Rapid Triage
Real-time policy alerts, based on open-standards curated by open-source communities, allow analysts to rapidly triage network anomaly and security IoC events.
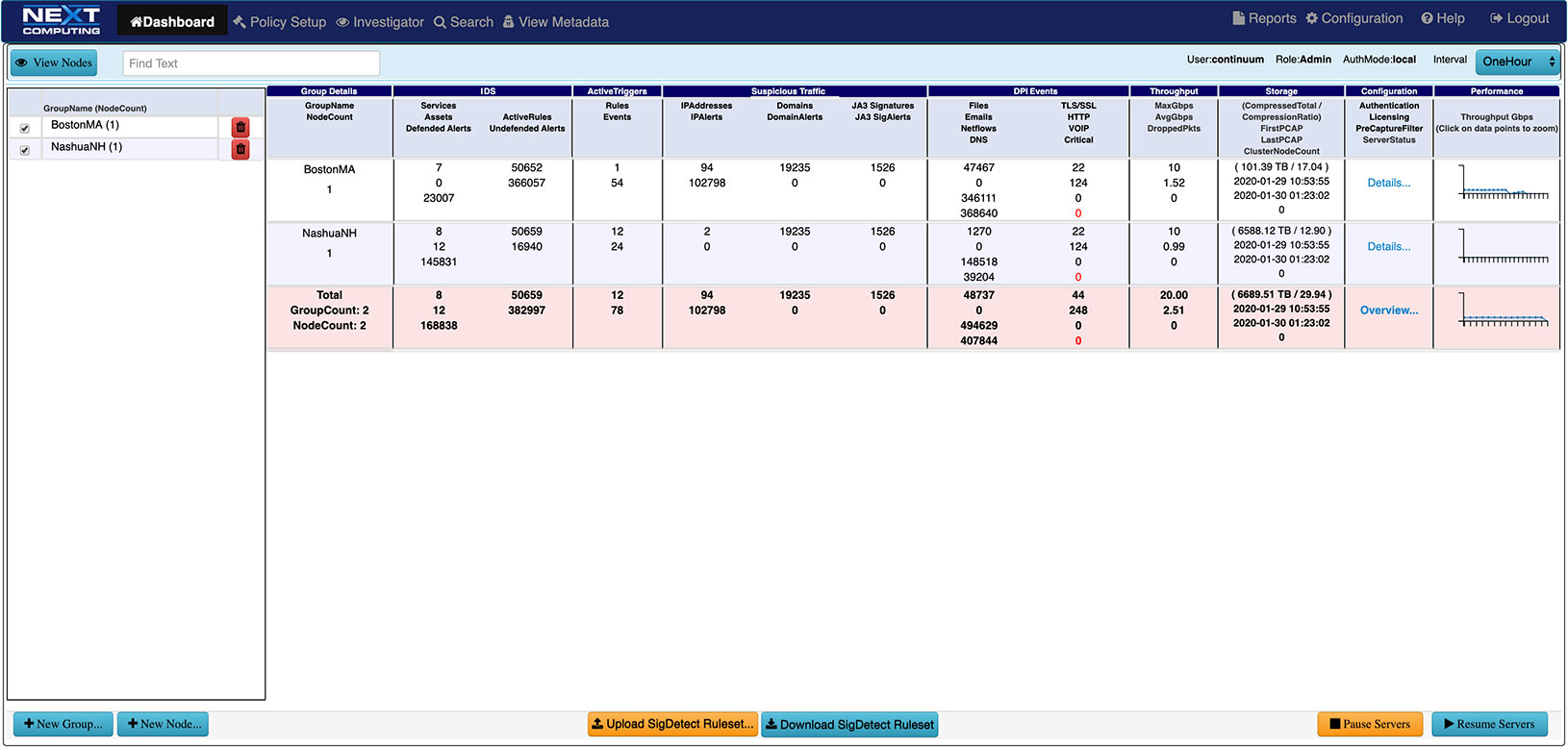
ANALYST OPERATIONS DASHBOARDS
- Prioritizes real-time Indicators of Compromise (IoC) & Incident Response actions
- Automated mapping of IoC events to adversary behavior in the Kill Chain
- One-click searches from the dashboard
- Live updates to the Capture Data Graph, and Critical Alerts List

Policy Alerts DRIVE INCIDENT RESPONSE
- Start with red-flag behavior, like Exfiltration or suspect C&C activity
- One-click search to show IoCs for each step in the Kill Chain
- Then click thru for all correlated PCAP data

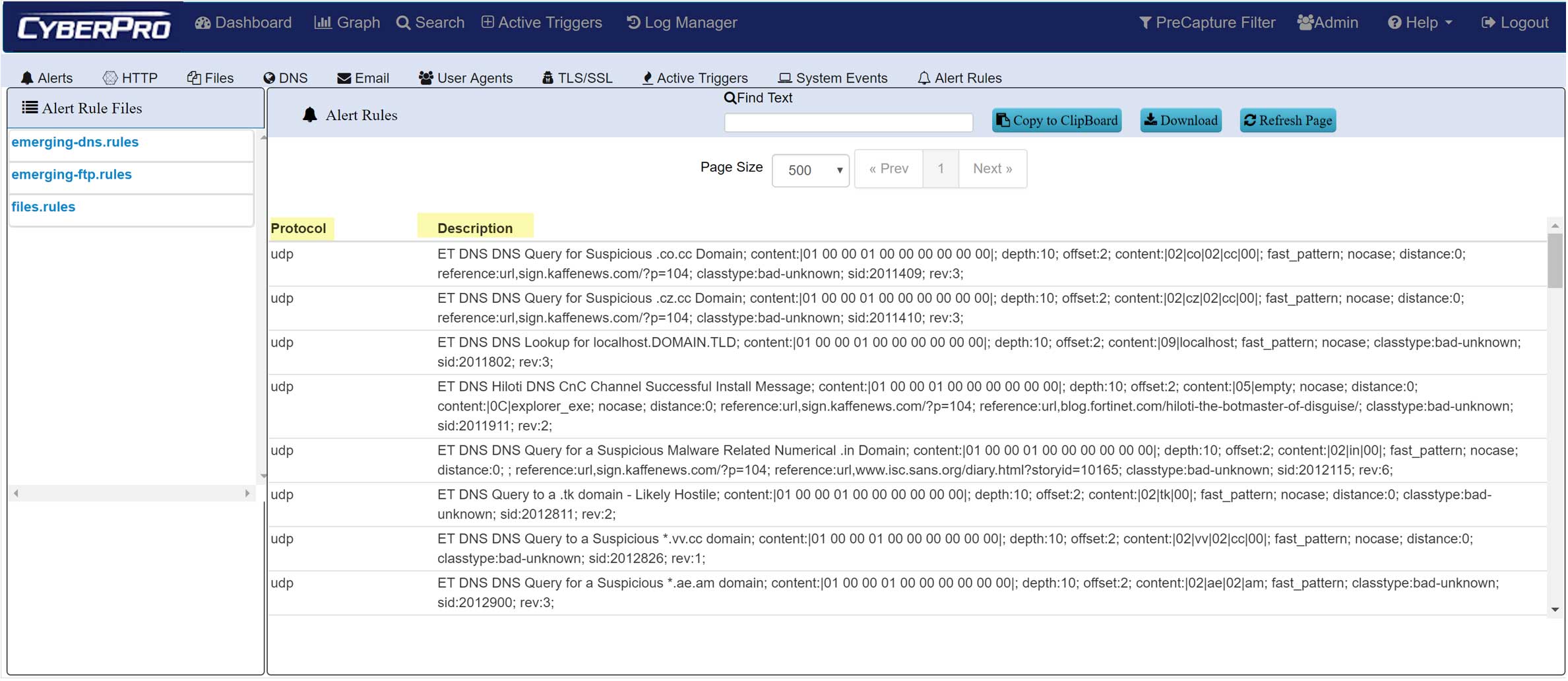
Threat Hunting - IOC POLICIES
- SNORT/SURICATA Rule Sets
- Threat IPs and Suspicious Traffic alerts
- Defended Assets & Services
- Active Triggers (BPF-based)

