large Capture Timeline Storage
Scalable to many Petabytes of PCAP storage with fast retrieval
Real-Time Packet Analytics
- Lossless packet capture at line rate
- Data compression in-line for packets in the clear. Compression ratios depending on packet payloads
Simultaneous search
Fast-response PCAP queries (with 100G limitations, eg stop capture), with analyst workflows for:
- BPF Filter and timeline based simultaneous PCAP session search/retrieval
- Web-based UI with remote packet viewers and PCAP analyzer/investigator
- Pivot-to-PCAP from BFP and/or timeline search
Active Triggers
Use real-time, dynamic, user-defined Active Triggers and real-time analytics to rapidly direct critical PCAP data for post-processing, using any of multiple third-party open source DPI software packages, conveniently pre-installed and ready-to-use within the system.
Unified GUI
- Interactive dashboard drives your investigation PCAPs from search with our PacketViewer
- REST API and Web-based UI with remote packet viewers and PCAP analyzer/investigator
- Pivot-to-PCAP from BFP and/or timeline search
Packet Continuum 100G+ Workflow
Real-Time Analytics Features
Open simultaneous BPF-based “Active Triggers”. Adjust them dynamically.
Log Investigator events, all with search, cross-correlation and extraction:
- HTTP
- File event logging, with file size and URL or SMTP reference
- DNS
- User agents
- TLS/SSL
- VOIP
- NetFlow
- Active Triggers (BPF signature)
- 50,000 Snort rules (emerging-DNS, emerging-ftp
- 1 Million ThreatIP alerts
- System events
Log Investigator search actions:
- All logs are time-correlated with PCAPs and NetFlow data
- Text string search of logs
- NetFlow record logging and search
- Choose your results for any search: PCAP, NetFlow, logs, etc.
- One-click searches auto-populate time period and search filter (BPF), based on context