Fill in the Holes of Your CyberSecurity Plan
Cyber theft is the fastest growing crime in the US. Crime damages will cost the world $6 trillion annually by 2021. Cybersecurity spending is expected to exceed $1 trillion by 2021. As the world goes digital, humans have moved ahead of machines as the top target for cyber criminals. Today’s hackers smell blood, not silicon.
Top targeted industries include healthcare, IT, energy, communications, critical manufacturing and more recently, family offices.
Across the board, breaches that took months or longer to detect largely fall into categories like cyber espionage, point-of-sale-intrusions and privilege misuse.
Packet Continuum software and deployable cybersecurity platforms have disrupted the market with open data access, smooth scale, and long timelines at a very low cost. Real time visibility and forensic insight into your critical network data resources is realized for small to large scale configurations.
NextComputing proudly announces a set of NEW features that further enable uncovering the immutable ground truth of any critical event, not merely an interpretation. Packet Continuum is compatible with third party commercial and open source tools providing you with a complete Cybersecurity protocol.
Some of these new features include:
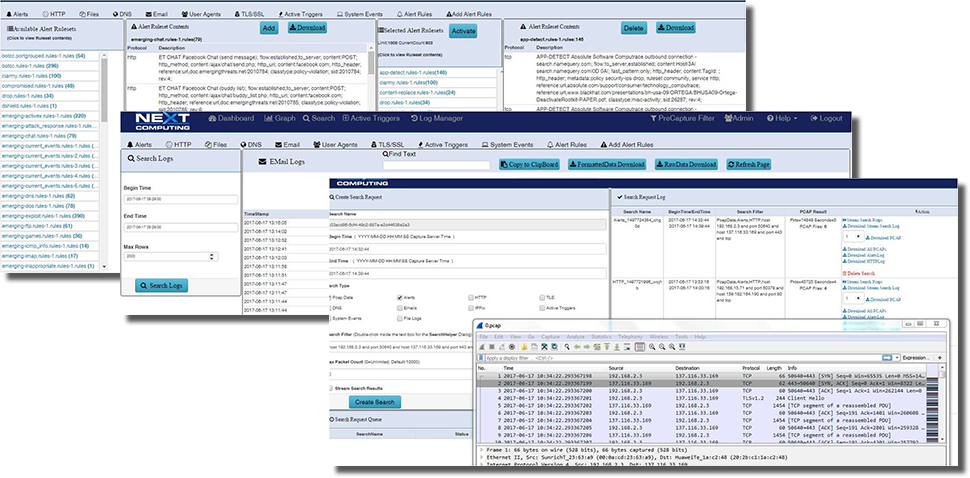
 Behavior / Signature Visibility and Logging
Behavior / Signature Visibility and Logging
- The IDS Alert configurator and DPI Analyzer enable multi-level signature and behavior event session search and logging, allowing groupings of alerts dynamically from a grouping of 30,000.
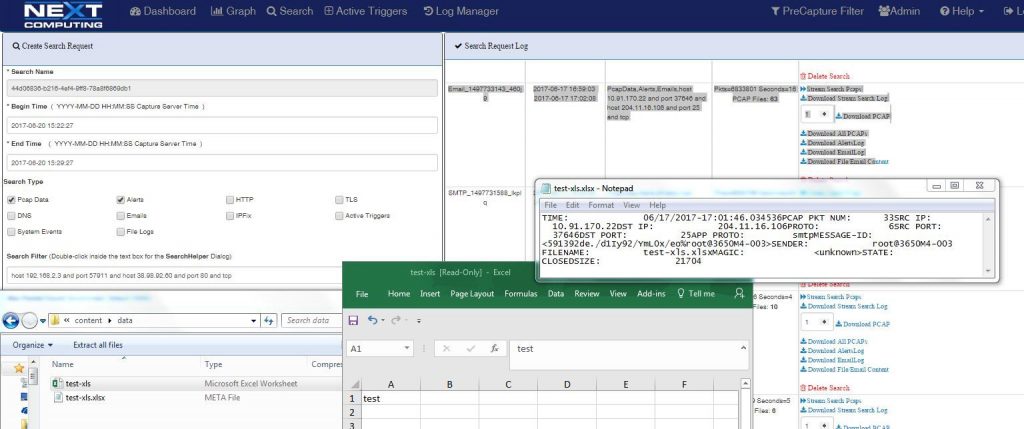
 Email Search / Extraction
Email Search / Extraction
- SMTP email session including subject, send and receive email and body text in HTMP format.
- File attachment reconstruction from original mime format.
 File Leakage / Exfiltration
File Leakage / Exfiltration
- HTTP, email and file transfer session logging, identification and reconstruction of files and associated metadata in original mime type for viewing and analysis.
 TLS / SSL Visibility
TLS / SSL Visibility
- Log and extract PCAP data from encrypted TLS / SSL sessions for recovery of sessionized packets
- Offloadable to WireShark
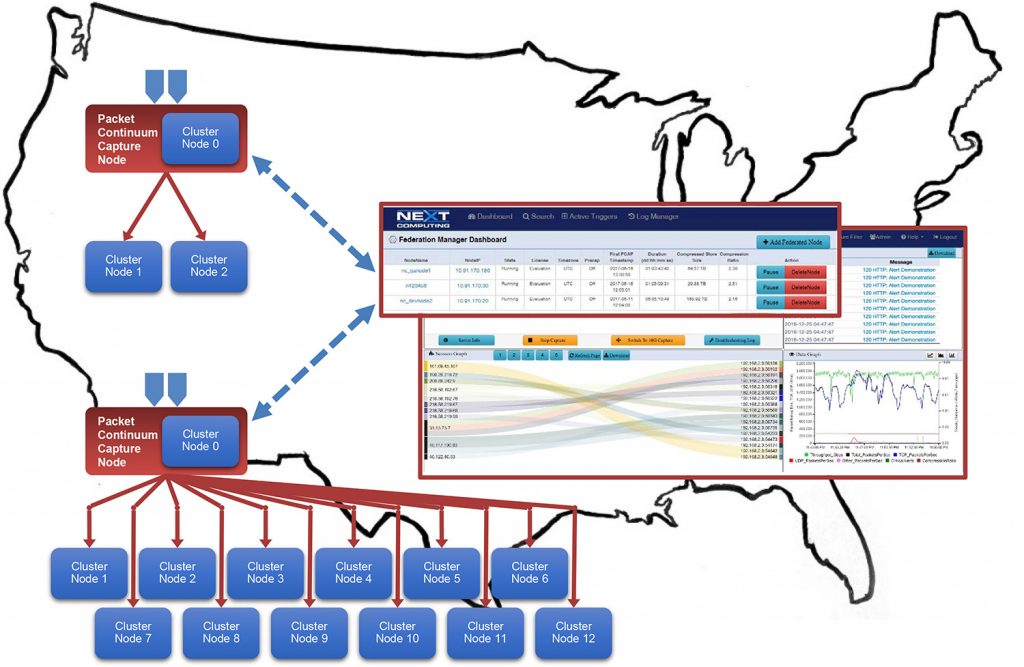
 Federation Manager
Federation Manager
- Federate multiple capture appliances in multiple locations.
- Remote control via browser and REST API
- Federate View of all data
- Map-reduced framework to extract out packets, DPI data and logs across federation
Click here for a downloadable datasheet to share (PDF).
For more information, contact us at sales@nextcomputing.com
Investigate. Fingerprint. Eliminate.