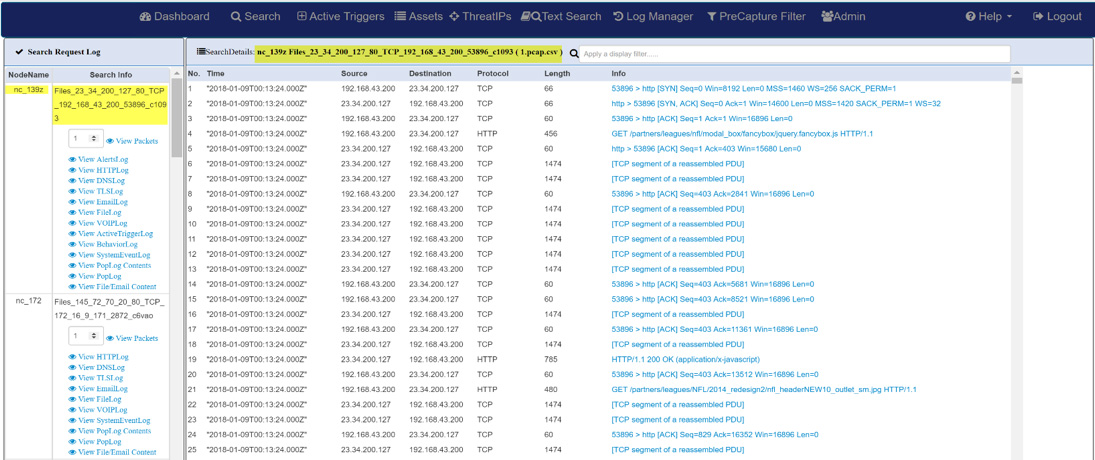
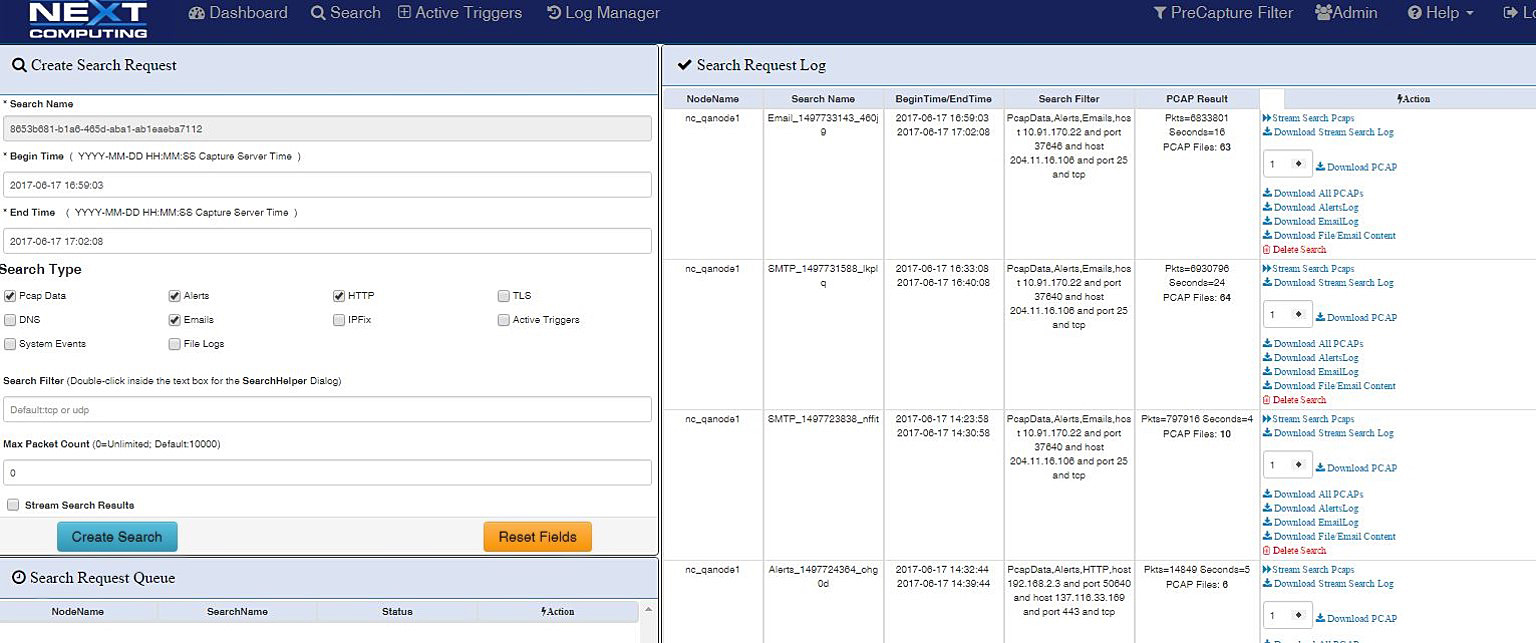
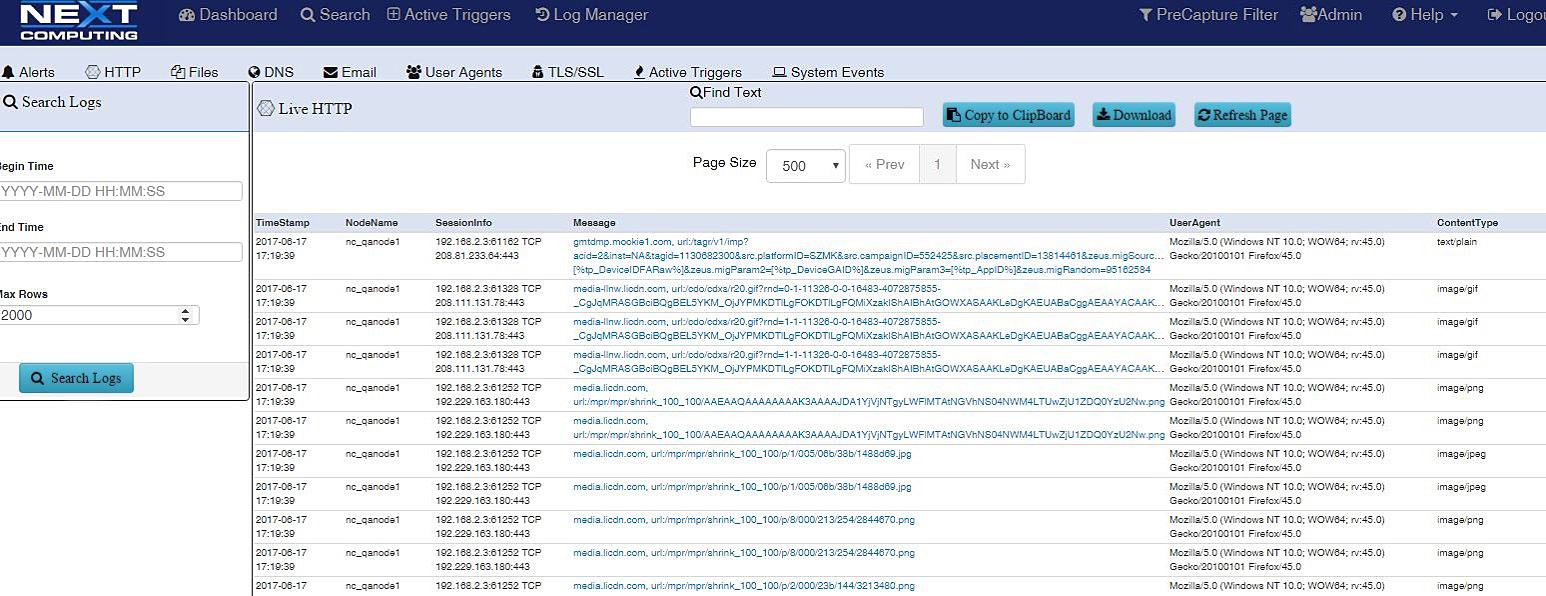
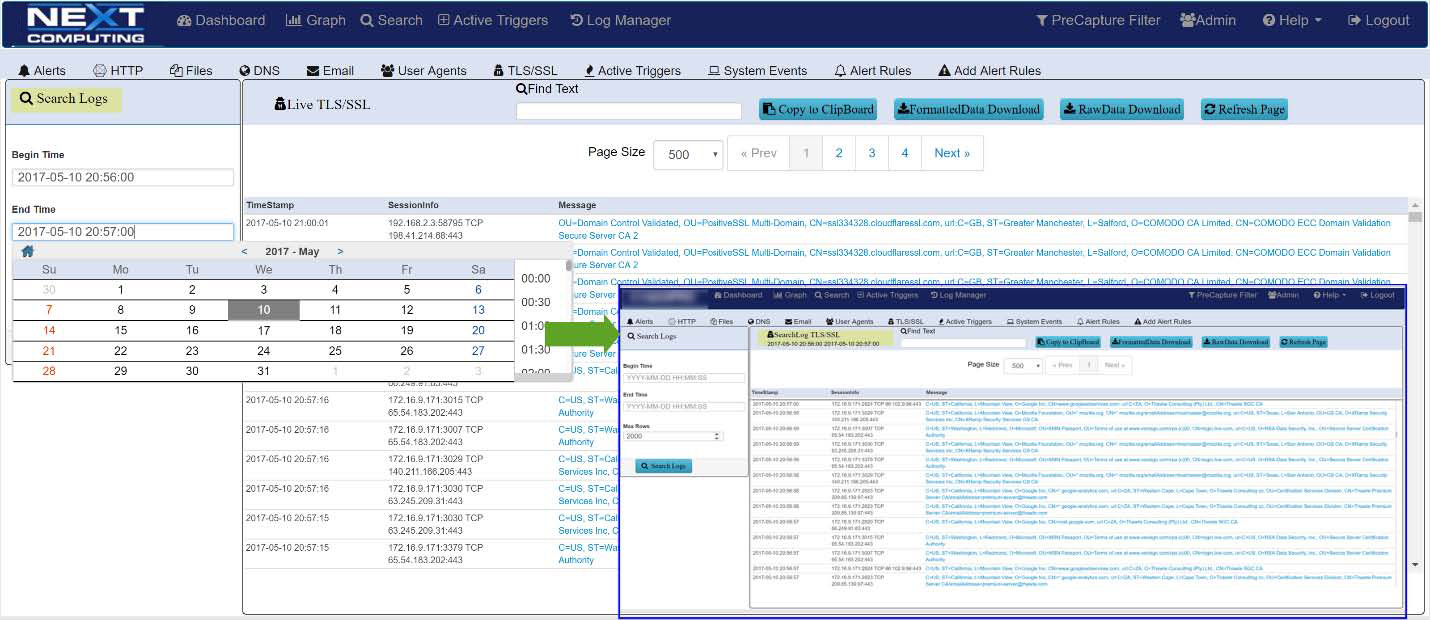
Log Investigator - Event Search Actions
- One-click time-based search
- Text-based search of alerts
- All IoC events correlated with PCAPs, NetFlow records, and sessionized logs
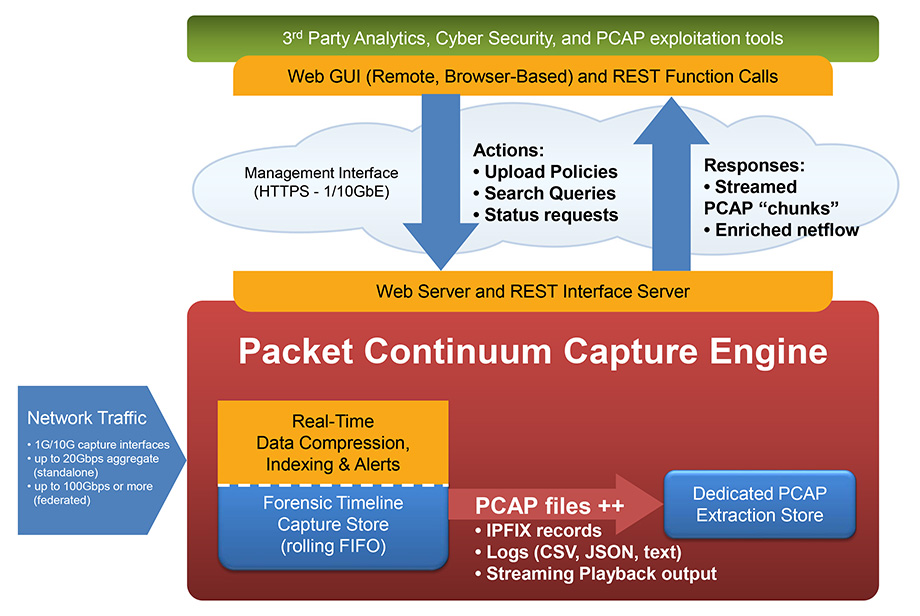
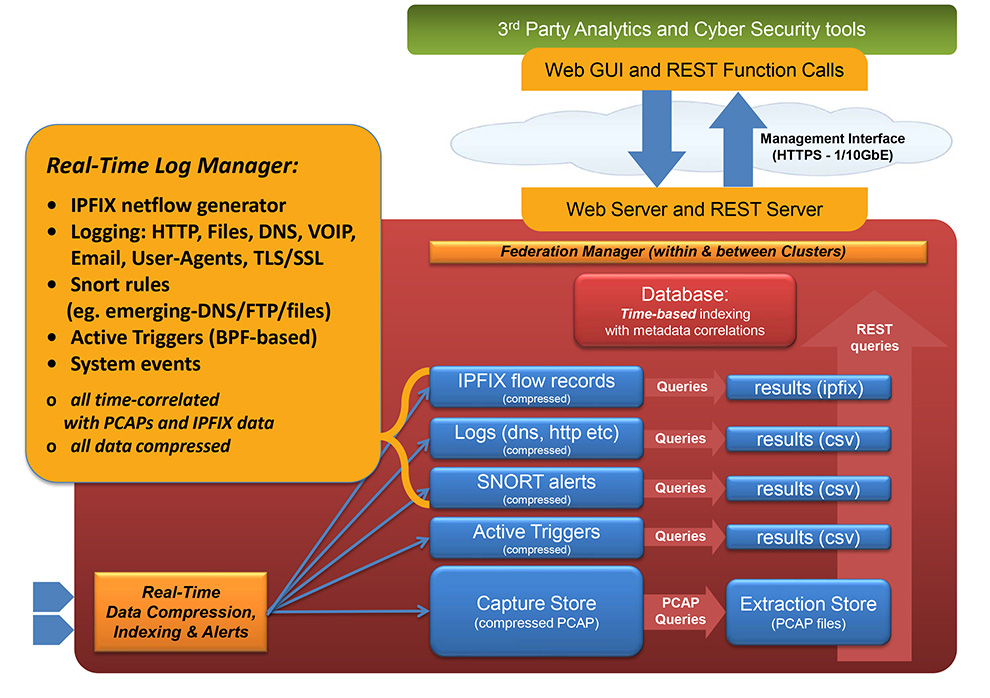
LOSSLESS PACKET Capture with DATA ENRICHMENT
The immutable ground truth of any critical event – not merely an interpretation. Packet Continuum provides a performance guarantee of sustained lossless capture rate, for a set of real-time packet analytics (Threat Hunting / Log Investigator) functions, and a specified number of Packet Continuum cluster nodes. This means a deterministic guarantee to capture every packet under real world conditions, not just a “best effort” attempt.
