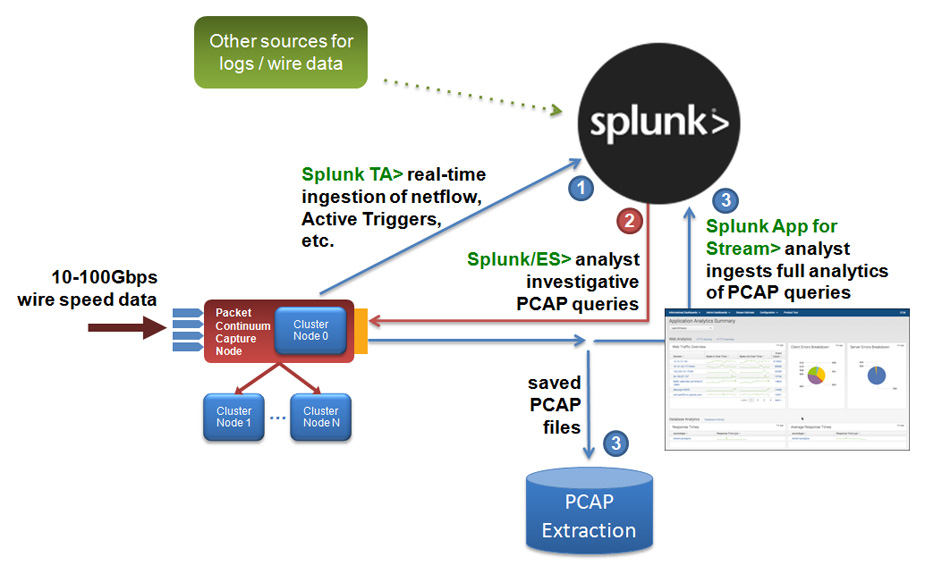
Packet Continuum offers packet capture at a flexible scale to meet the needs of any organization. As part of a complete capture workflow, data passing through a SIEM (Security Information and Event Management) tool such as Splunk for analysis and automated response is then pivoted to Packet Continuum for storage of data packets and metadata for further analysis.
Enriched metadata augments PCAP forensic investigations in several ways:
- IDS alerts (50K active Suricata rulesets)
- Suspicious traffic alerts (1M active ThreatIPs, domains, malware, JA3 signatures)
- Selective file-carving (eg. extract suspect files into workflows)
- Active trigger alerts (BPF-based alerts)
- General logs (Netflow+ DPI events)
The result is high-speed system allowing remote PCAP views and iterative search of alerts and incidents.
- Follow streams & suspicious augmentation alerts
- Remote view / analyze packets & preview objects / files
- Extract PCAPs & generate reports