- Lossless packet capture from 1Gbps to 100+Gbps telco interfaces
- Remote Packet Viewer for wireshark details about packets-in-place at remote sites
- Time stamping of 150 nanoseconds
- Real-time IDS alert configurator generates event logs for HTTP, Files, DNS, email, user agents, TLS/SSL, VOIP – all cross-correlated with PCAP & NetFlow V9 records
- Threat Hunting / Log Investigator advanced packet analytics options include real-time event logging & cross-correlation
- 1000s of Snort/Suricate rules, from prepackaged libraries and user-defined rulesets
- Sessionaized logging for Email, HTTP, SMTP, Files, DNS, User Agents, TLS/SSL
- NetFlow Version 9 flow record logging and search
- Scalable architecture to meet your speed and/or analytics requirements
- Federate multiple cluster-based capture systems, for global visibility and PCAP retrieval
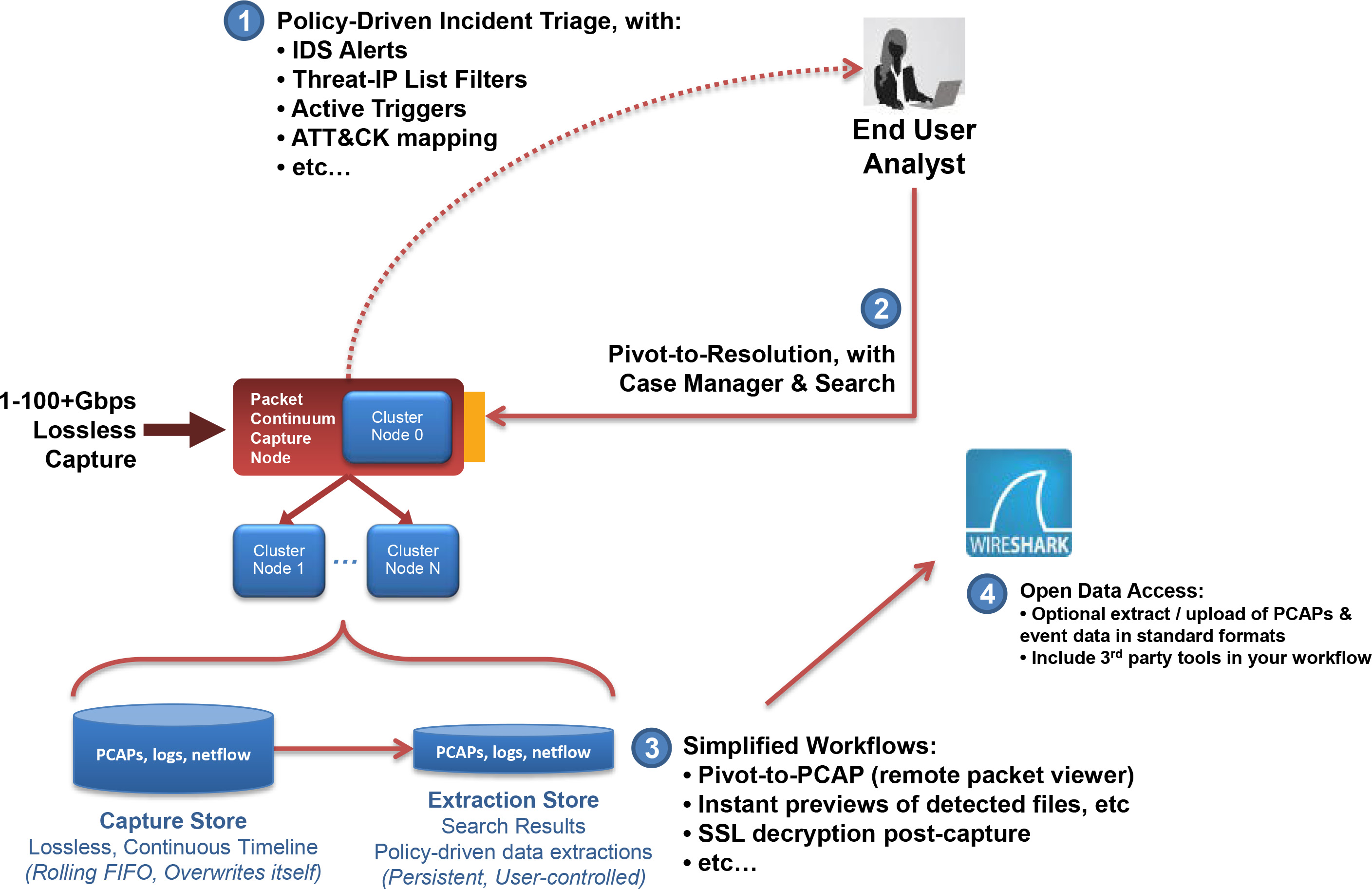
Simplified Workflow
Packet Continuum simplifies your workflow by integrating endpoint behavior and network signature visibility and DPI with a simple pivot to the sessionized network data, enriched metadata and file recovery. Mitigate the nearly 2/3 of breaches per incident that are easy to catch, like administrative issues, by implementing effective, basic cyber practice policies by tracking user agent signature characteristics, email and file exfiltration.
POLICY-DRIVEN WORKFLOW
The Packet Continuum user interface (and programmatic REST/API) integrates Policy Management, Threat Hunting / Log Management, Forensic Investigation, and Open Data Access.
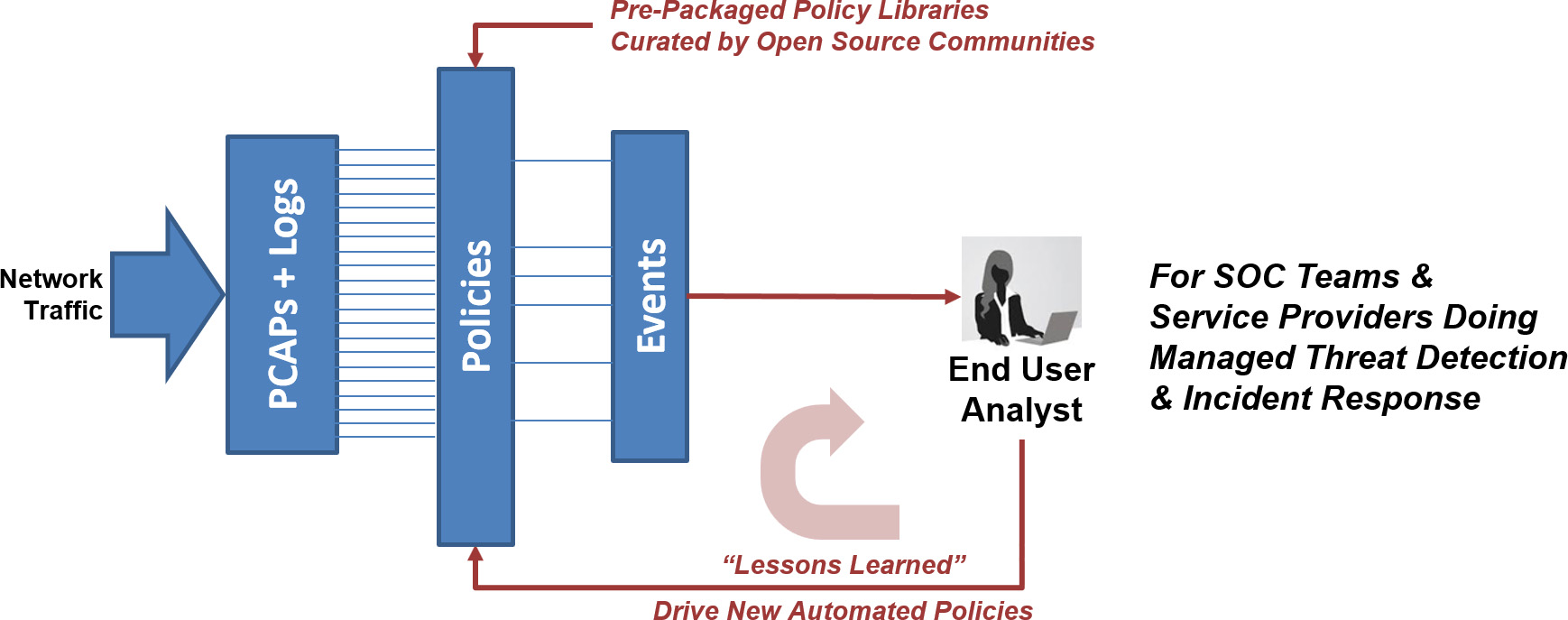
An integrated Threat Hunting / Log Investigator gives visibility to analysts about critical events, and allows quick drill-down to full session logs and full PCAP file content. Real-time IoC Policy Management comes with pre-packaged ruleset libraries, and allows SOC teams to design and upload their own rule sets, including
- IDS rulesets
- Malware rulesets
- ThreatIP lists
- Suspicious domain lists
- Suspicious SSL signatures
- Defended assets
- Defended services
- BPF-based Active Triggers
Triage critical events with real-time alerting policies.
All policies generation logs/metadata which are compressed, correlated, and instantly searchable.
All policies integrate within a full-featured Threat Hunting / Log Management User Interface.
Packet Continuum facilitates the “Spiral-Model” methodology for effective forensic investigations.
Standards-Based Policies
Open Source Rulesets & Data Interfaces:
- Snort/Suricata — IDS alert rulesets
- Kibana – open data visualization, compatible with the Elastic ELK stack
- JSON – used for open data-interchange and PCAP search parameters
- JA3 – TLS/SSL encrypted traffic signatures
- MD5 – File Malware signatures
- BPF — used for Active Trigger alerts, PCAP search parameters, and pre-capture filtering
- Suspicious Alerts & Augmentation – Flexible user-defined lists
- BPF — User-defined Active Trigger alerts
- Defended Assets/Services — Flexible user-defined lists
- TAXII/STIX — pre-packaged rulesets and Suspicious Alerts, supported via structured cyber threat information
Open Data Access, with standard file formats:
- PCAP-NG for packet data
- NetFlow Version 9 flow records
- Text/CSV/syslog for log enrichment data
Open Workflow Automation & Orchestration:
- Simplified URL-based actions, via a full-featured, mature REST/API
- Unix Command Line Interface (CLI)Full-featured, mature REST/API
- Custom Workflow Scripting
- 3rd Party Event/Data/PCAP Correlation
- Role-based Access Control
labor / cost reduction
Combine zero day alerting and pivot for analysis/mitigation and historical post breach forensics analysis including “cyber-espionage,” “point-of-sale intrusions,” and “privilege misuse.” Reduce the cost of network recording software and systems needed for medium and large networks.
Reduce labor needed for identification of indicators of compromise with an easy process to pivot to sessionized data / enriched meta data and reconstruct email and files for review.
Multiple features enable labor / cost reduction including
- Real-time Data Compression: In-line packet compression is transparent to the user. All packets are compressed as they are captured, and all extracted PCAP files are decompressed. Overall storage amplification up to 10x (depending on percentage of traffic with SSL encrypted or compressed packet payloads)
- Cluster architecture leverages CPU power over many servers for super-fast query response, while enabling low-cost local-attached storage on a massive scale. Forensic timelines smoothly scale over days, weeks & months.
- Massive queries over large timelines respond quickly, even as the timeline increases
- Federated search across multiple Packet Continuum appliances at diverse geographic locations, without any “concentrators” required
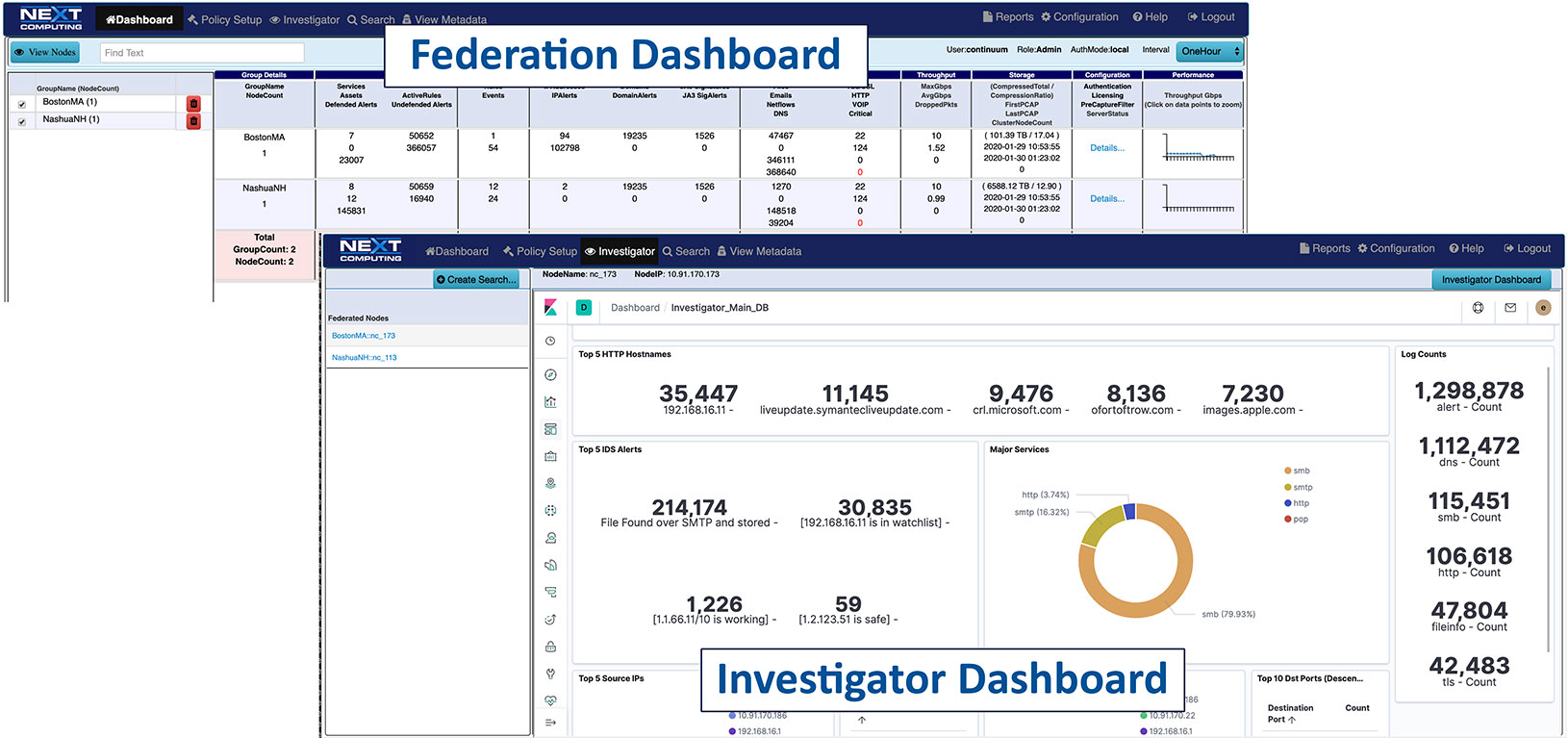
Federation manager
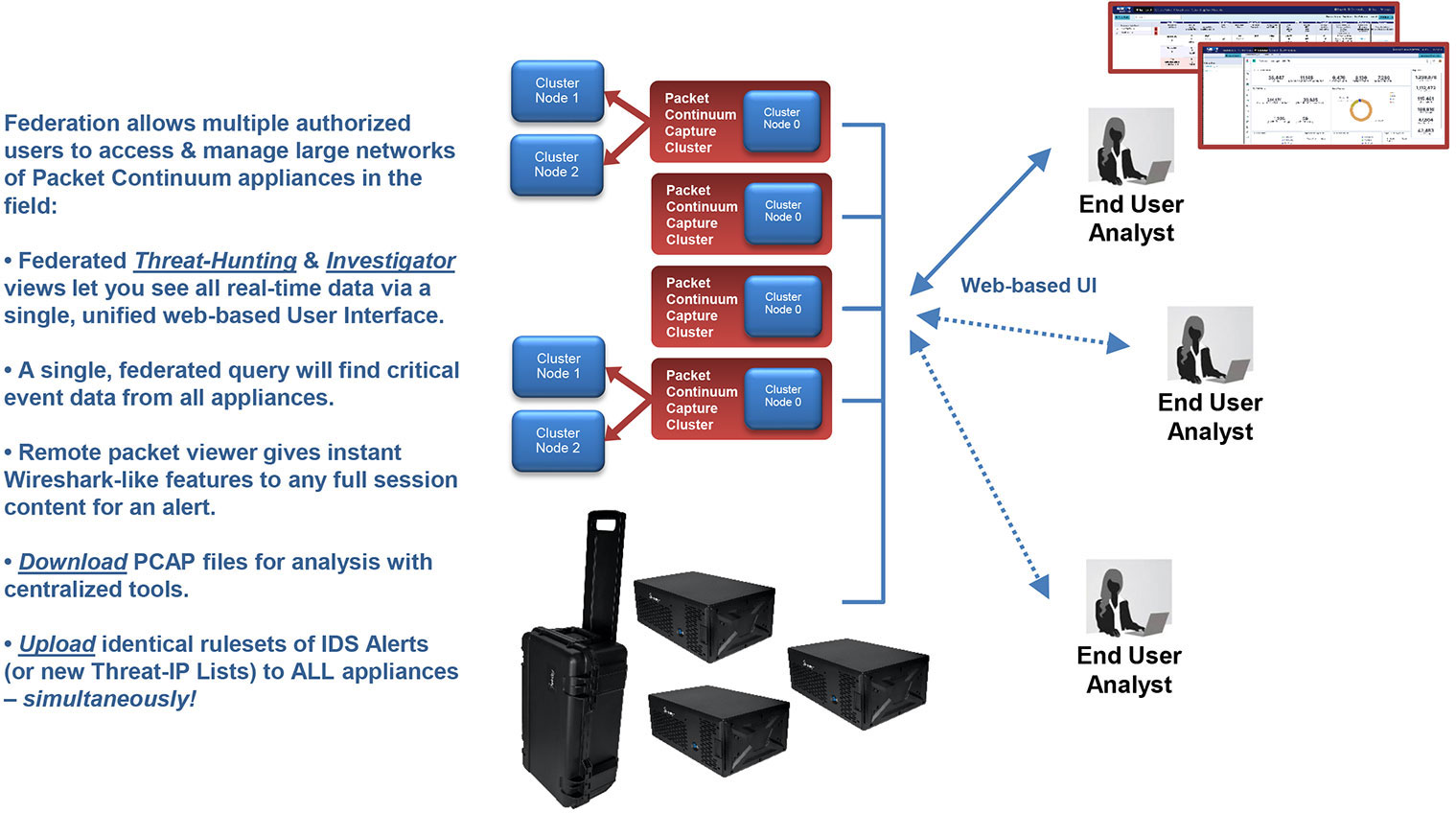
Packet Continuum's Federation Manager allows you to federate multiple capture appliances in multiple locations.
- Remote control capability via browser and REST API
- Federated View of all data
- Map-reduced framework to extract out packets, DPI data and logs across federation
Federation manager dashboard for easy identification of Packet Continuum appliances/clusters that can even be in different physical locations. Your enterprise network can identify the IP address of each appliance and federate together for a single pane of glass view of all network data.
Federated search across PCAP data, DPI log data and flow records, as well as email text and files for reconstruction.
Federated list of SMTP email sessions with time stamp, capture node location, session information, and SMTP email address, sender, and receiver. The user can click to obtain full session packets, extract email text, subject and reconstruct attachments in their original mime format, PDF, doc etc.
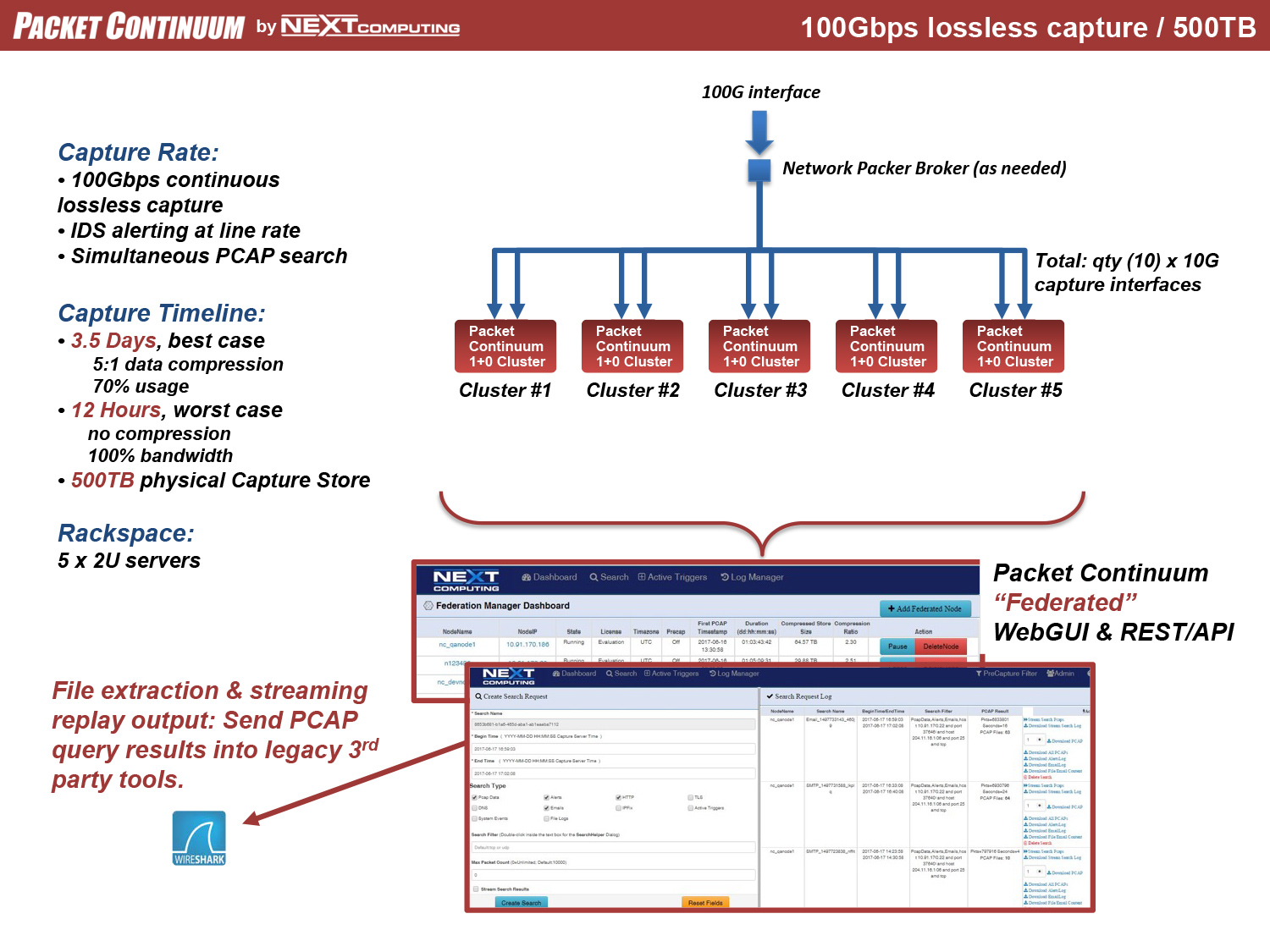
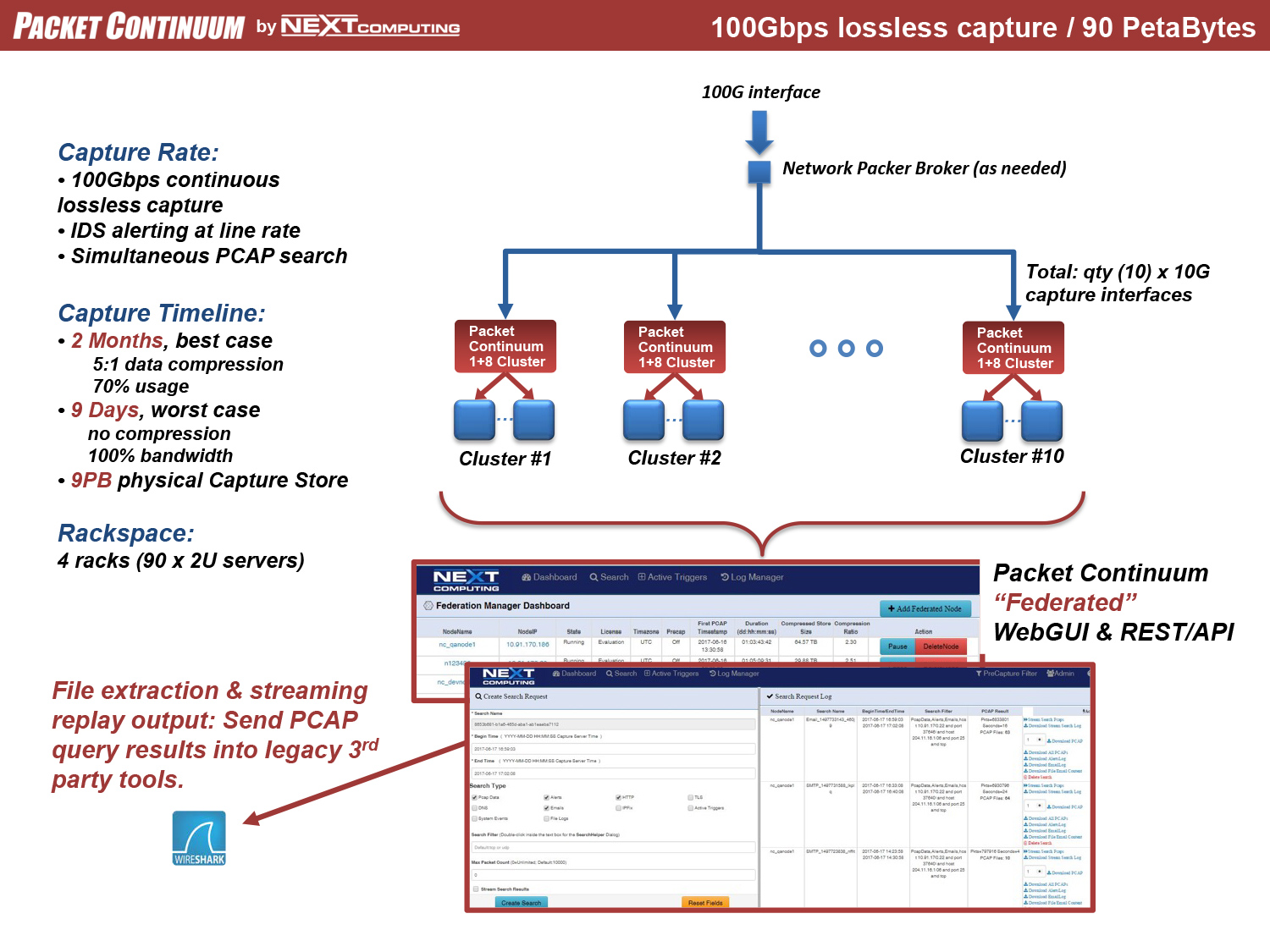
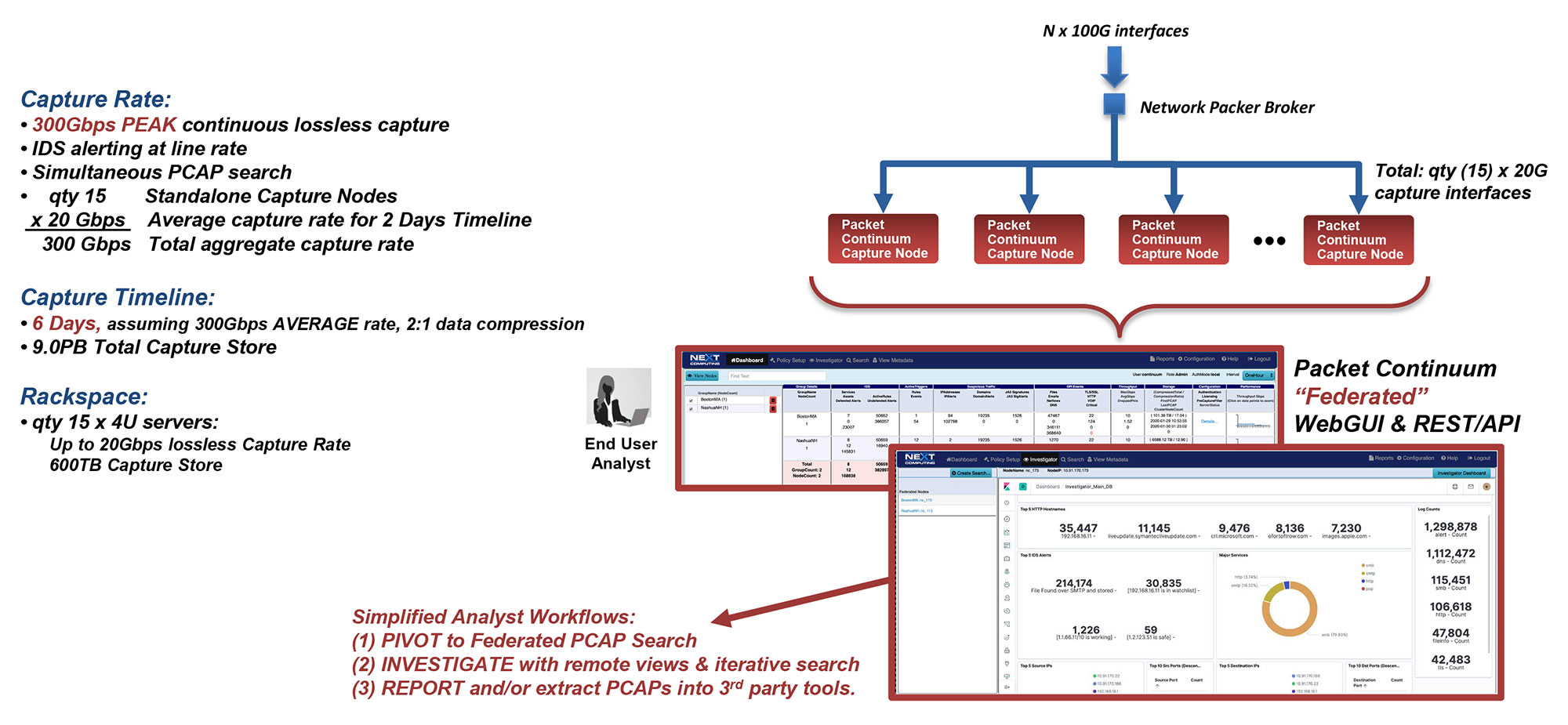
SMOOTH SCALE TO 100GBPS LOSSLESS PCAP
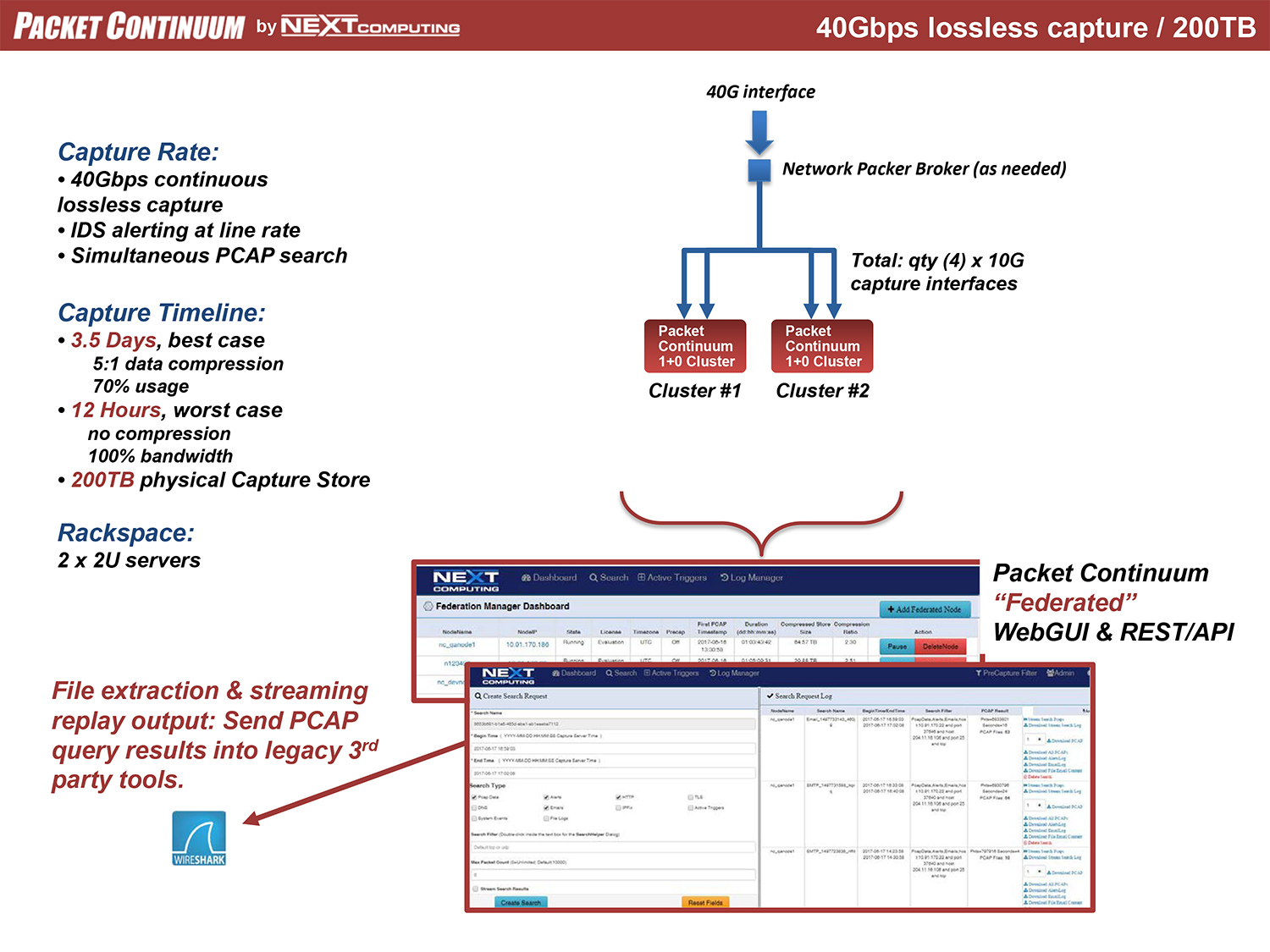
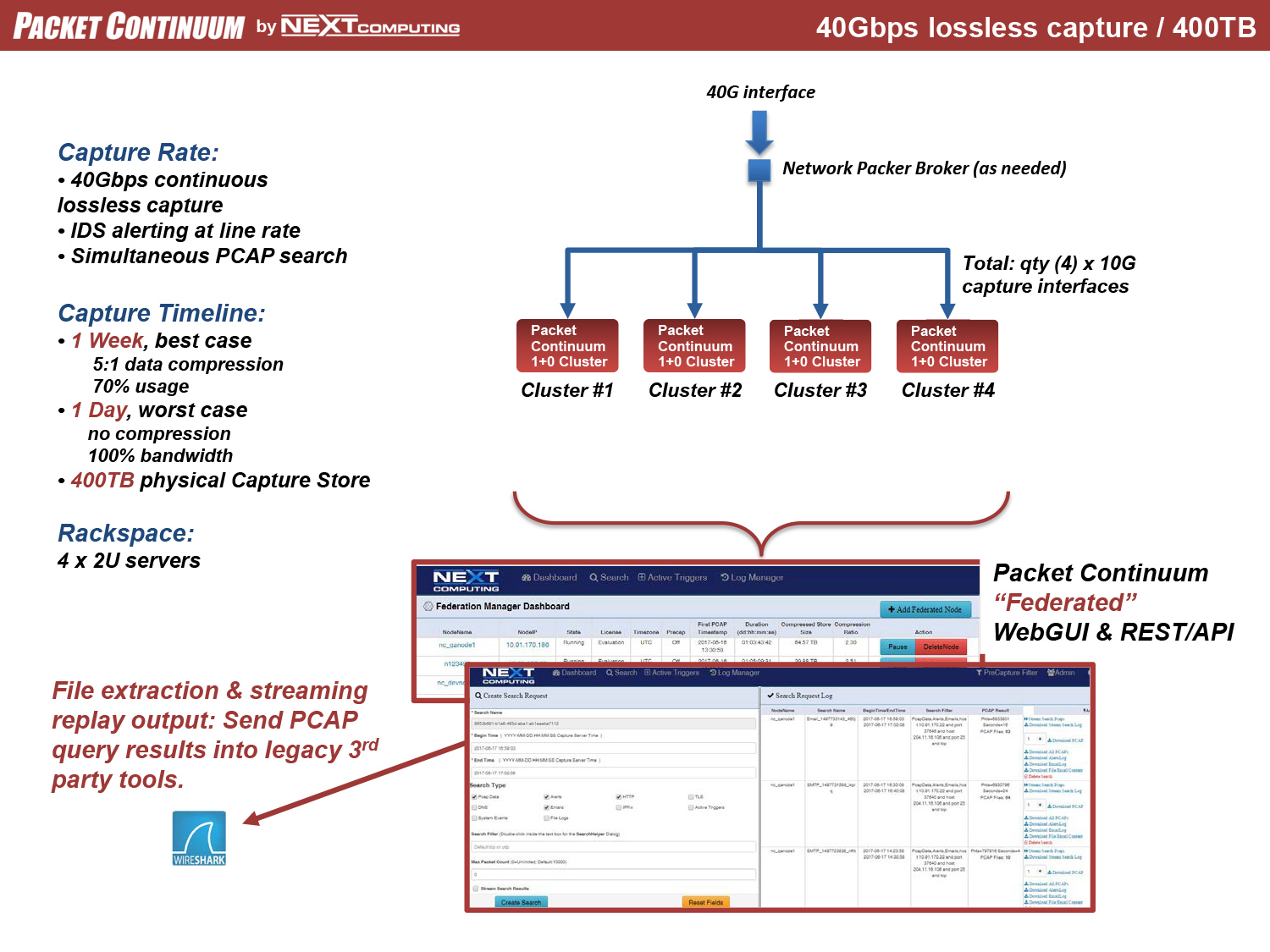
Packet Continuum MapReduce Architecture uses Capture Nodes and Cluster Nodes as the building blocks of massive scale. The following diagrams illustrate how to use Federation Manager for continuous lossless packet capture of 40Gbps and 100Gbps and even higher rates– including real-time IDS alerting (Snort/Suricata) running at line rate, together with other packet analytics and Policy Management functions. Each configuration uses the same core appliance as a "Node": a Dell R730 enterprise-class server with 100TB storage specifically allocated for capture timeline, net of other storage requirements.
40Gbps Example Configurations
100Gbps Example Configurations
Fast Query / Streaming
- Fast, Streamed Query Results
- Every query has the option to return PCAP files, NetFlow records, and/or any log files.
- All results are streamed in “chunks”, allowing partial results to be analyzed while the remaining query is completed, the first of which appear almost immediately after the query initiates.
- Historical “look-back” queries based on standard Berkeley Packet Filter (BPF) within a time period.
- Active Trigger “look-forward” alerts, BPF-based and user-defined, can generate dozens of simultaneous alerts when the target condition occurs.
- Pre-capture filters (BPF-based) can be changed on-the-fly during capture operations
- All historical logs searchable by text string
- Real-time indexing
- Every packet gets a timestamp and correlation index
- Every log & alert event is cross-correlated to PCAPs and IPIX flow records
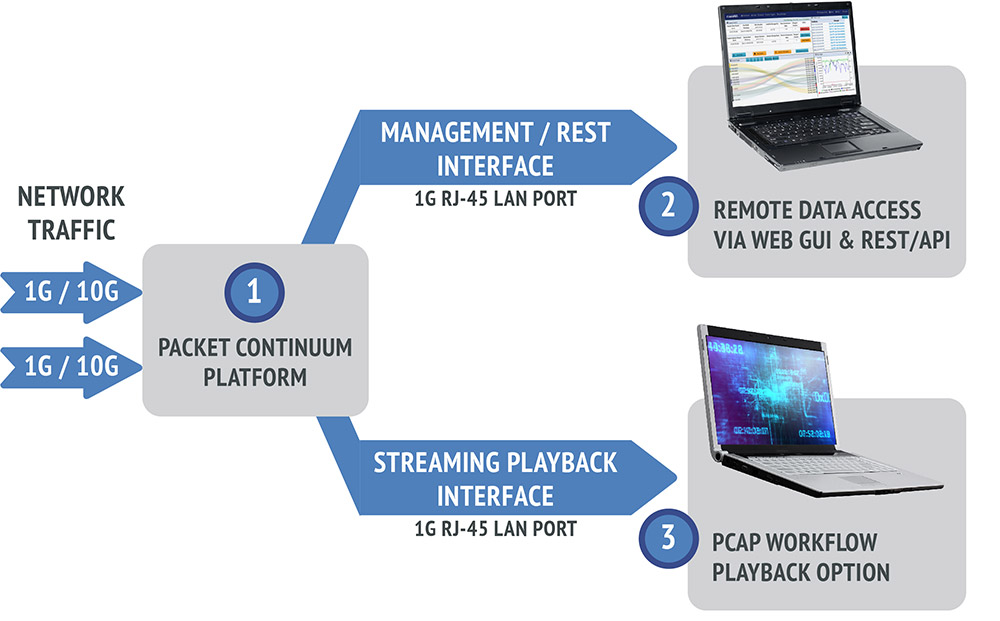
- Streaming Playback Feature
- PCAPs that have been searched/filtered/extracted with the Packet Continuum UI may be regenerated out a 1G copper RJ45 interface to an external device
- Compatible with ANY 3rd party capture/analysis tool - just like a span/mirror port.
Great for recording, additional packet/signature analysis, or back-testing new firewall policies against real historical traffic.
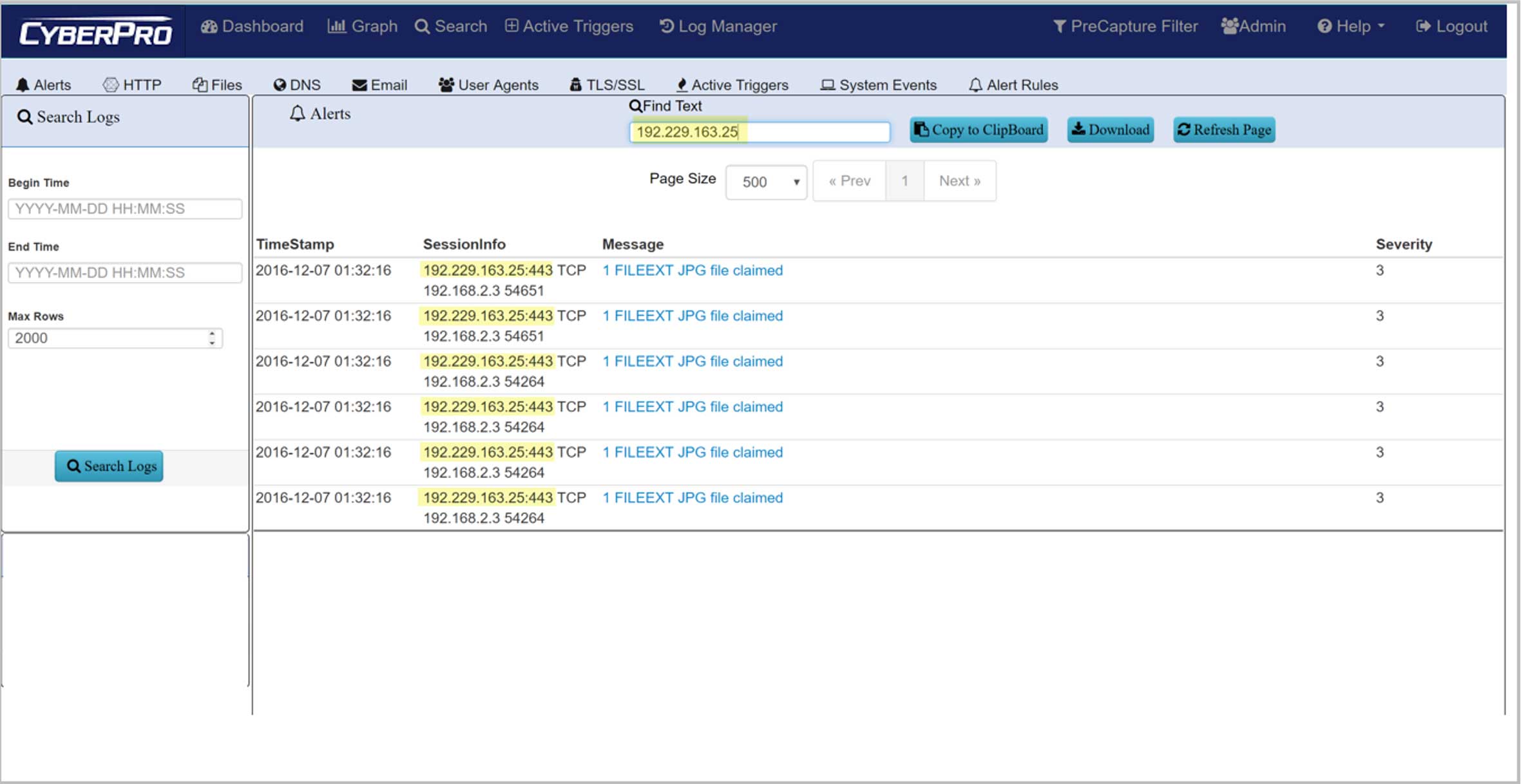
Threat-IP Detection
Packet Continuum enables identification, monitoring, viewing, and mitigation of pre-defined Threat IPs as well as user-defined IPs. Packet Continuum comes pre-loaded with a known list of Threat IPs; a number of malicious IPs previously identified by trusted sources such as US-CERT, for your protection.
From the Packet Continuum Log Investigator or Sankey Graph, users can:
- Upload/enable, view or delete/disable lists of identified Threat IPs
- Set alerts based on identified Threat IPs
- Create Active Defense actions (via user criteria or Suricata rules) to be taken when a Threat IP is identified
- With one click, view detailed PCAP session information where a threat is identified
When a Threat IP is identified as present in a session, the system generates a severe alert and a pre-defined Active Defense action can be executed or, if one is not available, alert info can be sent to an external server.
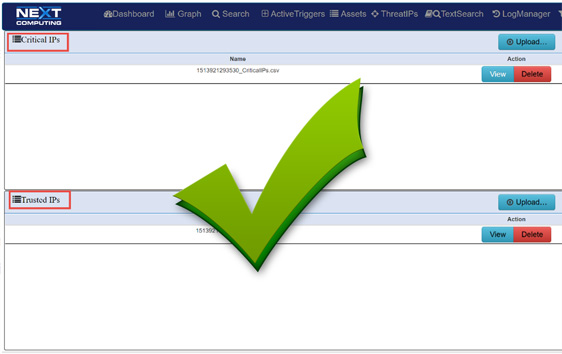
Defended Assets & Services
Packet Continuum enables identification, monitoring, viewing and automatic approval of Defended Assets, which consist of Critical IPs (essential infrastructure) as well as Trusted Asset IPs (host IP addresses defined as safe). Similarly, Defended Services for each critical network application/protocol are defined by port #.
Using the Packet Continuum Dashboard and Threat Hunting / Log Investigator, users can:
- Upload, view or delete lists of identified Assets and Services
- Set alerts based on identified assets or services
- Monitor / view sessions containing specified assets/services as the source or destination
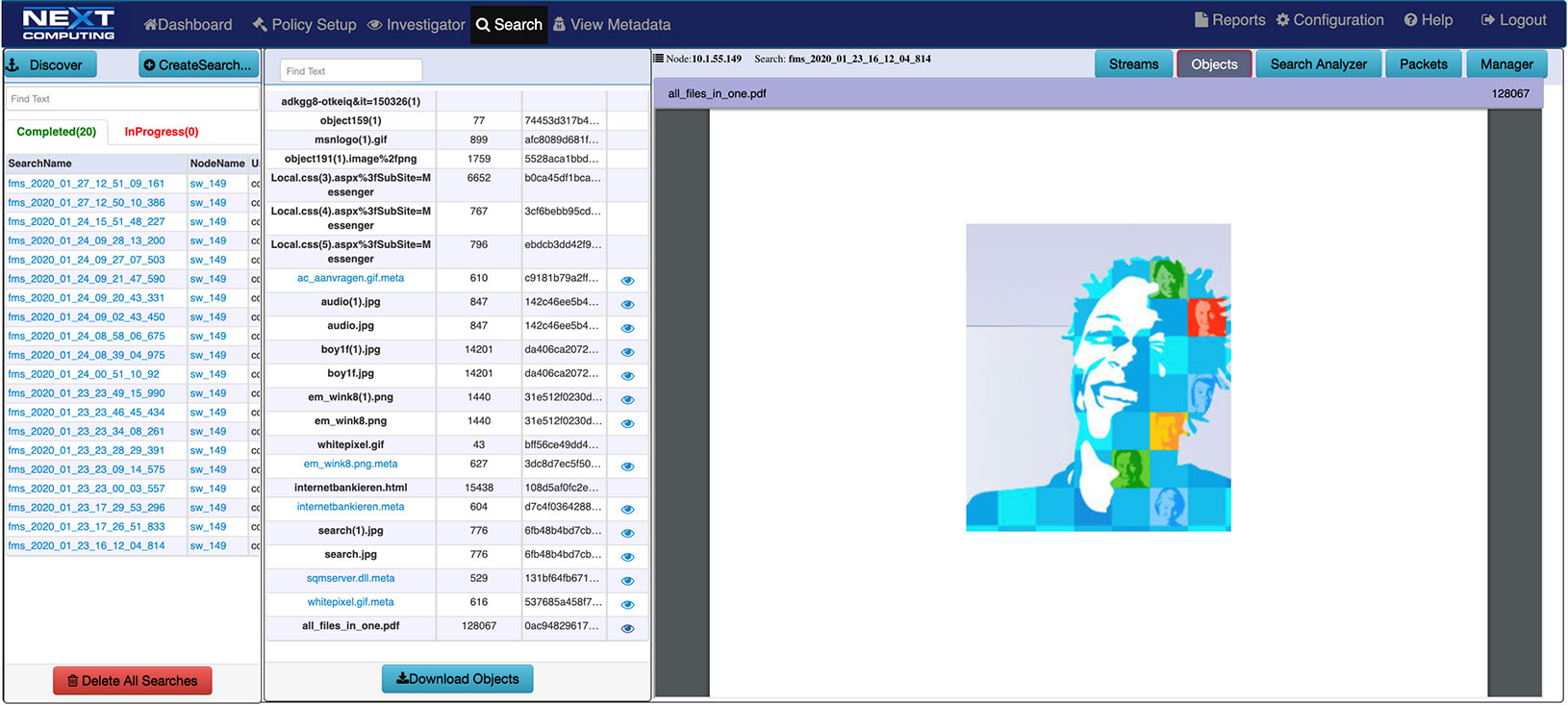
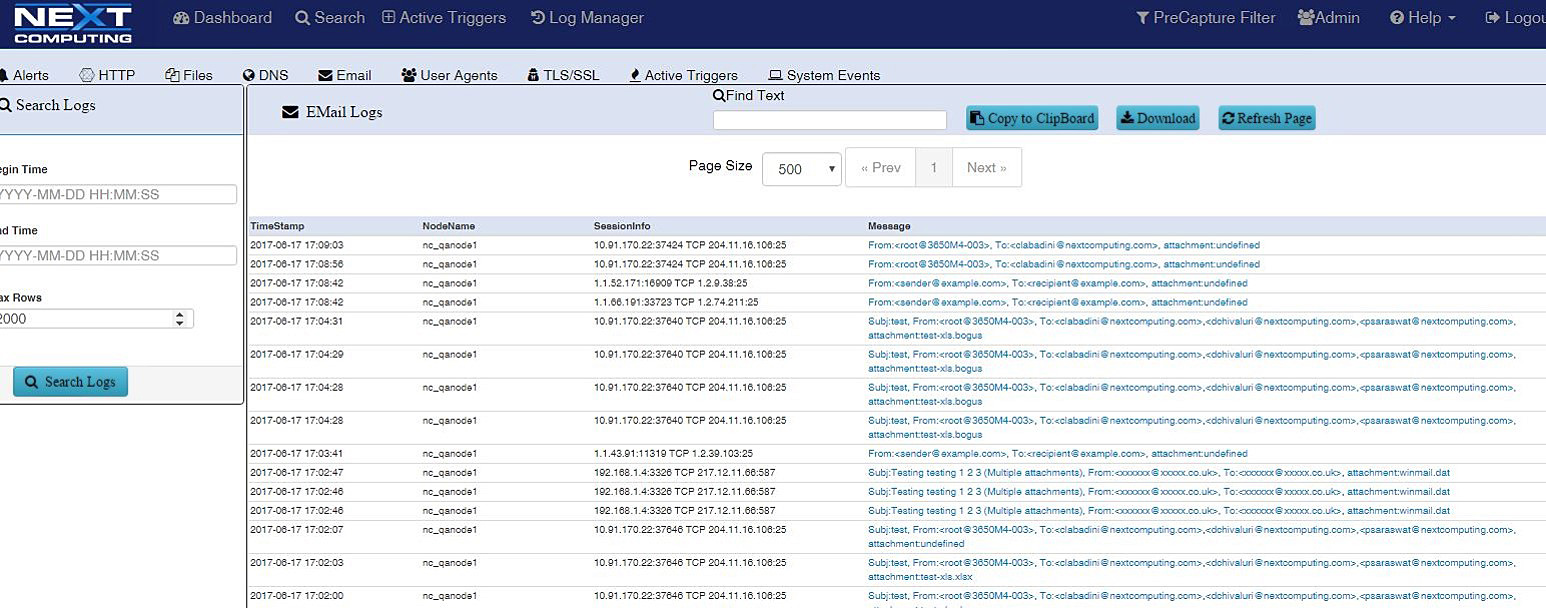
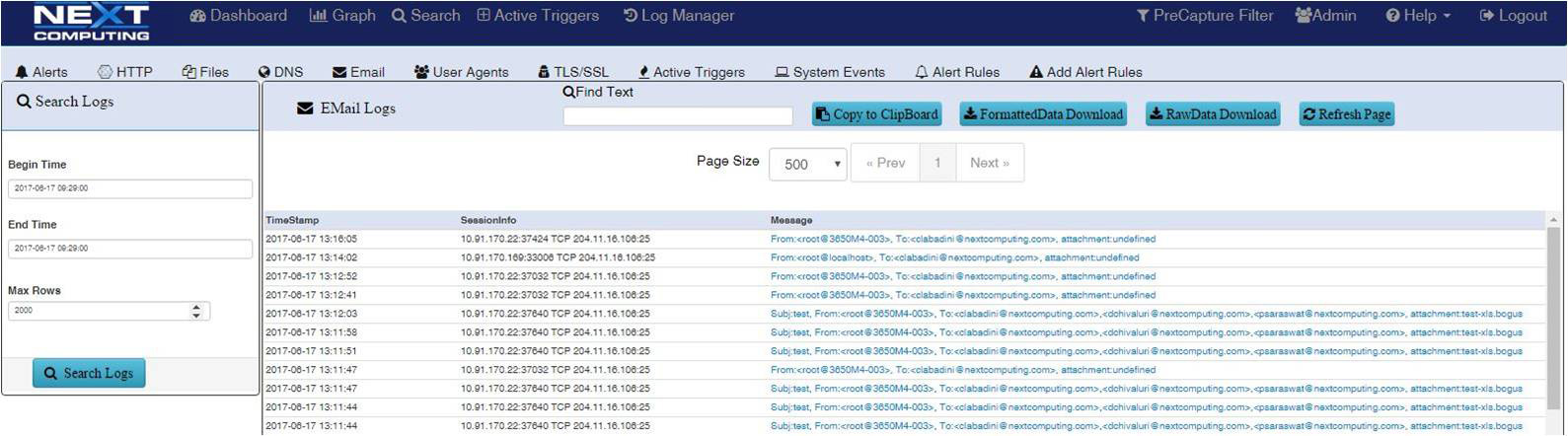
Email Search / Extraction
Identify and search email strings and subjects. Email extraction feature includes sender, receiver, subject line and text reconstruction.
- SMTP email session logging with body text in HTMP format and file attachment reconstruction from original Mime format
- SMTP subject, send and receive email address logging
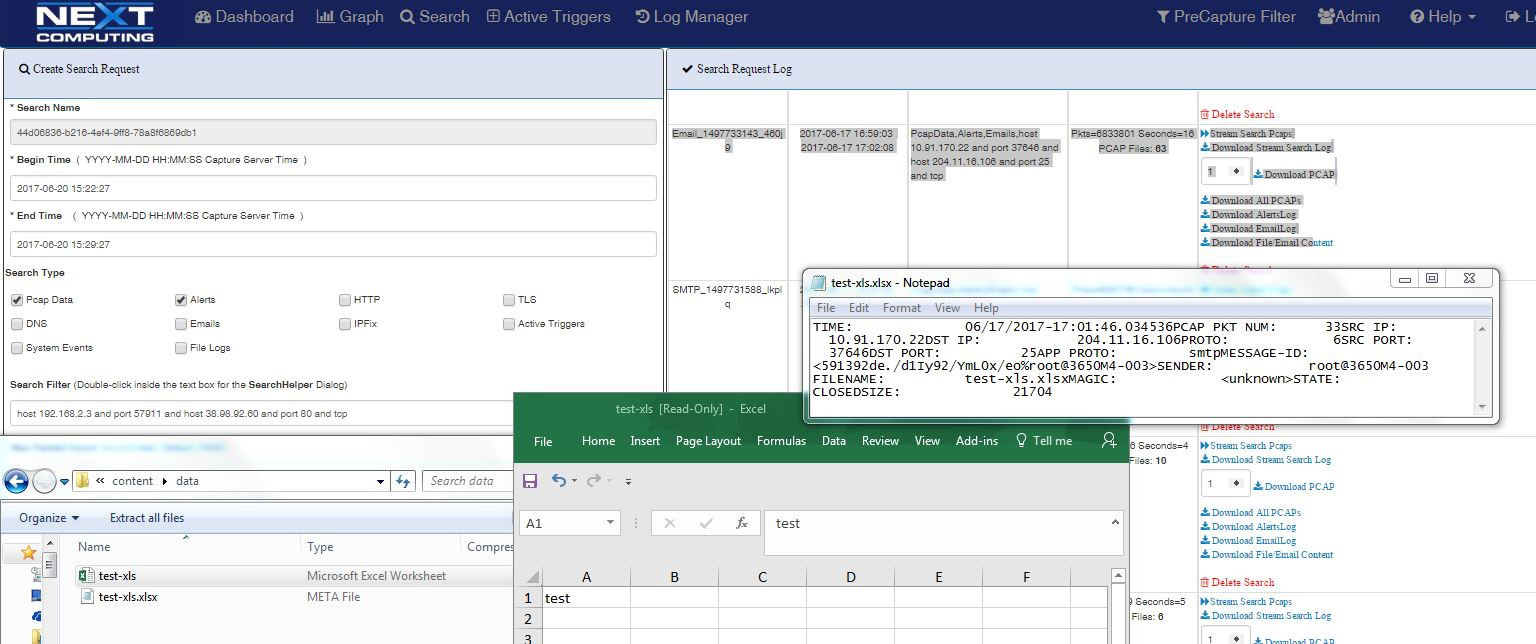
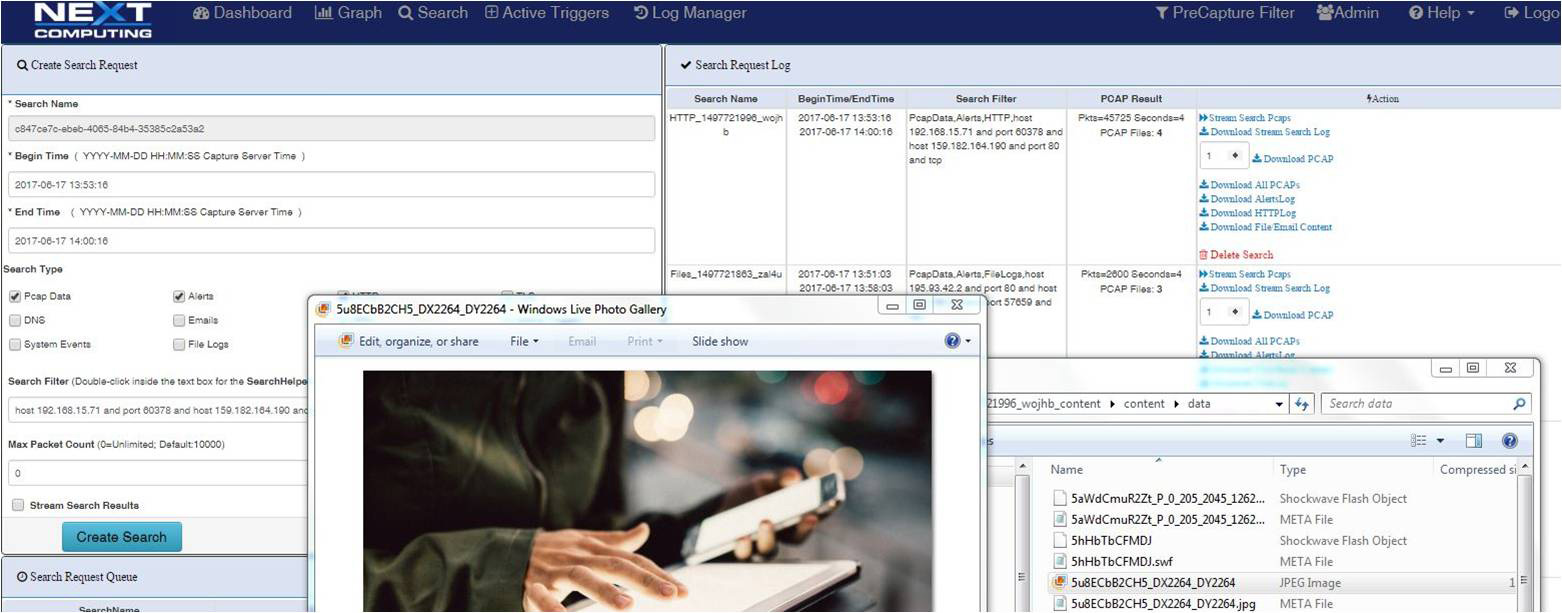
Log Investigator email tab showing SMTP email session extraction and reconstruction of email attachment as Excel file with original content and metadata file
Packet Continuum simplifies the email session logging process with pivot to sessionized search and file recovery.
- Free form text search capability
- Clickable by event
- Second click initiates packet session recovery and file reconstruction
- Just two more clicks to the reconstructed file and meta data for that HTTP or SMTP email session
- All viewable and downloadable
List of SMTP emails sessions searchable with time stamp, capture node location, session information, and SMTP email address, sender / receiver. A user can click to get the full session packets, extract email subject / text and reconstruct file attachments in original mime format, PDF, doc, etc.
File Leakage / Exfiltration
Packet Continuum enables
- HTTP, email and file transfer session logging and file identification
- Identification and reconstruction of files and associated metadata in original mime type for viewing and analysis
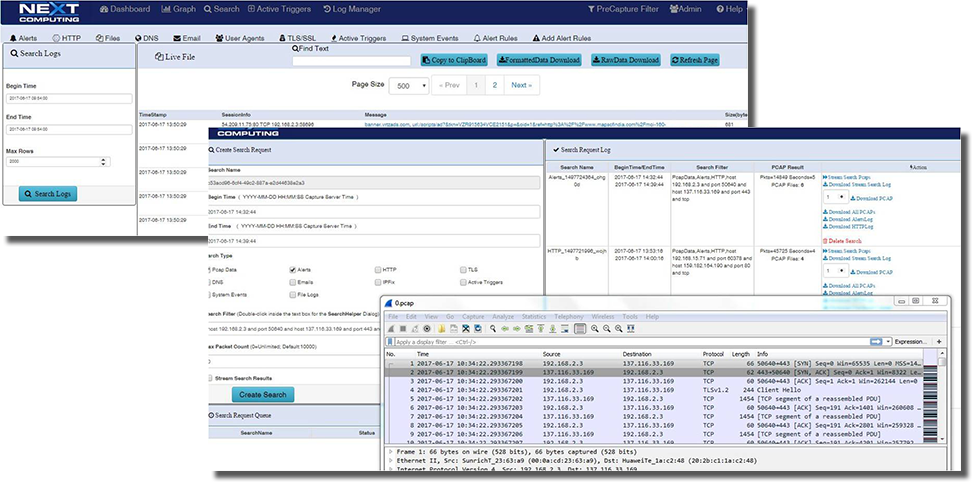
File Leakage Session showing logs and pivot to session search and file reconstruction with metadata
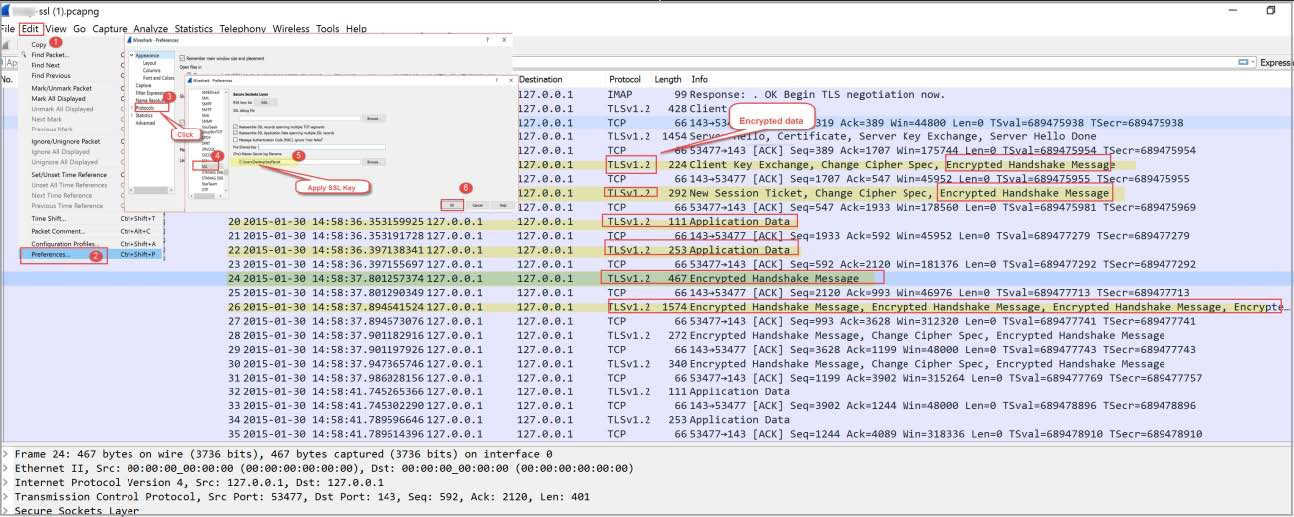
TLS / SSL Visibility
Gain visibility into TLS / SSL encrypted sessions. Log and extract sessionized PCAP data via timestamp, capture node and session information for recovery of sessionized packets, then offload them to WireShark using customer provided keys.
Open Data interfaces
Packet Continuum's open interface enables use of 3rd party commercial and open source tools from SIEM for additional cyber analytics.
- Open file formats and data viewers
- Standard PCAP-NG file and NetFlow record extractions viewable in WireShark or TShark
- Log files and alerts viewable as CSV or text files in any compatible application such as MS Office.
- Remote Access to file extractions with Web GUI
- PCAP playback feature for 3rd party tools
Open REST/API for creating custom workflows to automate Incident Response, Policy-driven data retention, or interface to legacy analytics tools.
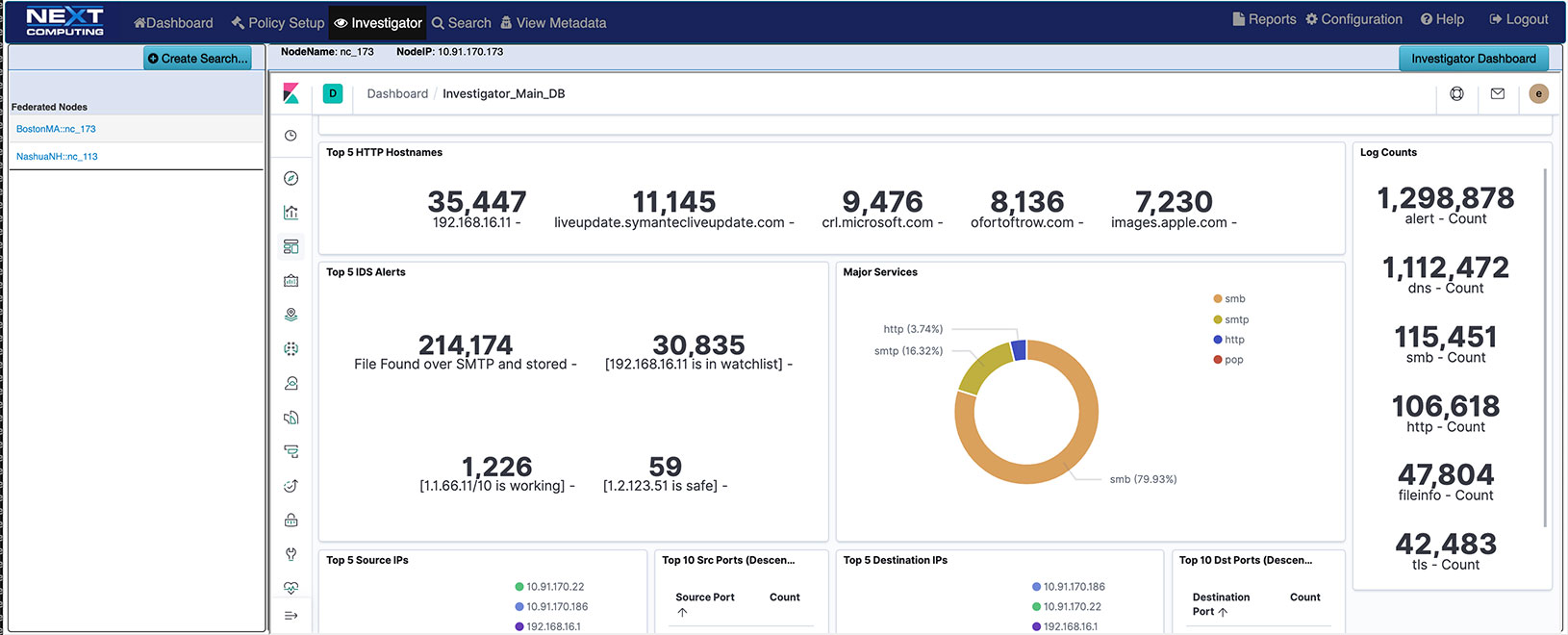
Web UI & REST API
- Packet Continuum dashboard integrates policy-driven IoC events for rapid triage decisions and simplified workflows.
- One-click searches directly from Dashboard areas: Events Summary, Capture Data Graph or Critical Alerts. Searches auto-populate with the query request per user context, simplifying the process of finding and viewing critical events and associated PCAP files
- Packet Continuum has remote viewers for sessions, packets, IoC events, and even previews for detected files. Data can be viewed without external tools or downloading to the local system. Besides viewing, user also has the capability to create more concentrated and focused searches from the view data available.
- Comprehensive Threat Hunting / Log Investigator screen with tabs for each IoC policy type, allowing instant search and correlation with PCAP and NetFlow V9 flow records
- Remote access to manage and control multiple devices including hot-accessible cluster node changes
- Control of multiple clusters in a global-dispersed federation of capture systems
Massively Scalable
Packet Continuum deploys on a wide range of rackmount and desktop common hardware platforms, from cost-effective sensor/recorders to enterprise-class servers. It is uniquely cost-effective when deployed at scale. Examples of how packet Continuum can scale include:
- Numerous distributed sensor/recorders within a highly-scalable “Federated” network architecture, for close coordination with a central Security / Network Operations Center.
- Long capture timelines for days, weeks, or months of lossless packet capture data history, when quick-response search is required. Added timeline features include in-line data compression and policy-driven data retention.
- High capture rate capture points (eg. 40Gbps, 100Gbps, and beyond) where a full feature set of real-time analytics functions must run at line rate with deterministic performance: Continuous lossless full packet capture (PCAP), real-time IDS alerting and other user-defined Policy Management, with simultaneous search/recall for Incident Response.
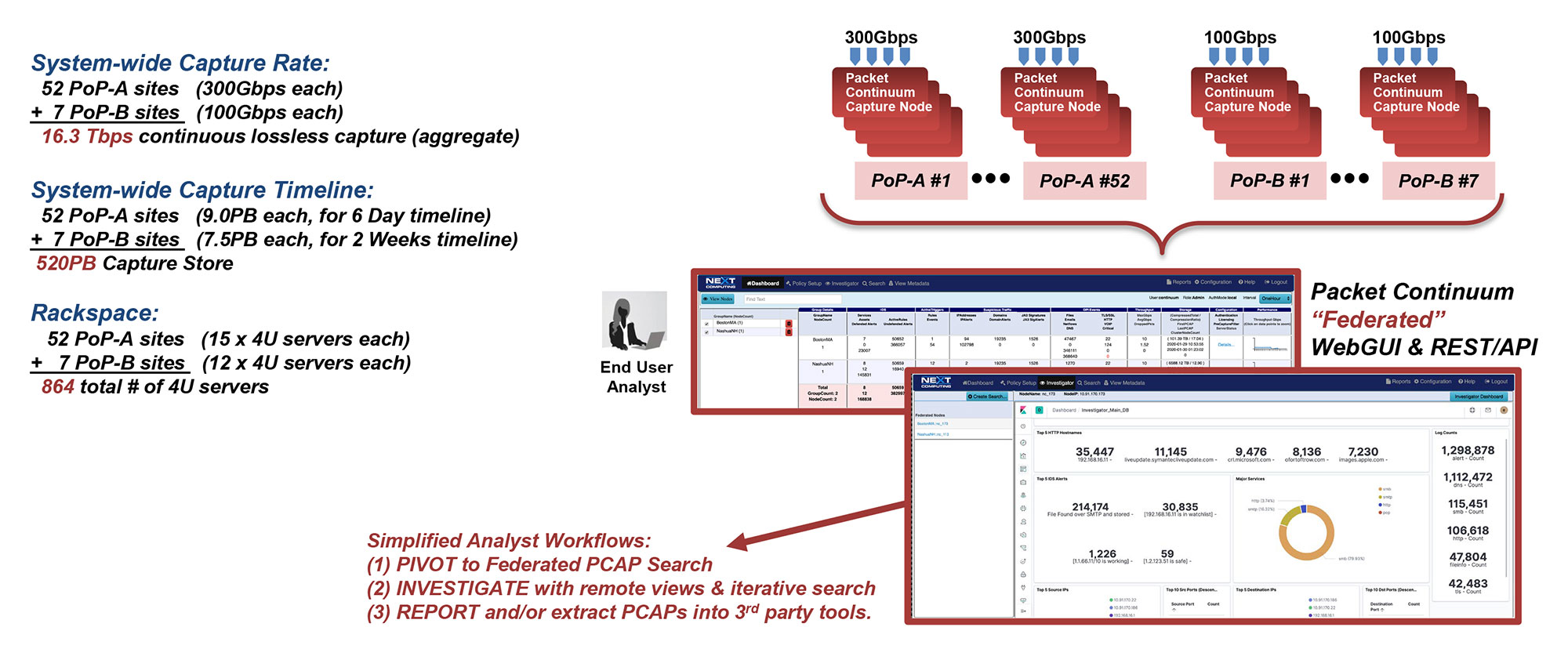
Telco Example: 60 Federated Internet PoP Sites
Click to enlarge
Telco Example: 300Gbps for 6 Days required per PoP Site
Click to enlarge
Packet Continuum is disrupting the market with open data access, smooth scale, and long timelines – at very low cost.
As an “Open PCAP Infrastructure”, the Packet Continuum supports even the largest enterprise-scale users. Lossless packet capture is the immutable ground truth of any critical event – not merely an interpretation. Take direct ownership of your own critical network data resource.
Infrastructure Services
Packet Continuum includes comprehensive support services for long-term management of large numbers of sensors in the field. This is particularly valuable for Service Providers who can focus on optimizing their yber analytics and SOC procedures, while NextComputing manages a wide variety of hardware sensors, all with an identical software stack capable of field upgrades. The range of services includes:
- Flexible Pricing, including hardware financing and software subscription or site licensing
- Optimized Platform Specs
- Based on requirements for Deterministic Real-Time Performance + Low Cost
- OS, BIOS, Memory, CPU Cores, Hyper-Threads, RAID, Storage, Patch/Vulnerability Updates
- Common Architecture Flexibility
- Customer-branded hardware & UI software
- Customization / Integration
- Software, Hardware, Cabling, Documentation, Packaging
- Application Support
- Example: Legacy Transition Support
- Configuration Management & Revision Control
- Sensor Refurbishment, QA, and Regression Testing
- Supply Chain Logistics
- Standards-Based Certification
- Electrical, Vibration, etc
- Long Term Support Commitment
- Tier 1/2/3 disciplined policies for ticket escalation/resolution
- End User Training + Innovative “Train-the-Trainer” techniques